Custom Security Groups in OpenStack and AWS Clouds
Overview
By default, the Avi Controller creates and manages a single security group (SG) for an Avi Service Engine. This SG manages the ingress/egress rules for the SE’s management- and data-plane traffic. In certain customer environments, it may be required to provide custom SGs to be also be associated with the Avi SEs’ management- and/or data-plane vNICs. This article shows how to use the Avi SE group’s custom_securitygroups_mgmt and custom_securitygroups_data configuration flags to achieve this extra flexibility in OpenStack and AWS clouds, via the Avi UI and Avi CLI.
OpenStack Cloud
Without any Custom Security Group Configuration
[root@sivacos ~(keystone_admin)]# nova show a2354abc-0455-440b-ac0b-0b0e50bc66d2
+-----------------------+------------------------------------------------------------------------------------------------------------+
| Property | Value |
+-----------------------+------------------------------------------------------------------------------------------------------------+
...
| avimgmt network | 172.24.16.4 |
| description | Avi-se-pyhlh |
| id | a2354abc-0455-440b-ac0b-0b0e50bc66d2 |
| image | Avi-SE-17.1.4-9000-cloud-15190a62-e284-4033-8800-70c27c452bad-cluster-143b2840-19b6-409d-918d-d92edc98b2e1 |
| metadata | {"AVICNTRL": "10.10.22.44", ..."AVISG_UUID": "bccf43ca-e98d-483b-9bff-43ab5e8970f3", ...} |
| name | Avi-se-pyhlh |
| private network | 10.0.0.10 |
| security_groups | avi-se-a2354abc-0455-440b-ac0b-0b0e50bc66d2 |
| status | ACTIVE |
| tenant_id | a6d878c0f7db40bf91ed1226e720460a |
| xfrontend network | 192.168.10.13 |
+-----------------------+------------------------------------------------------------------------------------------------------------+
[root@sivacos ~(keystone_admin)]# neutron port-show 9427350d-31d9-42d2-a2e5-53bef1e52475
+-----------------------+--------------------------------------------------------------------------------------------------+
| Field | Value |
+-----------------------+--------------------------------------------------------------------------------------------------+
| device_id | a2354abc-0455-440b-ac0b-0b0e50bc66d2 |
| device_owner | compute:None |
| fixed_ips | {"subnet_id": "a178c1f1-5cce-4f0a-ac1a-8277e26b085e", "ip_address": "172.24.16.4"} |
| id | 9427350d-31d9-42d2-a2e5-53bef1e52475 |
| mac_address | fa:16:3e:1d:ba:21 |
| name | Avi-Mgmt:cluster-143b2840-19b6-409d-918d-d92edc98b2e1:cloud-15190a62-e284-4033-8800-70c27c452bad |
| network_id | 27bd1f64-5a50-4189-98db-3265809ac71a |
| security_groups | bccf43ca-e98d-483b-9bff-43ab5e8970f3 |
| status | ACTIVE |
| tenant_id | a6d878c0f7db40bf91ed1226e720460a |
...
+-----------------------+--------------------------------------------------------------------------------------------------+
[root@sivacos ~(keystone_admin)]# neutron port-show 747d4110-c4d2-443e-8ee0-373702b4f4ec
+-----------------------+--------------------------------------------------------------------------------------------------+
| Field | Value |
+-----------------------+--------------------------------------------------------------------------------------------------+
| device_id | a2354abc-0455-440b-ac0b-0b0e50bc66d2 |
| device_owner | compute:None |
| fixed_ips | {"subnet_id": "4e010951-eb90-43af-9bad-e578f1ac2f77", "ip_address": "10.0.0.10"} |
| id | 747d4110-c4d2-443e-8ee0-373702b4f4ec |
| mac_address | fa:16:3e:fa:bd:ec |
| name | Avi-Data:cluster-143b2840-19b6-409d-918d-d92edc98b2e1:cloud-15190a62-e284-4033-8800-70c27c452bad |
| network_id | a6669299-dccb-40a9-a0d2-4608aaea79c0 |
| security_groups | bccf43ca-e98d-483b-9bff-43ab5e8970f3 |
| status | ACTIVE |
| tenant_id | a6d878c0f7db40bf91ed1226e720460a |
...
+-----------------------+--------------------------------------------------------------------------------------------------+
[root@sivacos ~(keystone_admin)]# neutron port-show 16414cce-7eaf-4d58-bdb5-fa8169a4a8e2
+-----------------------+--------------------------------------------------------------------------------------------------+
| Field | Value |
+-----------------------+--------------------------------------------------------------------------------------------------+
| device_id | a2354abc-0455-440b-ac0b-0b0e50bc66d2 |
| device_owner | compute:None |
| fixed_ips | {"subnet_id": "5b0d022b-33a2-42d9-873b-814ac2726e13", "ip_address": "192.168.10.13"} |
| id | 16414cce-7eaf-4d58-bdb5-fa8169a4a8e2 |
| mac_address | fa:16:3e:91:a3:24 |
| name | Avi-Data:cluster-143b2840-19b6-409d-918d-d92edc98b2e1:cloud-15190a62-e284-4033-8800-70c27c452bad |
| network_id | d36521da-8810-457e-95e5-a350143e61a4 |
| security_groups | bccf43ca-e98d-483b-9bff-43ab5e8970f3 |
| status | ACTIVE |
| tenant_id | a6d878c0f7db40bf91ed1226e720460a |
...
+-----------------------+--------------------------------------------------------------------------------------------------+
Custom Security-group Configuration via the Avi CLI
[admin:10-10-22-44]: > configure serviceenginegroup Default-Group
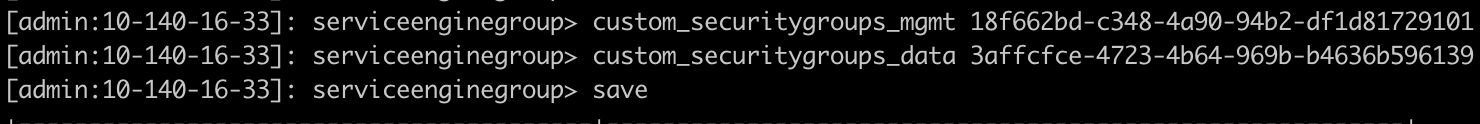
[admin:10-10-22-44]: serviceenginegroup> custom_securitygroups_mgmt 30fe49a4-ee31-43a9-9235-e23d59e392b3
[admin:10-10-22-44]: serviceenginegroup> custom_securitygroups_data 2aba00a7-8b20-45d4-88f3-64b901b9e363
[admin:10-10-22-44]: serviceenginegroup> custom_securitygroups_data adcf99de-46d0-44e2-8f3b-037804f725f0
[admin:10-10-22-44]: serviceenginegroup> save
+---------------------------------------+---------------------------------------------------------+
| Field | Value |
+---------------------------------------+---------------------------------------------------------+
...
| custom_securitygroups_mgmt[1] | 30fe49a4-ee31-43a9-9235-e23d59e392b3 |
| custom_securitygroups_data[1] | 2aba00a7-8b20-45d4-88f3-64b901b9e363 |
| custom_securitygroups_data[2] | adcf99de-46d0-44e2-8f3b-037804f725f0 |
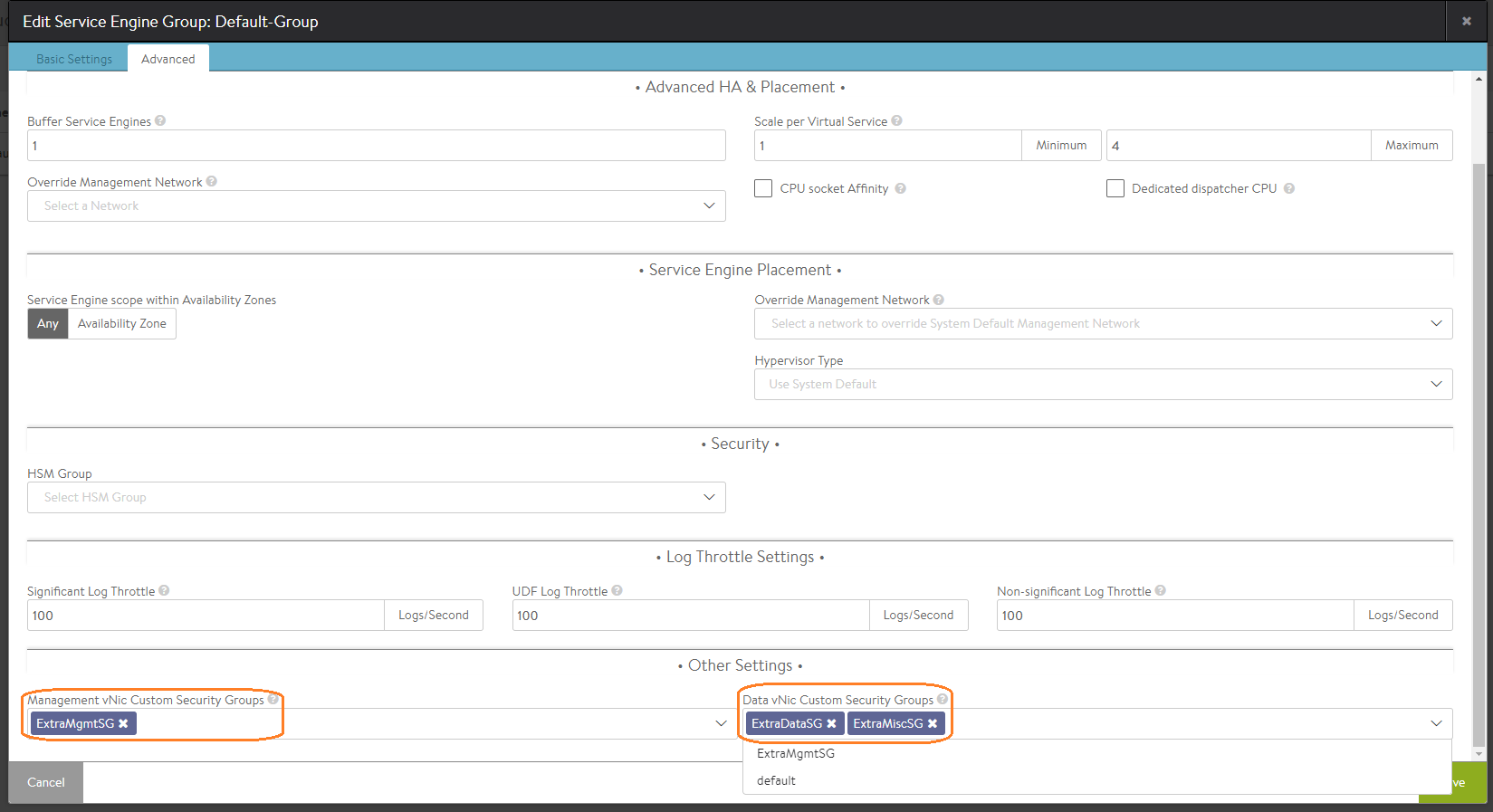
Custom Security-group Configuration via the Avi UI
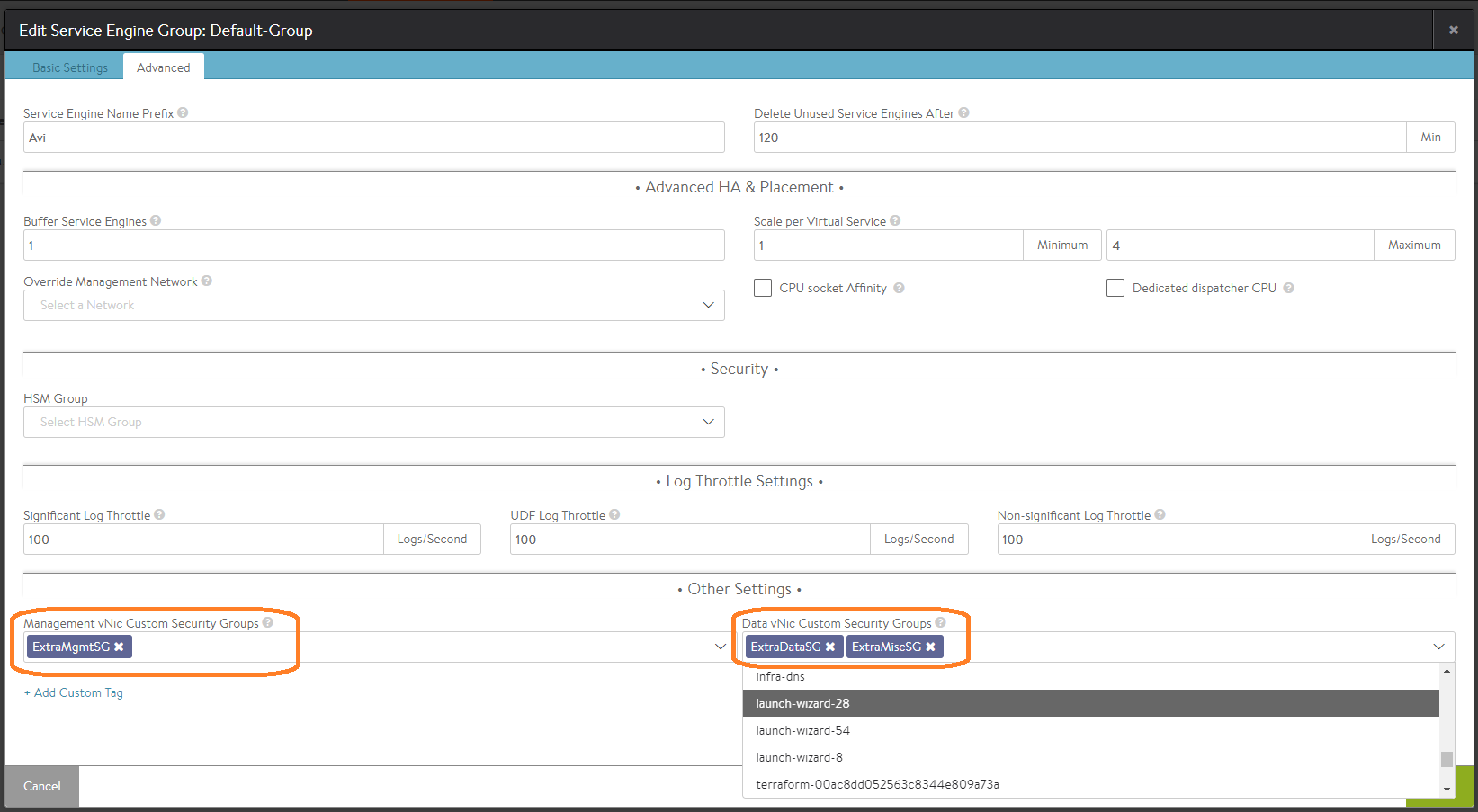
Navigate to Applications > Infrastructure > Service Engine Group and invoke the SE group editor. Select the appropriate named custom security groups for the management vNIC and the data vNIC.
Resulting Custom Security Group Configuration
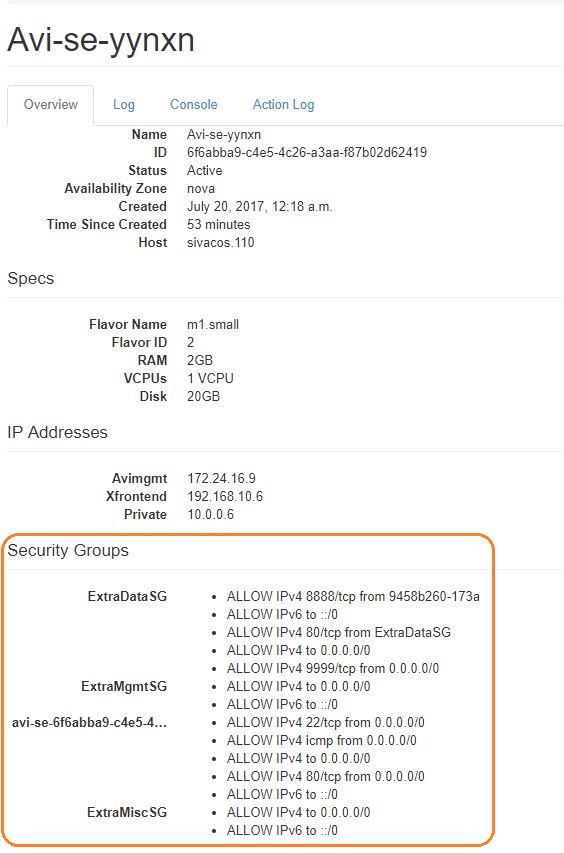
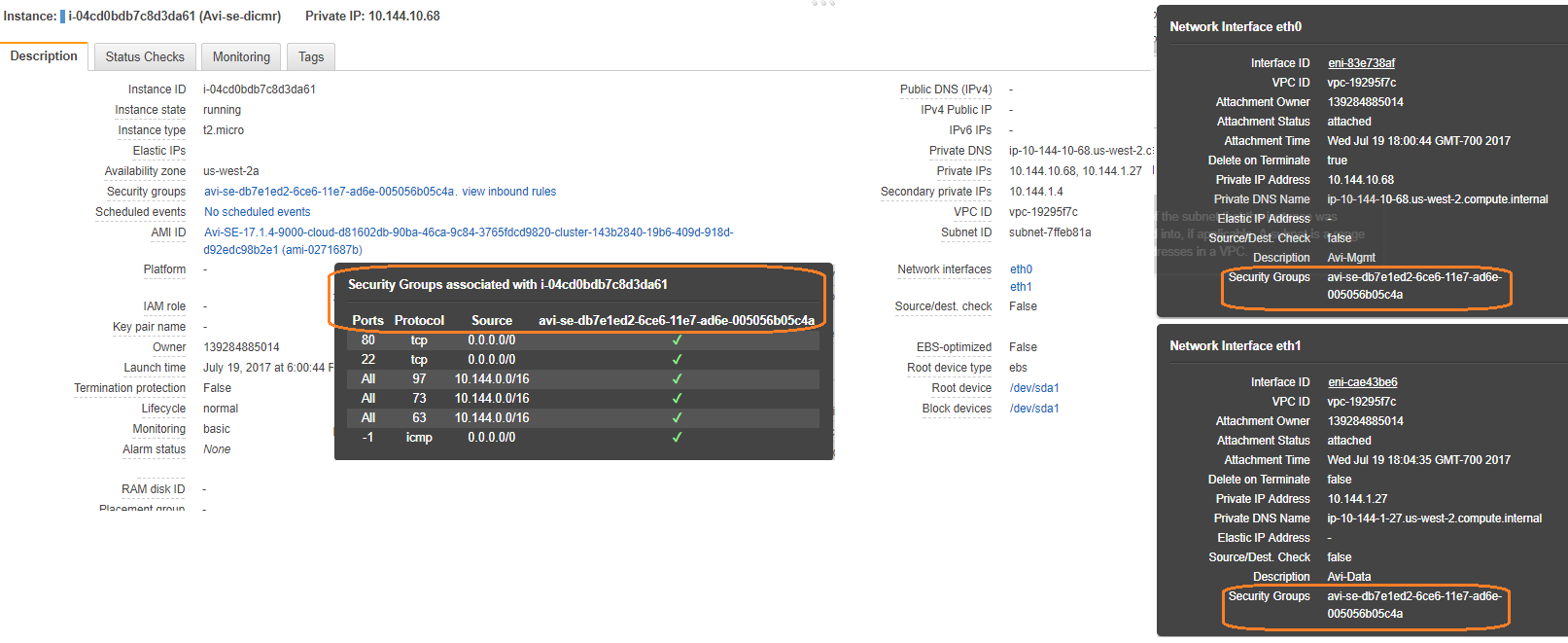
As viewed from the OpenStack UI
As viewed from the OpenStack CLI
[root@sivacos ~(keystone_admin)]# nova show 6f6abba9-c4e5-4c26-a3aa-f87b02d62419
+-----------------------+------------------------------------------------------------------------------------------------------------+
| Property | Value |
+-----------------------+------------------------------------------------------------------------------------------------------------+
...
| avimgmt network | 172.24.16.9 |
| description | Avi-se-yynxn |
| id | 6f6abba9-c4e5-4c26-a3aa-f87b02d62419 |
| image | Avi-SE-17.1.4-9000-cloud-15190a62-e284-4033-8800-70c27c452bad-cluster-143b2840-19b6-409d-918d-d92edc98b2e1 |
| metadata | {"AVICNTRL": "10.10.22.44", "AVISG_UUID": "3d13ee89-5069-4dd2-a505-b6d7032bea9e", ..} |
| name | Avi-se-yynxn |
| private network | 10.0.0.6 |
| security_groups | ExtraDataSG, ExtraMgmtSG, ExtraMiscSG, avi-se-6f6abba9-c4e5-4c26-a3aa-f87b02d62419 |
| status | ACTIVE |
| tenant_id | a6d878c0f7db40bf91ed1226e720460a |
| xfrontend network | 192.168.10.6 |
+-----------------------+------------------------------------------------------------------------------------------------------------+
[root@sivacos ~(keystone_admin)]# neutron port-show 51783401-f174-4240-93df-028564aeb54b
+-----------------------+--------------------------------------------------------------------------------------------------+
| Field | Value |
+-----------------------+--------------------------------------------------------------------------------------------------+
| device_id | 6f6abba9-c4e5-4c26-a3aa-f87b02d62419 |
| device_owner | compute:None |
| fixed_ips | {"subnet_id": "5b0d022b-33a2-42d9-873b-814ac2726e13", "ip_address": "192.168.10.6"} |
| id | 51783401-f174-4240-93df-028564aeb54b |
| mac_address | fa:16:3e:50:7a:73 |
| name | Avi-Data:cluster-143b2840-19b6-409d-918d-d92edc98b2e1:cloud-15190a62-e284-4033-8800-70c27c452bad |
| network_id | d36521da-8810-457e-95e5-a350143e61a4 |
| security_groups | 2aba00a7-8b20-45d4-88f3-64b901b9e363 |
| | 3d13ee89-5069-4dd2-a505-b6d7032bea9e |
| | adcf99de-46d0-44e2-8f3b-037804f725f0 |
| status | ACTIVE |
| tenant_id | a6d878c0f7db40bf91ed1226e720460a |
...
+-----------------------+--------------------------------------------------------------------------------------------------+
[root@sivacos ~(keystone_admin)]# neutron port-show 69bb1115-7e1d-474d-97b7-178d25a2dbe6
+-----------------------+--------------------------------------------------------------------------------------------------+
| Field | Value |
+-----------------------+--------------------------------------------------------------------------------------------------+
| device_id | 6f6abba9-c4e5-4c26-a3aa-f87b02d62419 |
| device_owner | compute:None |
| fixed_ips | {"subnet_id": "4e010951-eb90-43af-9bad-e578f1ac2f77", "ip_address": "10.0.0.6"} |
| id | 69bb1115-7e1d-474d-97b7-178d25a2dbe6 |
| mac_address | fa:16:3e:91:92:38 |
| name | Avi-Data:cluster-143b2840-19b6-409d-918d-d92edc98b2e1:cloud-15190a62-e284-4033-8800-70c27c452bad |
| network_id | a6669299-dccb-40a9-a0d2-4608aaea79c0 |
| security_groups | 2aba00a7-8b20-45d4-88f3-64b901b9e363 |
| | 3d13ee89-5069-4dd2-a505-b6d7032bea9e |
| | adcf99de-46d0-44e2-8f3b-037804f725f0 |
| status | ACTIVE |
| tenant_id | a6d878c0f7db40bf91ed1226e720460a |
...
+-----------------------+--------------------------------------------------------------------------------------------------+
[root@sivacos ~(keystone_admin)]# neutron port-show ca8c572e-f430-4176-87e0-780c81e82b91
+-----------------------+--------------------------------------------------------------------------------------------------+
| Field | Value |
+-----------------------+--------------------------------------------------------------------------------------------------+
| device_id | 6f6abba9-c4e5-4c26-a3aa-f87b02d62419 |
| device_owner | compute:None |
| fixed_ips | {"subnet_id": "a178c1f1-5cce-4f0a-ac1a-8277e26b085e", "ip_address": "172.24.16.9"} |
| id | ca8c572e-f430-4176-87e0-780c81e82b91 |
| mac_address | fa:16:3e:c2:42:d1 |
| name | Avi-Mgmt:cluster-143b2840-19b6-409d-918d-d92edc98b2e1:cloud-15190a62-e284-4033-8800-70c27c452bad |
| network_id | 27bd1f64-5a50-4189-98db-3265809ac71a |
| security_groups | 30fe49a4-ee31-43a9-9235-e23d59e392b3 |
| | 3d13ee89-5069-4dd2-a505-b6d7032bea9e |
| status | ACTIVE |
| tenant_id | a6d878c0f7db40bf91ed1226e720460a |
...
+-----------------------+--------------------------------------------------------------------------------------------------+
Disabling Custom Security Groups
You can manage the security groups along with the rules that Avi Vantage needs for the necessary operations.
You can configure custom security group at Service Engine group level for both data and management interface and set an option to disable Avi Vantage security groups.
Note: You cannot change disable_avi_security_groups option on an existing Service Engine group having Service Engines.
Custom Security Group Naming Convention
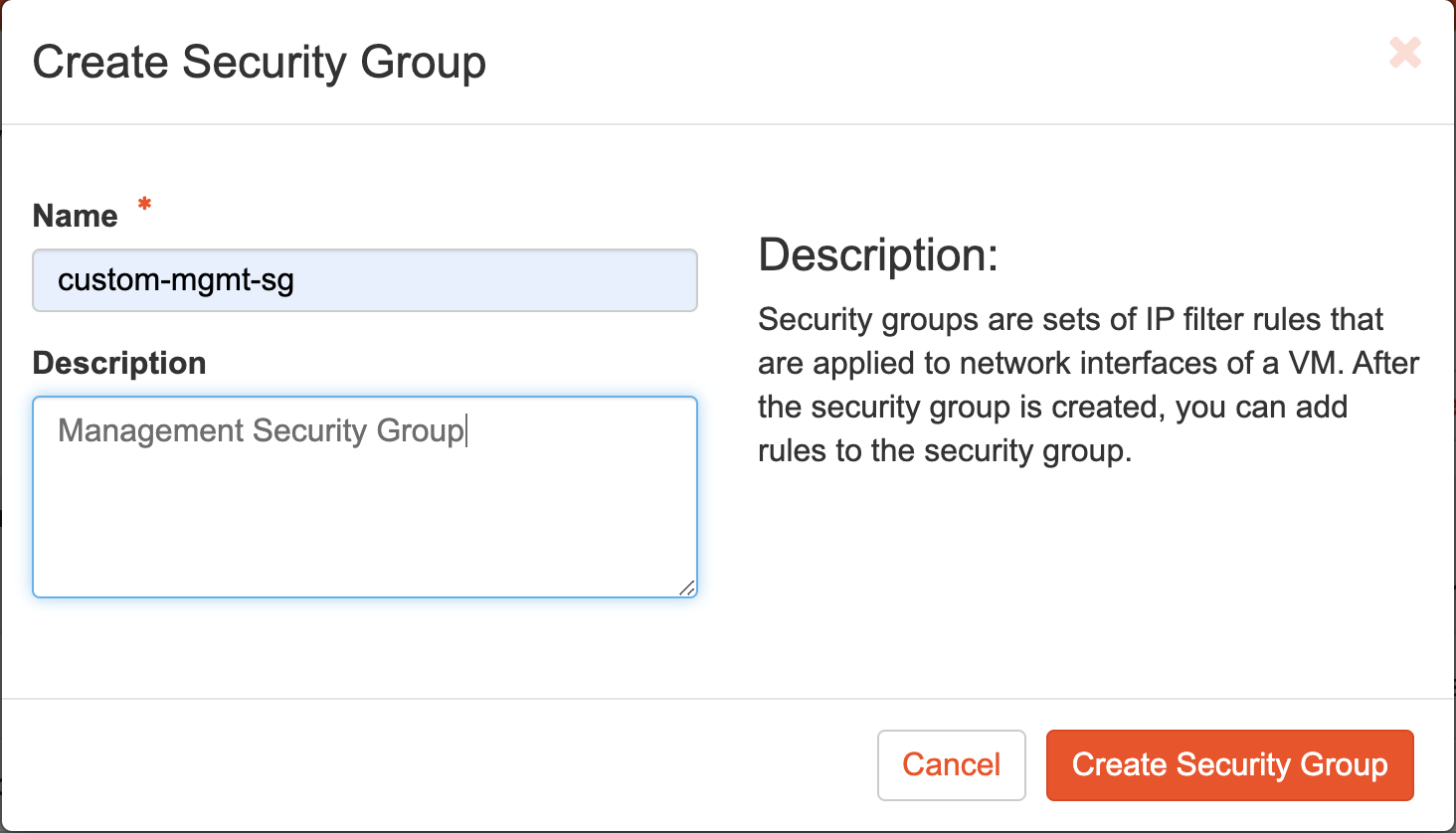
You can manage a security group in the Create Security Group window. Once you create a security group, you can add the rules to the security group.
You can specify the following details:
Name — Specify the name of the security group to be applied to network interfaces of a virtual machine.
Note: Custom security group name must not contain -se- or avi-se- in it. This is mandatory so as to differentiate and identify the custom security group from Avi Vantage created security groups.
Description — Specify the description of the security group name you provided.
You can add the rules by clicking on Create Security Group button. The following window is displayed:
The system displays the following values:
- Security group name
- Security group ID
- Security group description
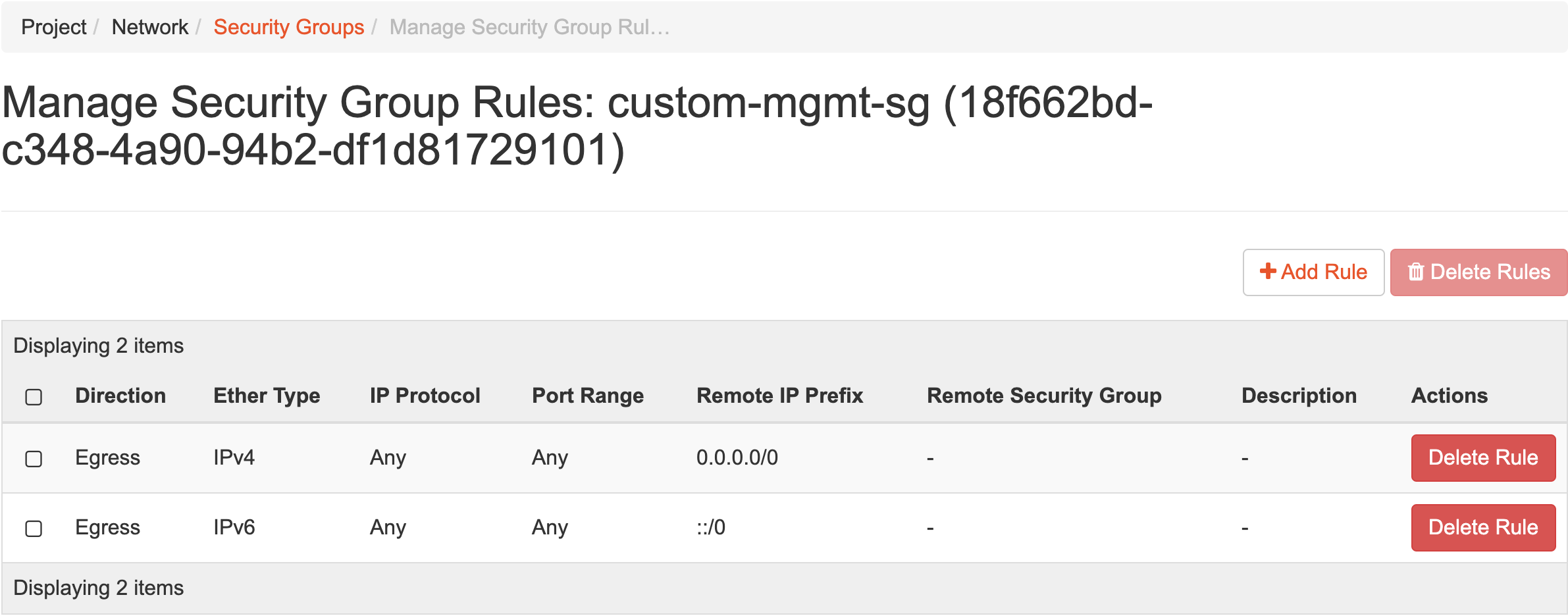
You can manage the rules in Actions field. Click on Manage Rules button. The following window is displayed:
By default, all egress are open when you create a security group. You need to delete these default egress rules by clicking Delete Rules button.
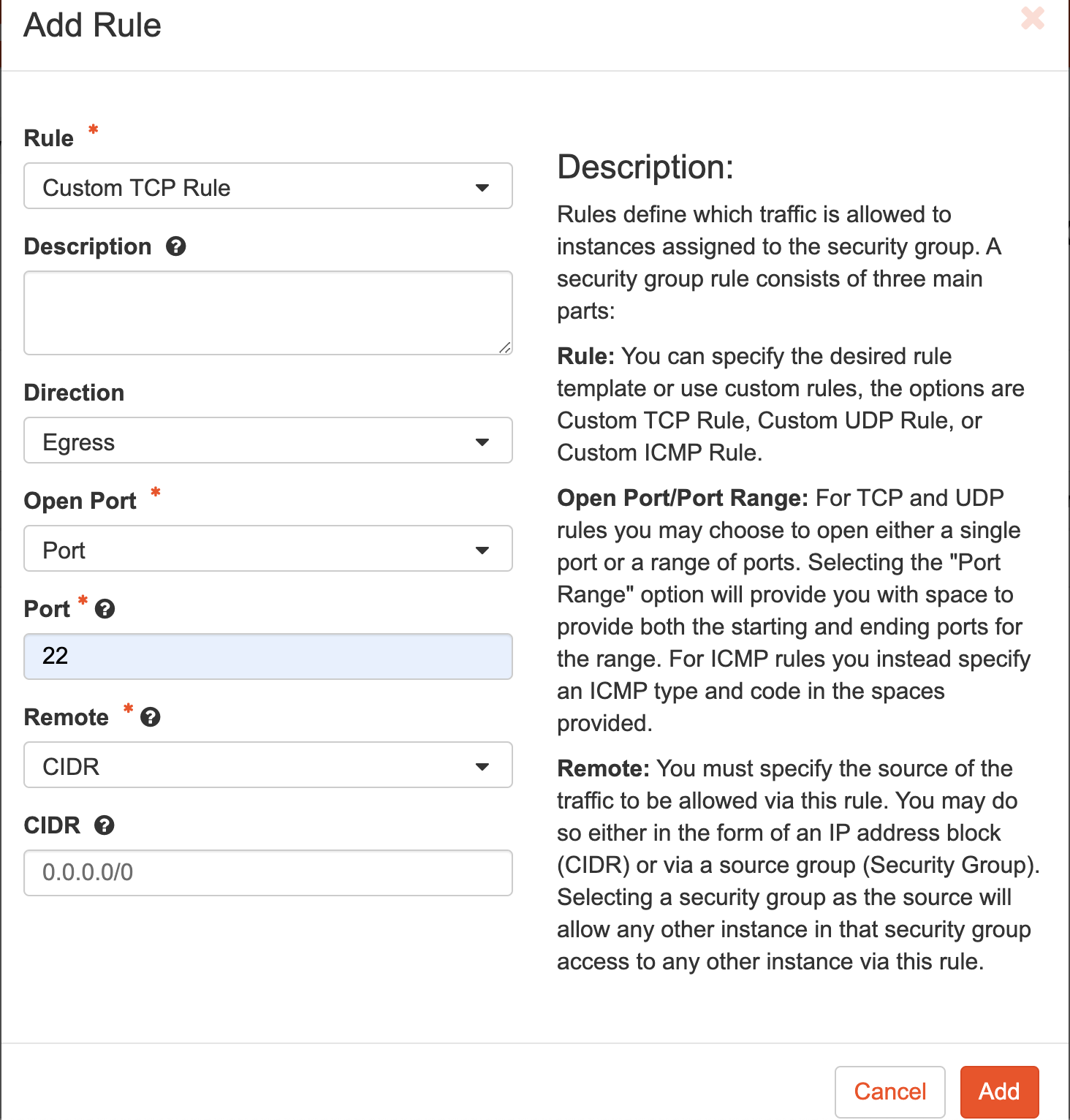
You can add a rule by clicking on Add Rule button.
The following are the rules to configure in custom security group for management interface:
| Direction | Ether Tye | IP Protocol | Port Range | Remote IP Prefix |
|---|---|---|---|---|
| Egress | IPv4 | TCP | 22 (SSH) | 0.0.0.0/0 |
| Egress | IPv4 | TCP | 8443 | 0.0.0.0/0 |
| Egress | IPv4 | UDP | 123 | 0.0.0.0/0 |
| Ingress | IPv4 | ICMP | Any | 0.0.0.0/0 |
| Ingress | IPv4 | TCP | 22 (SSH) | 0.0.0.0/0 |
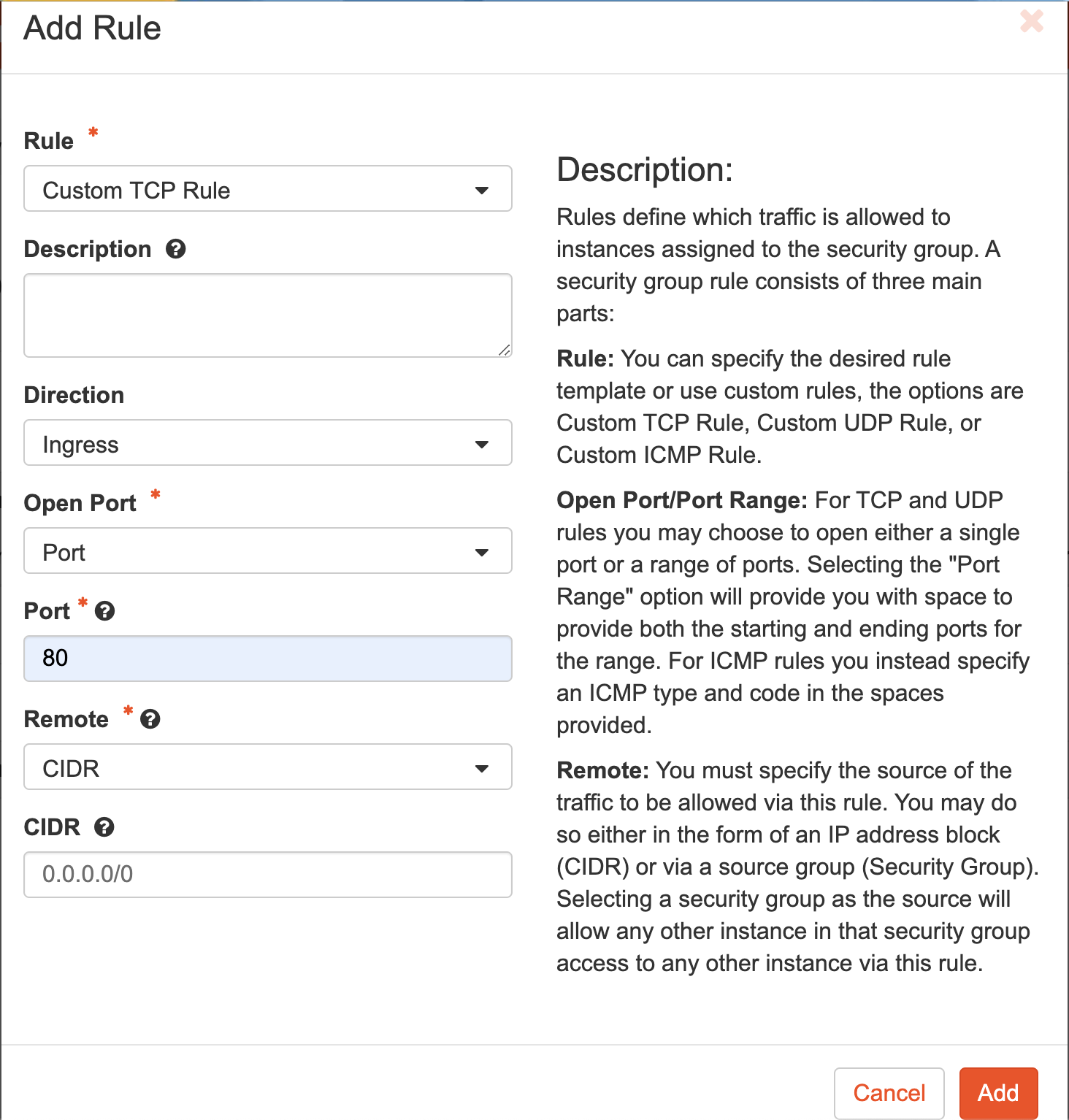
Clicking on Add Rule button, the following window is displayed:
You can add similar rules for IPv6 Ether Type, if required.
Data Rules
By default, all egress are open when a security group gets created. You can either create or remove the same.
You should configure virtual service ports/rules in custom security group for data interface. For instance, 80, 443, etc.
| Direction | Ether Tye | IP Protocol | Port Range | Remote IP Prefix |
|---|---|---|---|---|
| Ingress | IPv4 | HTTP | 80 | 0.0.0.0/0 |
You can add similar rules for IPv6 ether type, if required.
Configuring Service Engine Group
The following are the steps to configure Service Engine group:
-
You can configure Service Engine group to use or apply the created custom security group.
-
Use the following custom security group IDs for configuration:
-
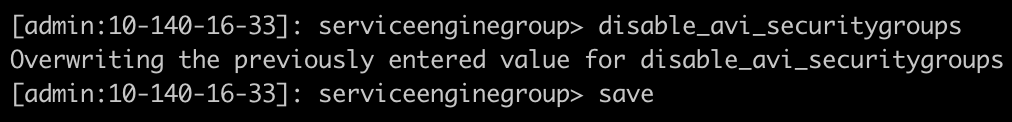
Set disable_avi_securitygroups option to True. By default, it is set to False.
Additional References
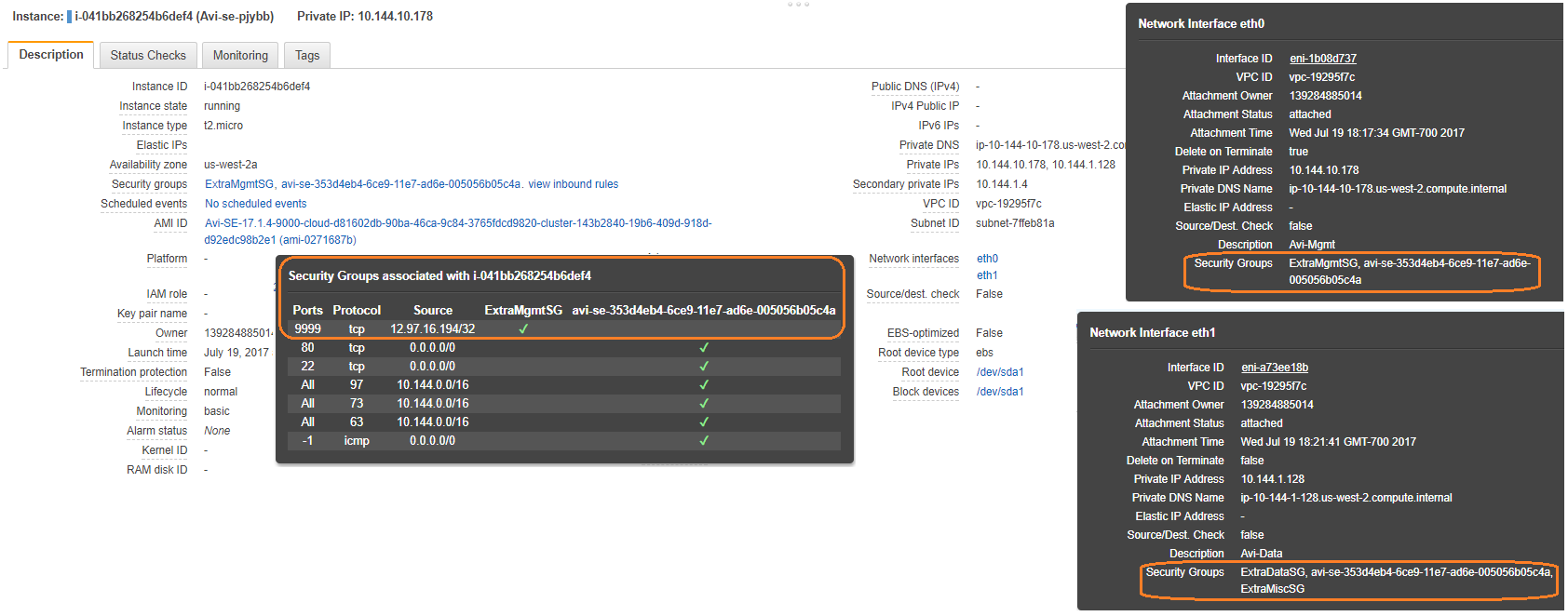
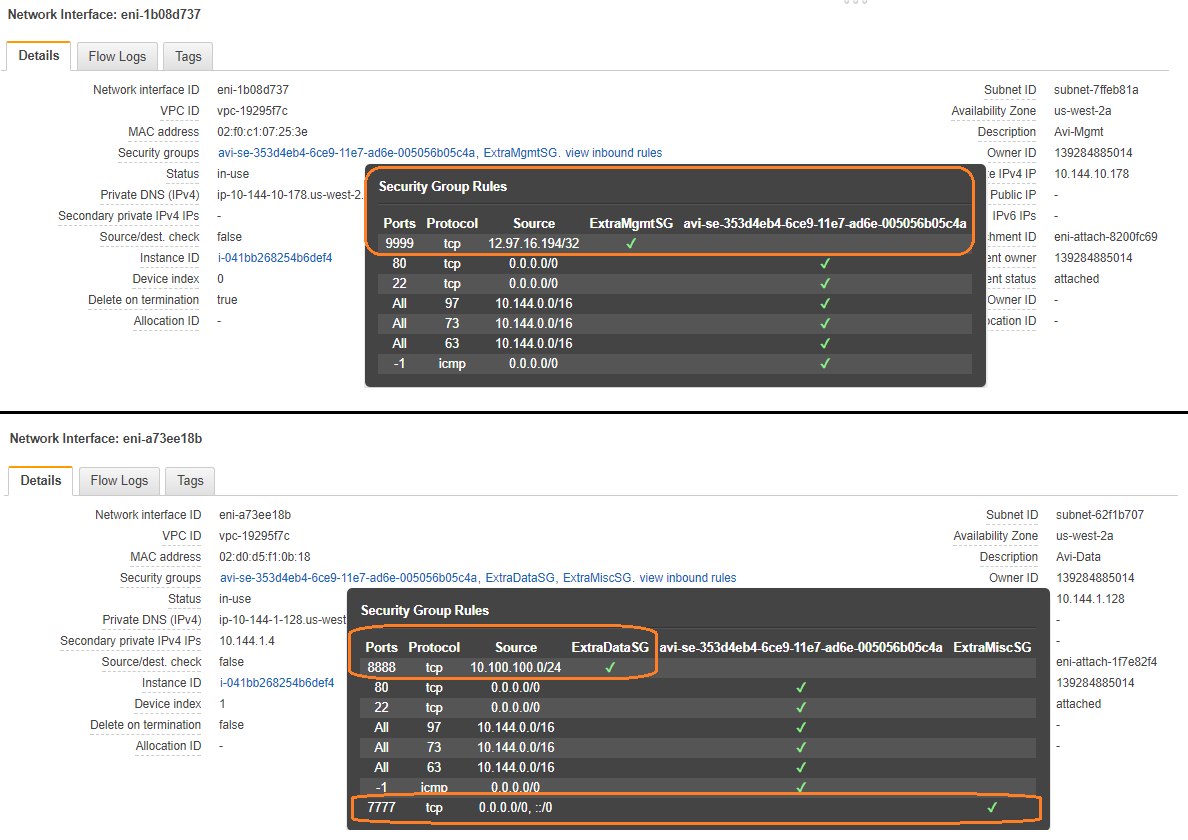
AWS Cloud
Without any Custom Security group configuration
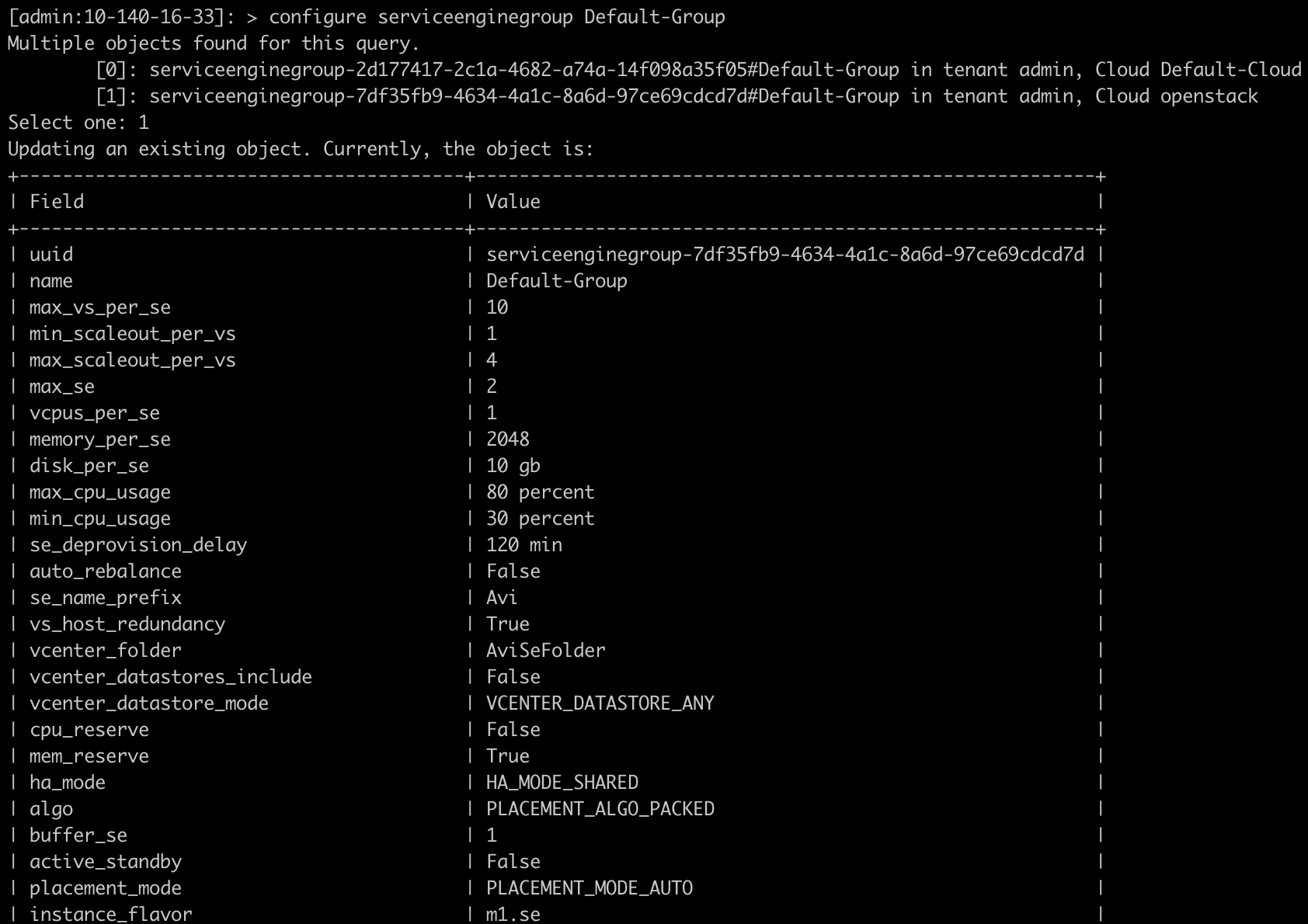
Custom Security Group Configuration via the Avi CLI
[admin:10-10-22-44]: > configure serviceenginegroup Default-Group
[admin:10-10-22-44]: serviceenginegroup> custom_securitygroups_mgmt sg-5c902726
[admin:10-10-22-44]: serviceenginegroup> custom_securitygroups_data sg-4b9d2a31
[admin:10-10-22-44]: serviceenginegroup> custom_securitygroups_data sg-b99c2bc3
[admin:10-10-22-44]: serviceenginegroup> save
+---------------------------------------+---------------------------------------------------------+
| Field | Value |
+---------------------------------------+---------------------------------------------------------+
...
| custom_securitygroups_mgmt[1] | sg-5c902726 |
| custom_securitygroups_data[1] | sg-4b9d2a31 |
| custom_securitygroups_data[2] | sg-b99c2bc3
Custom Security-group Configuration via the Avi UI
Navigate to Applications > Infrastructure > Service Engine Group and invoke the SE group editor. Select the appropriate named custom security groups for the management vNIC and the data vNIC.