IAM Role Setup for Installation into AWS
If using the IAM role method to define access for an Avi Vantage installation in Amazon Web Services (AWS), use the steps in this article to set up the IAM roles before beginning deployment of the Avi Controller EC2 instance.
| IAM Role Name | Policy Name | Description | Required |
|---|---|---|---|
| vmimport vmimport-role-trust.json |
vmimport vmimport-role-policy.json |
Enables the Avi SE VM to be imported into AWS. Without this IAM role, the Avi SE cannot be launched. This role is associated with the AWS account (not with the Avi Controller). For more details on vmimport, refer to VM Import/Export guide. | Yes |
| kmsimport avicontroller-kms-vmimport.json |
Used to create an IAM policy and attached to vmimport role, or it can be directly applied to the KMS key. | Yes | |
| AviController-Refined-Role avicontroller-role-trust.json |
avicontroller-ec2-policy avicontroller-ec2-policy.json |
Enables Avi Controller instance to be installed. | Yes |
| AviController-IAM-Policy avicontroller-iam-policy.json |
Enable access to retrieve IAM roles and policy information. | Yes | |
| AviController-s3-Policy avicontroller-s3-policy.json |
Enables S3 permissions. | Yes | |
| AviController-R53-Policy aviController-r53-policy.json |
Enables access to the AWS cloud's DNS. | No | |
| AviController-AutoScalingGroup-Policy avicontroller-asg-policy.json |
Enables read access to the AWS cloud's Auto Scaling groups. | No | |
| AviController-SQS-SNS-Policy avicontroller-sqs-sns-policy.json |
Enables Avi Controller to use SNS and SQS feature for Auto Scaling groups. .Allows NSX ALB Controller to receive ASG notifications when SNS and SQS features are enabled. | No | |
| AviController-KMS-Policy avicontroller-kms-policy.json |
Enables the Avi Controller to list the encryption keys in the Avi UI, and decrypt encrypted messages (required, when using SQS encryption) |
No |
To begin, download the JSON files for the IAM role and policies onto a host that has the AWS CLI.
Then use one of the following workflows to set up the IAM roles:
Using the AWS CLI
The AWS CLI needs to be run from the same directory in which you save the files.
Step 1. Create the VM Import Service Role
Use the following commands to create a role name “vmimport” with the required permission.
aws iam create-role --role-name vmimport --assume-role-policy-document file://vmimport-role-trust.json
aws iam put-role-policy --role-name vmimport --policy-name vmimport --policy-document file://vmimport-role-policy.json
aws iam put-role-policy --role-name vmimport --policy-name AviController-vmimport-KMS-Policy --policy-document file://avicontroller-kms-vmimport.json
Step 2. Create the required policies for the Avi Controller role
AviController-Refined-Role is the role which will be attached to the Avi Controller via the instance profile. Follow the below commands.
aws iam create-role --role-name AviController-Refined-Role --assume-role-policy-document file://avicontroller-role-trust.json
aws iam create-policy --policy-name AviController-EC2-Policy --policy-document file://avicontroller-ec2-policy.json
aws iam create-policy --policy-name AviController-S3-Policy --policy-document file://avicontroller-s3-policy.json
aws iam create-policy --policy-name AviController-IAM-Policy --policy-document file://avicontroller-iam-policy.json
aws iam create-policy --policy-name AviController-R53-Policy --policy-document file://avicontroller-r53-policy.json
aws iam create-policy --policy-name AviController-ASG-Policy --policy-document file://avicontroller-asg-policy.json
aws iam create-policy --policy-name AviController-SQS-SNS-Policy --policy-document file://avicontroller-sqs-sns-policy.json
aws iam create-policy --policy-name AviController-KMS-Policy --policy-document file://avicontroller-kms-policy.json
Note: Following are the optional policies for AWS DNS service and the SNS-SQS feature. They are not needed for the basic setup.
- AviController-R53-Policy
- AviController-AutoScalingGroup-Policy
- AviController-SQS-SNS-Policy
- AviController-KMS-Policy (supported as of release 17.2.8)
Step 3. Attach policies to the Avi Controller role
Once the policies (AviController-EC2-Policy, AviController-R53-Policy, AviController-IAM-Policy, etc.) are created (in Step 2), attach them to the AviController-Refined-Role.
aws iam attach-role-policy --role-name AviController-Refined-Role --policy-arn "arn:aws:iam::123456789012:policy/AviController-EC2-Policy"
aws iam attach-role-policy --role-name AviController-Refined-Role --policy-arn "arn:aws:iam::123456789012:policy/AviController-R53-Policy"
aws iam attach-role-policy --role-name AviController-Refined-Role --policy-arn "arn:aws:iam::123456789012:policy/AviController-AutoScalingGroup-Policy"
aws iam attach-role-policy --role-name AviController-Refined-Role --policy-arn "arn:aws:iam::123456789012:policy/AviController-SNS-Policy"
aws iam attach-role-policy --role-name AviController-Refined-Role --policy-arn "arn:aws:iam::123456789012:policy/AviController-SQS-Policy"
aws iam attach-role-policy --role-name AviController-Refined-Role --policy-arn "arn:aws:iam::123456789012:policy/AviController-ASG-Notification"
aws iam attach-role-policy --role-name AviController-Refined-Role --policy-arn "arn:aws:iam::123456789012:policy/AviController-KMS-Policy"
Note: Following are the optional policies for AWS DNS service and SNS-SQS feature. It is not necessary to attach these to the Avi Controller role for the basic setup.
- AviController-R53-Policy
- AviController-AutoScalingGroup-Policy
- AviController-SQS-SNS-Policy
- AviController-KMS-Policy
Step 4. Create instance profile and apply this instance profile to EC2 role.
aws iam create-role --role-name AviController-Refined-Role --assume-role-policy-document file://avicontroller-role-trust.json
aws iam create-policy --policy-name AviController-EC2-Policy --policy-document file://avicontroller-ec2-policy.json
aws iam create-policy --policy-name AviController-S3-Policy --policy-document file://avicontroller-s3-policy.json
aws iam create-policy --policy-name AviController-IAM-Policy --policy-document file://avicontroller-iam-policy.json
aws iam create-policy --policy-name AviController-R53-Policy --policy-document file://avicontroller-r53-policy.json
aws iam create-policy --policy-name AviController-ASG-Policy --policy-document file://avicontroller-asg-policy.json
aws iam create-policy --policy-name AviController-SQS-SNS-Policy --policy-document file://avicontroller-sqs-sns-policy.json
aws iam create-policy --policy-name AviController-KMS-Policy --policy-document file://avicontroller-kms-policy.json
Note:
- The aws put-role-policy command creates an inline policy in the role (as opposed to an attached policy).
- Make sure to replace “123456789012” with the applicable AWS account ID.
Using AWS Web Interface
The various roles and the associated policies mentioned in the previous section can be created using AWS web interface (AWS management console) too. This section discusses configuration steps for the following mandatory policies and the associated roles.
- vmimport policy
- vmimport role (associated with vmimport policy)
- AviController-Refined-Role
- AviController-EC2-Policy (associated with AviController-Refined-Role)
- AviController-IAM-Policy (associated with AviController-Refined-Role)
Follow the same steps to create the optional policies as required.
Creating vmimport policy
-
Log into the AWS console using your AWS customer account, select Policies.
-
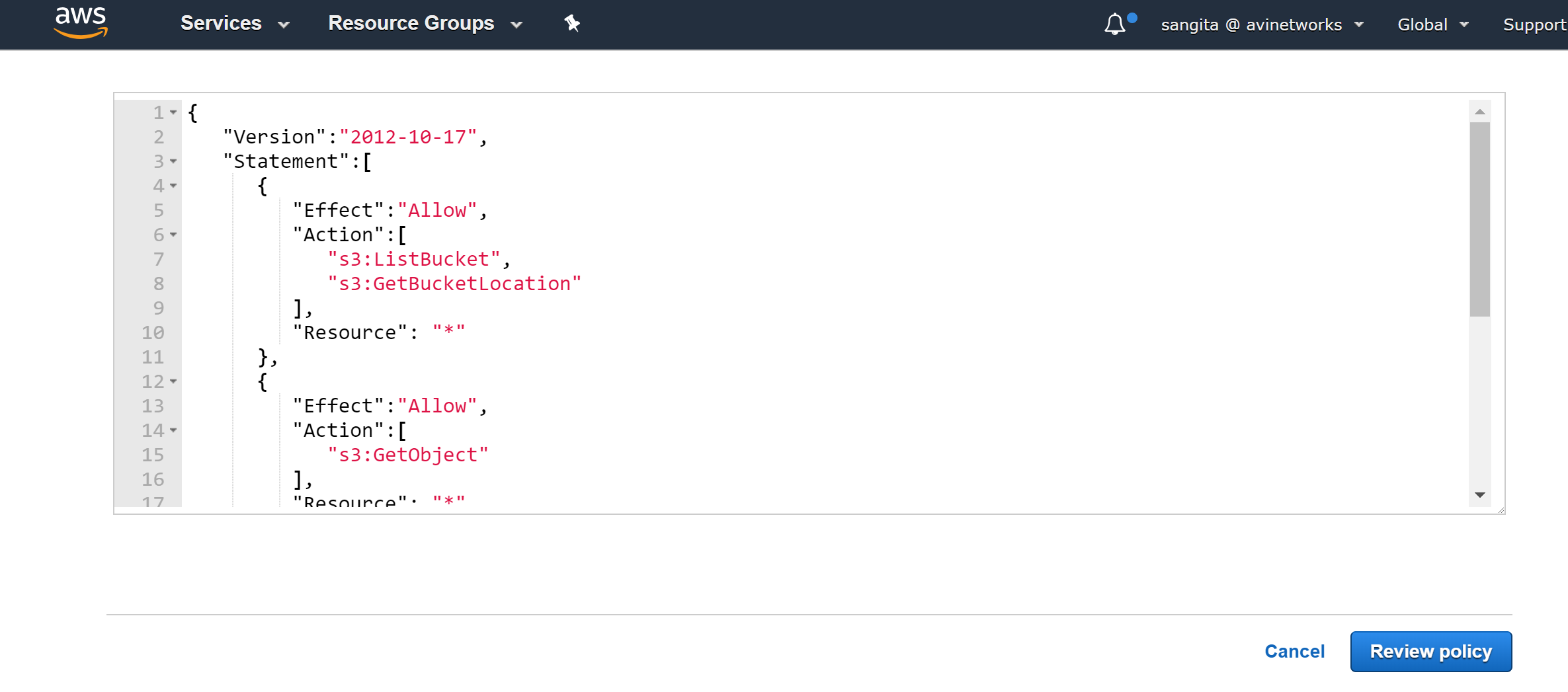
Select Create policy, select JSON tab, copy and paste the content from the JSON file (vmimport-role-policy.json), and click on Review Policy.
-
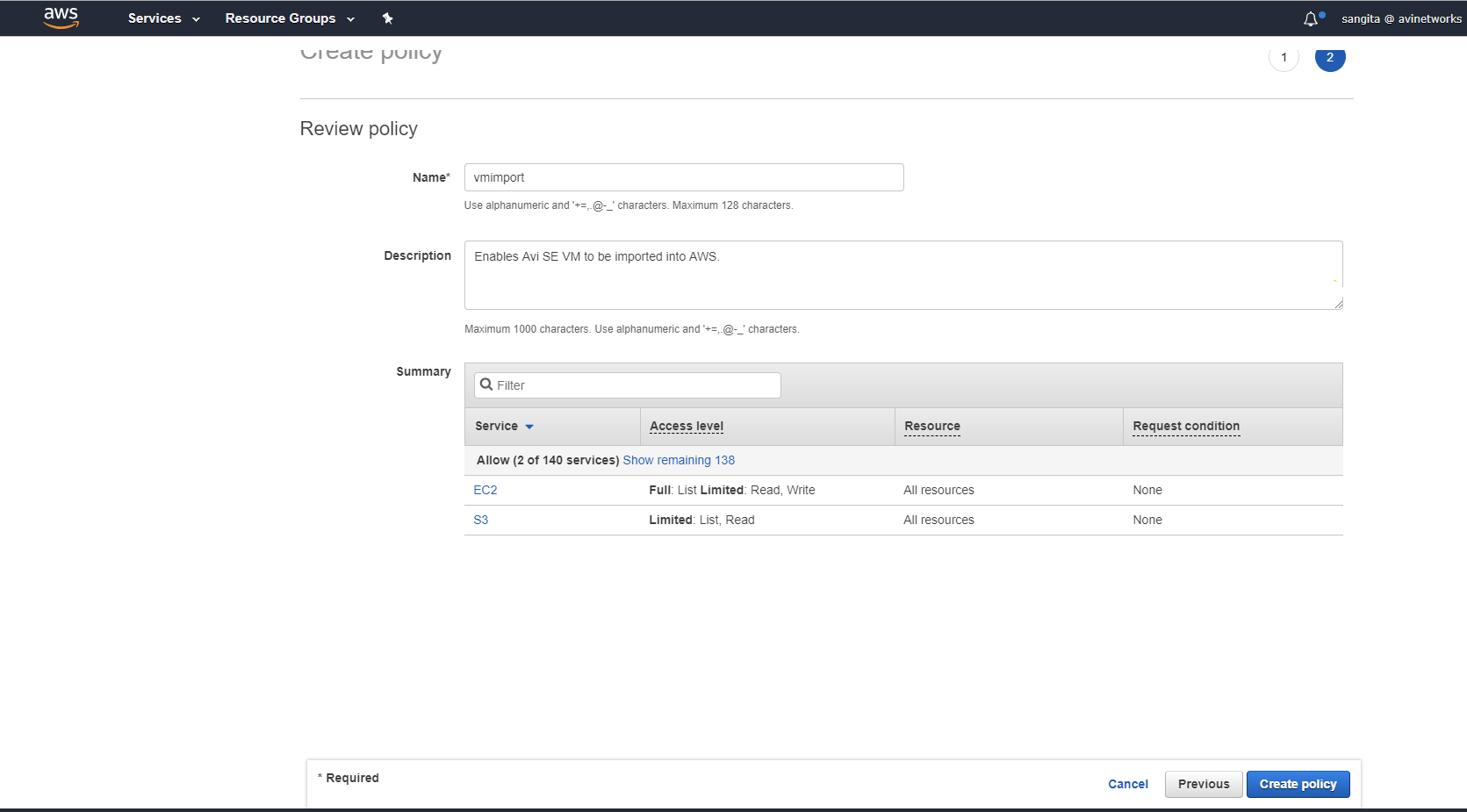
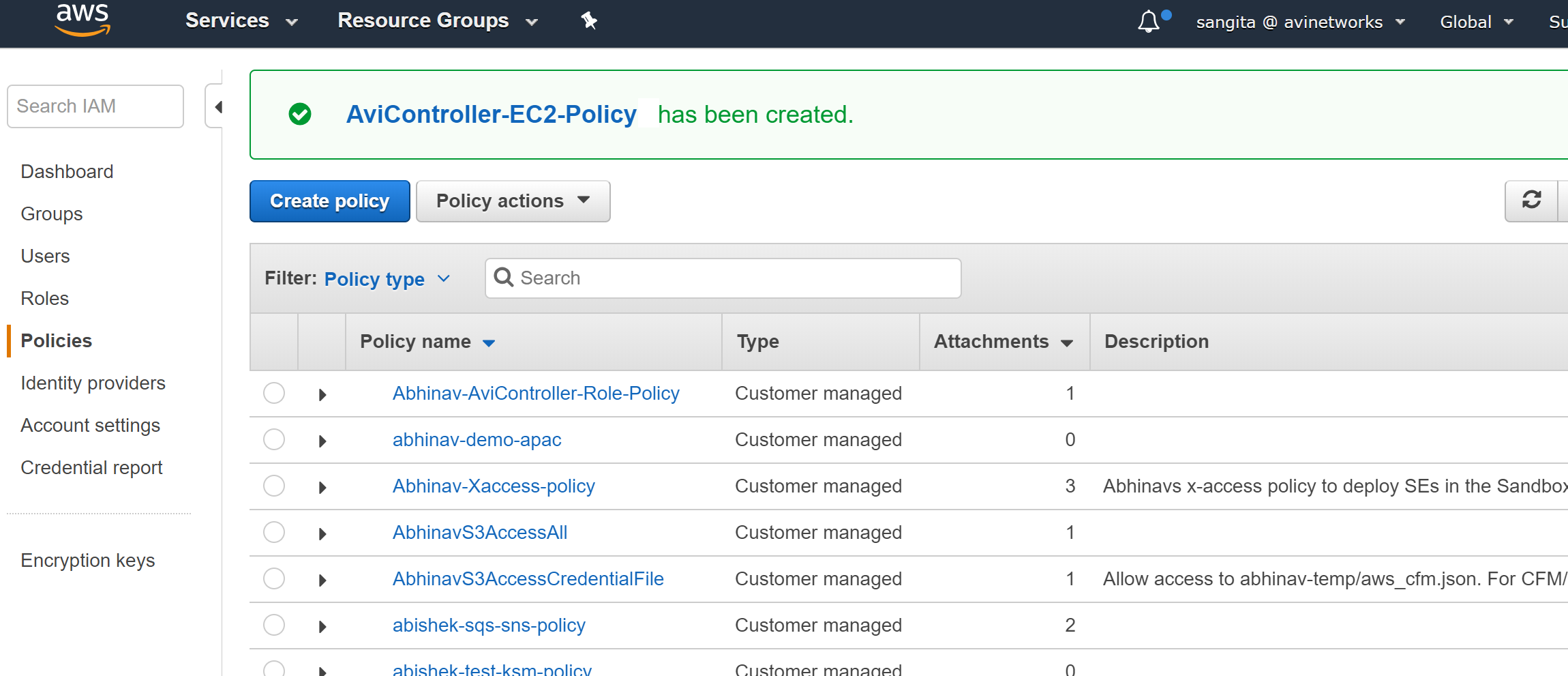
Provide the name for the policy (vmimport), the description (optional), click on Create Policy.
Creating vmimport role and associating it with the vmimport policy
-
Select Roles, then click on Create role.
-
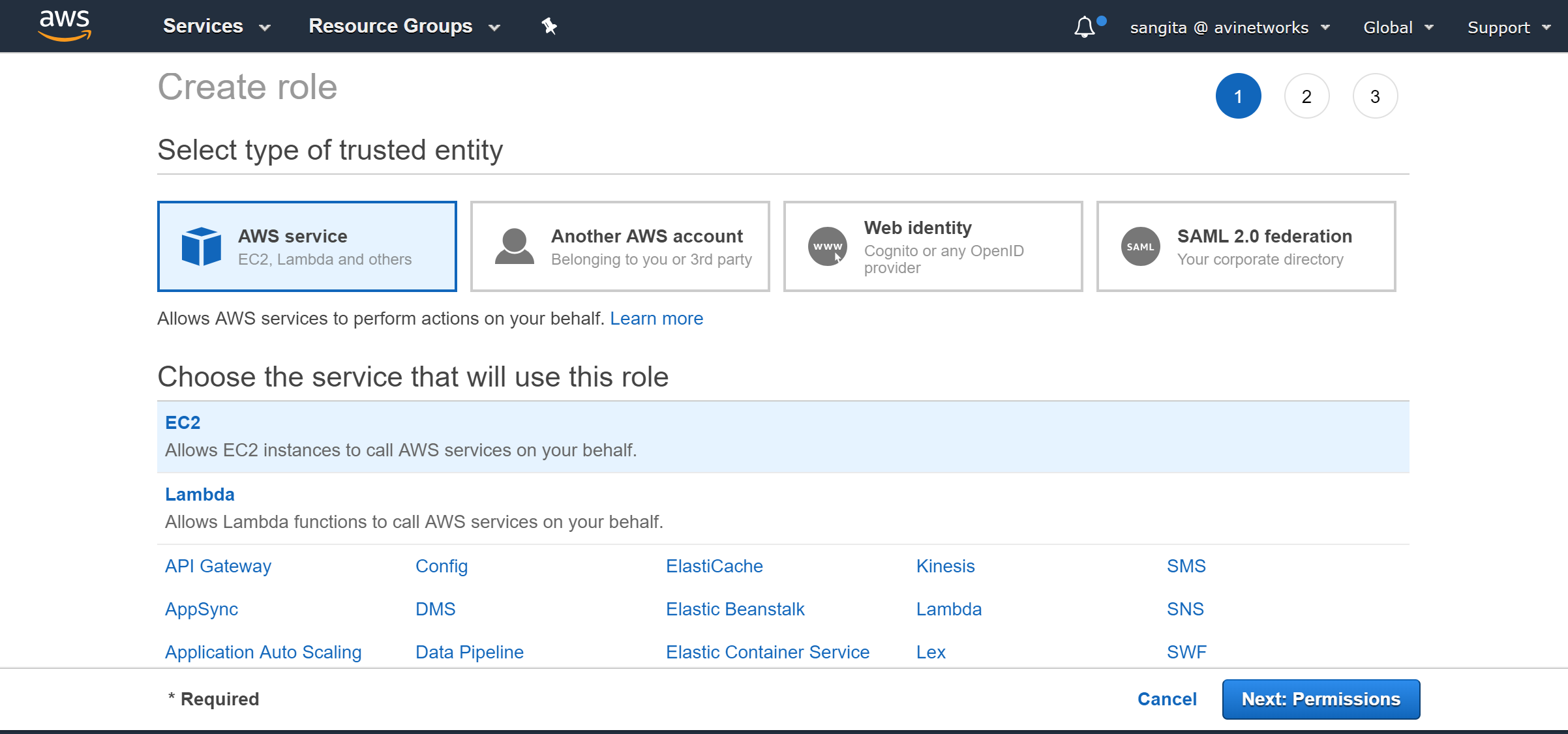
Select type of trusted identity (AWS Service), choose the service (EC2) that will use this role, and click on Next:Permissions.
-
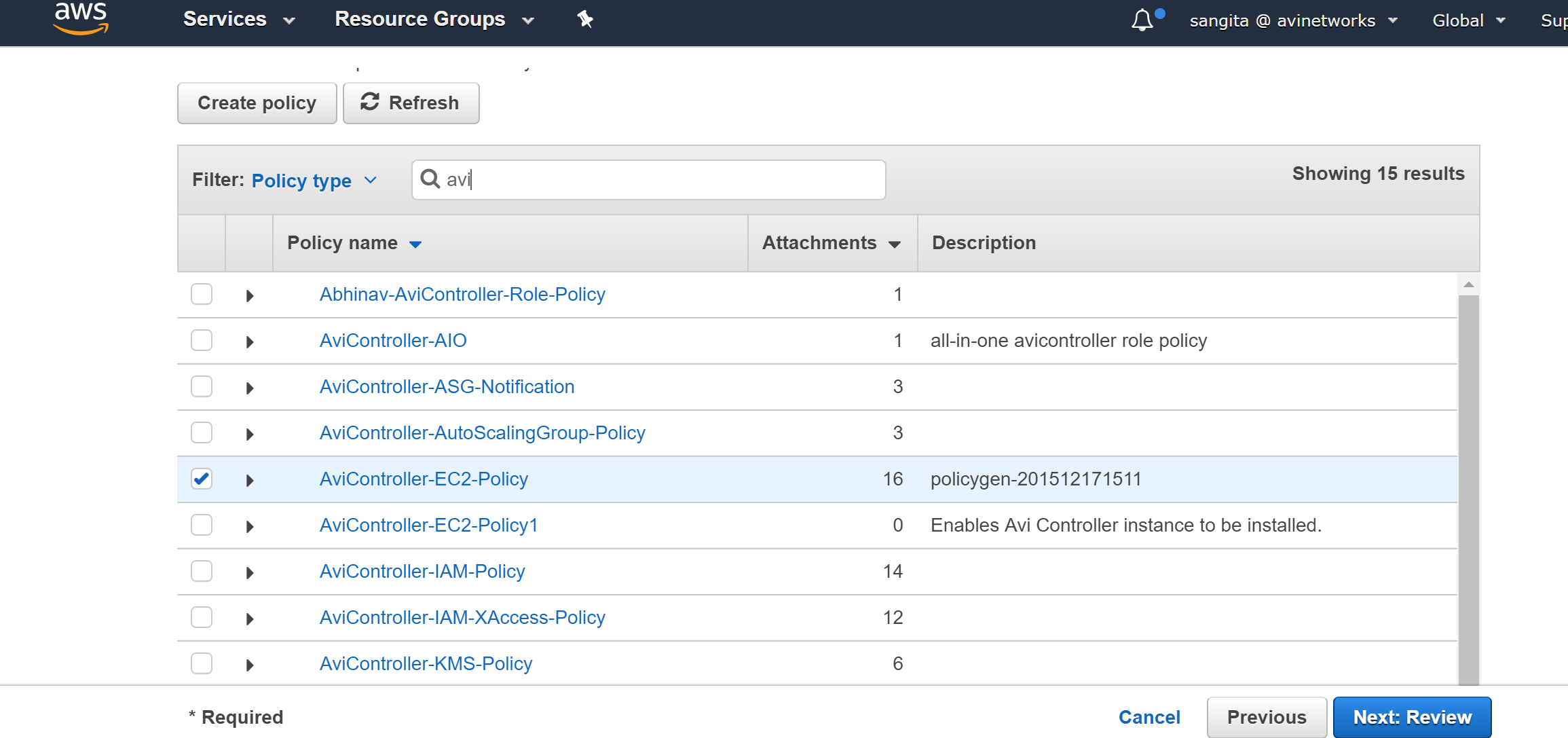
Select the policy created in previous step (vmimport policy), and click on Next:Review.
-
Provide Role name, Role description, and click on Create role.
-
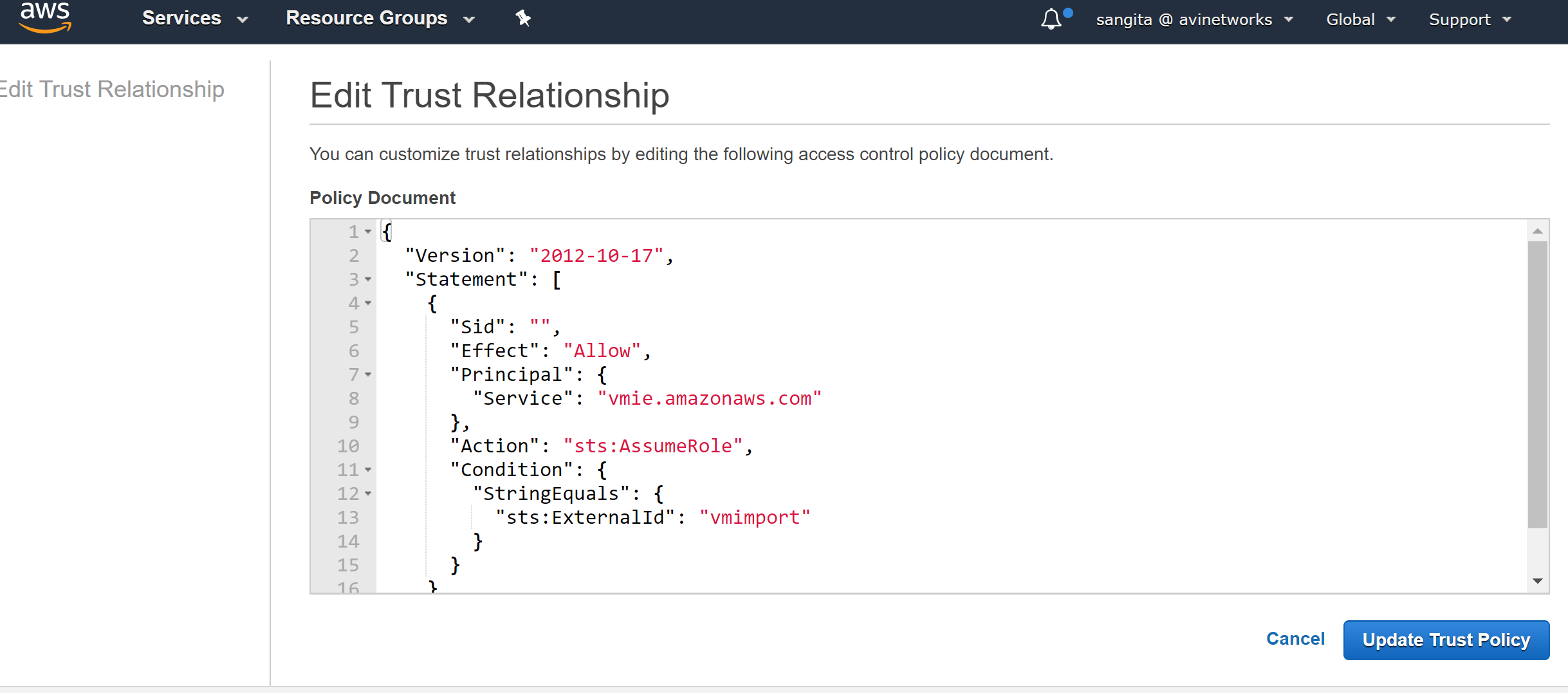
Once the role is created, AWS web interface will exhibit the following message as shown in the below screenshot.
Note: For vmimport role, Trust relationships should be edited. Navigate to the Trust relationships tab, click on edit, and copy the content of vmimport-role-trust.json (from the table mentioned in the beginning) to the JSON tab, and click on Update Trust Policy.
Creating AviController-Refined-Role
Creating Policies
-
Select the Policies option on AWS web interface, and click on Create Policy.
-
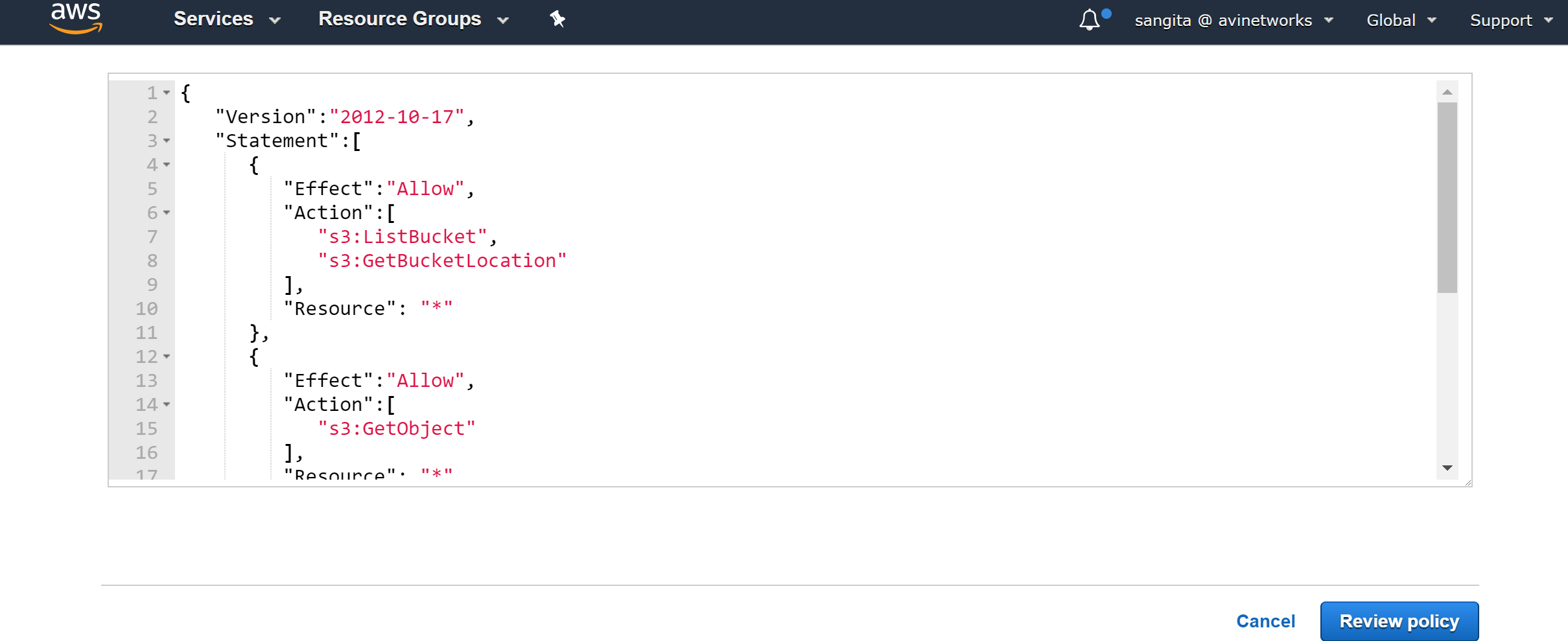
Select JSON tab, copy the content from the JSON file (avicontroller-role-policy.json), paste in the JSON box, and click on Review Policy.
-
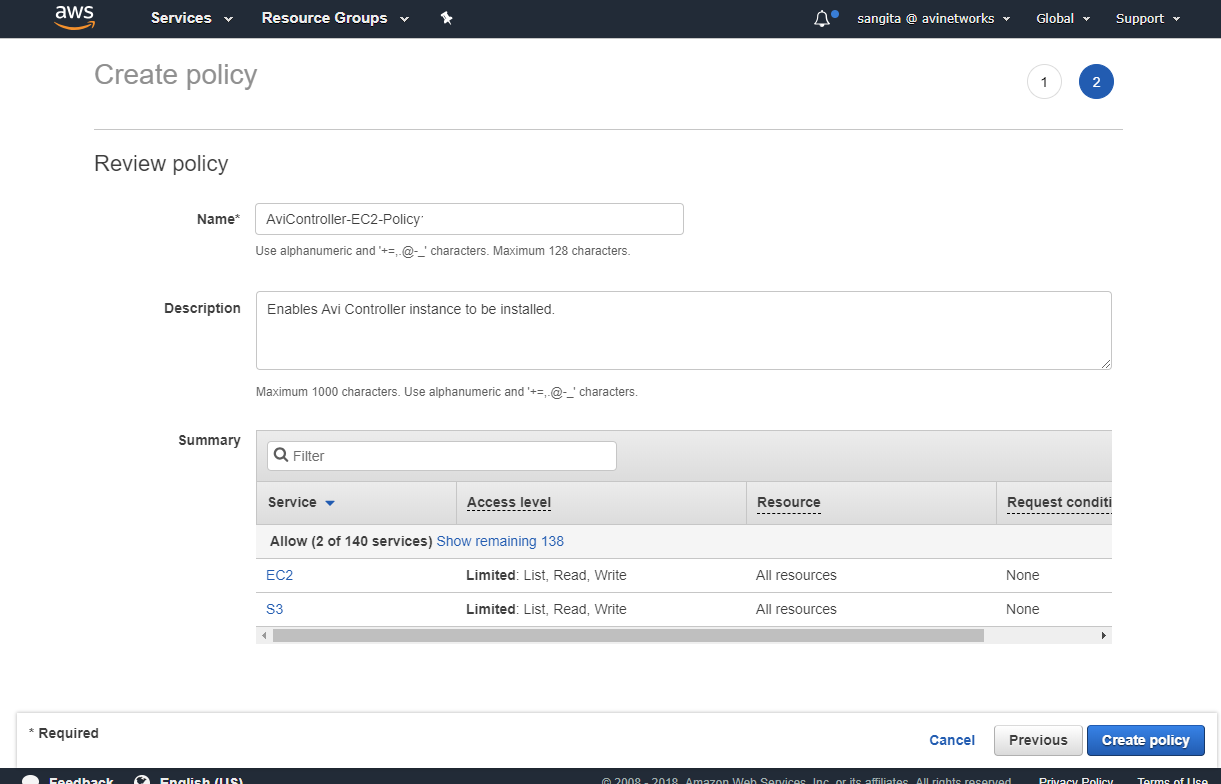
Provide the name for the policy (AviController-EC2-Policy), the description (optional), and click on Create Policy.
-
Once the policy is successfully created, AWS web interface will exhibit the following message.
Notes:
- Follow the steps mentioned above to create AviController-IAM-Policy. Choose the policy name and the JSON file as mentioned in the table provided at the beginning of the article.
- Based on the requirement, create the other optional policies as well. For example, If Avi Vantage will use the AWS DNS service, create a policy named “AviController-R53-Policy” and copy-and-paste the contents of the avicontroller-role-53-policy.json file into the Policy Document field.
Creating Role and Associating with the Required Policies
-
Select Roles, and click on Create Role.
-
Select type of trusted identity (AWS Service), choose the service (EC2) that will use this role, and click on Next:Permissions.
-
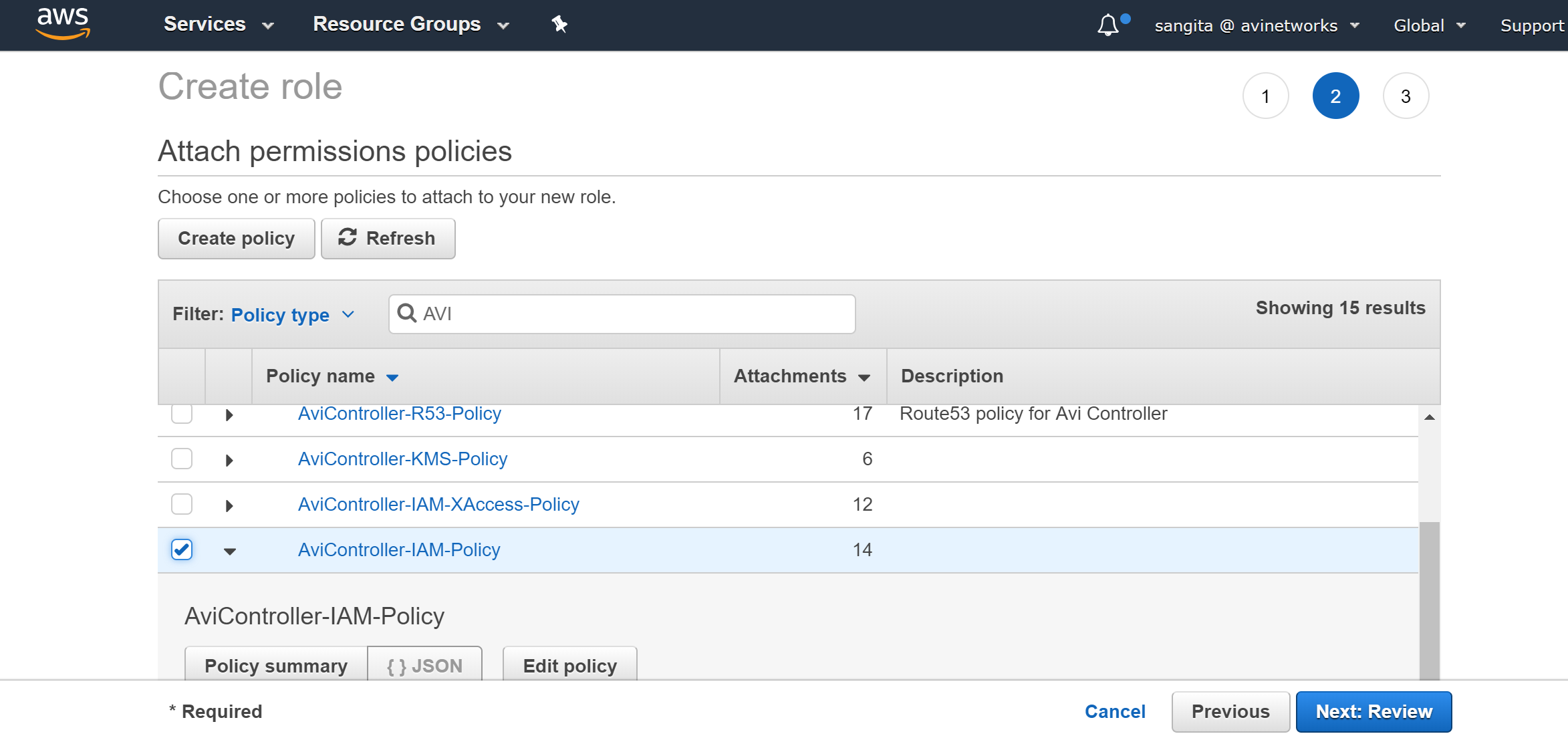
select the policy created in previous step (AviController-EC2-Policy), and (AviController-IAM-Policy), and select Next: Preview.
-
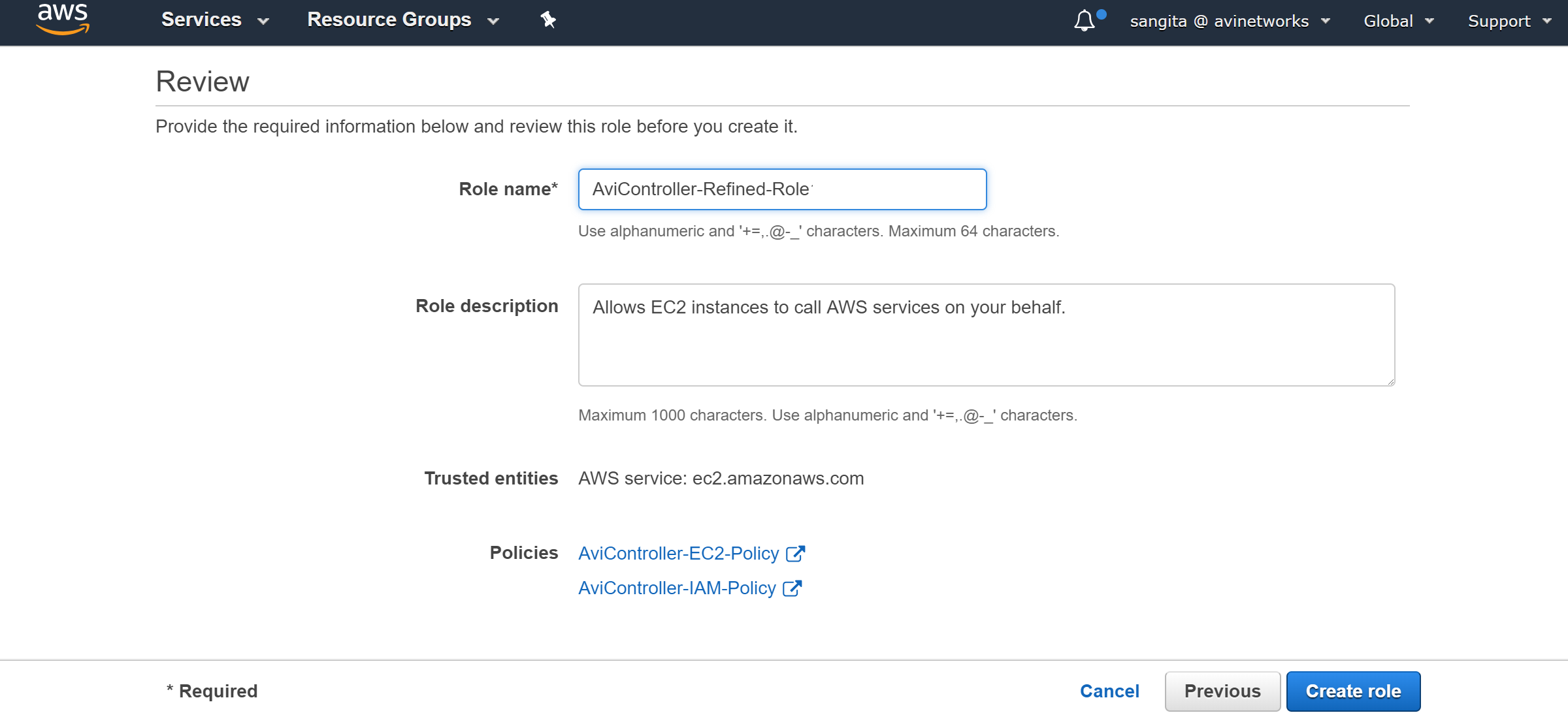
Provide the role name (AviController-Refined-Role), the description (optional), and click on Create role.
-
Once the role is created, AWS web interface will exhibit the following message as shown in the below screenshot.
The new roles should be in the list.
Note There are 2 ways, an AWS cloud can be created in Avi Vantage. 1) Using Access/Secret key. 2) Using IAM roles of the Avi Controller.
Both of the methods mentioned above, require a vmimport role to be present. However, while using the Access/Secret key method, the user whose keys are used must have all the necessary permissions for carrying out all the operations done in Avi Vantage.
AviController-Refined-Role needs to be present, if we choose using IAM roles of the Avi Controller option. If the AviController-Refined-Role role is created using AWS CLI, then, an instance-profile is required as created in step-4. But, if the role is created using AWS GUI, then it is not required to create instance-profile separately, as it is automatically created along with the role.
Once all the required roles and policies are configured, refer to Installing Avi Vantage in Amazon Web Services to install the Avi Vantage EC2 instance.