SSL Security Definition
Secure Sockets Layer (SSL) is a standard security technology for establishing an encrypted link between a server and a client—typically a web server (website) and a browser, or a mail server and a mail client (e.g., Outlook). SSL security safeguards sensitive data such as credit card numbers and financial information, from capture or modification as two systems send and receive it, to prevent unauthorized users from accessing, reading, or modifying any personal information.
The two systems transferring the information might both be servers, as when an application accesses sensitive information. The systems might also be a client and a server, as when a user buys things on an e-commerce website through their web browser.
To protect the sensitive data in transmission, SSL security encrypts the information using algorithms, rendering it unreadable during the transfer between sites, systems, and/or users. Various versions of SSL security protocols are widespread use in applications such as email, chatting and instant messaging, voice over IP (VoIP), and web browsing.
What is SSL Security?
SSL is a security protocol that determines how to encrypt data using specific algorithms. The secure socket layer SSL protocol assesses both the data to transmit and the link, and determines encryption variables for both.
SSL security technology establishes encrypted links between clients and servers. For example, it scrambles sensitive information transferred between a client, often a website, and a user, often a browser or mail server.
The default mode of communication between web servers and browsers allows data to be sent in plain text. This leaves users vulnerable to hackers who can “see” information they intercept. SSL encrypts sensitive details such as login credentials, social security numbers, and bank information so that unauthorized users cannot interpret and use the data, even if they see it.
The lock icon users see on SSL-secured websites and the “https” address indicate that a secure connection is present. Sites with a green address bar have an Extended Validation SSL-secured website. These visual signals are sometimes called EV indicators.
Although any web browser is able to use the SSL protocol to interact with secured web servers, both the server and the browser must have an SSL certificate to establish a secure connection.
What is an SSL Security Certificate?
A SSL security certificate identifies the certificate/website owner in its subject. SSL security certificates also contain a pair of public and private cryptographic keys they use to establish an encrypted connection.
There are several steps to get a SSL or TLS certificate:
- Create a Certificate Signing Request (CSR) on your server to generate a public key and a private key.
- Send the CSR data file called a Certificate Authority or CA to the SSL certificate issuer.
- The CA contains the public key which the CA uses along with the rest of the CSR data file to match your private key with a data structure. The CA never sees the private key, nor is it compromised.
The certificate issuer gives you the SSL certificate. You install both the SSL certificate and an intermediate certificate that establishes its credibility on your server. Depending on the server and the other facts, how you install and test the SSL certificate will vary.
When your browser connects to the SSL certificate on your server, the SSL (or TLS) protocol begins to encrypt any transferred information.
The transmission control protocol (TCP) is the first layer of defense, with the SSL security protocol serving as a safety zone, operating directly on top of the TCP to provide a secure connection while leaving higher protocol layers unchanged. This way, other protocol layers function normally beneath the SSL layer.
Is SSL Security Safe from Man in the Middle Attacks?
The SSL certificate may allow hackers in a man in the middle attack to see how much data is being transferred, and which IP and port are connected. However they cannot intercept any information, and although they may be able to terminate the connection, it will be clear to both the user and the server that a third party broke the connection.
What is a Certificate Authority (CA)?
A certificate authority (CA) is a trusted entity that issues and manages SSL certificates. As part of the public key infrastructure (PKI), the CA also manages public keys that are used throughout a public network for secure communication. Along with the registration authority (RA), the CA also verifies the information digital certificate requesters provide in support of their requests. Once they verify the information, the CA can then issue a certificate.
Obviously CAs play an important role in encryption, but they can also augment security by authenticating website owner identities via their SSL certificates. There are three authentication categories for certificates based on the authentication level: domain validation certificates, organization validation certificates, and extended validation certificates.
Domain validation certificates require users to prove control over the domain name alone and represent the most basic level of SSL security. Organization validation certificates represent the next level, and for such a certificate to issue users must prove both control over the domain name and legal accountability for and ownership of the business.
Extended validation EV certificates demand the most from users, including everything the other certificates require, plus additional verification steps. This highest level of SSL security helps protect against phishing and other security issues.
Can You Explain How SSL Protocol is Used for Secure Transactions?
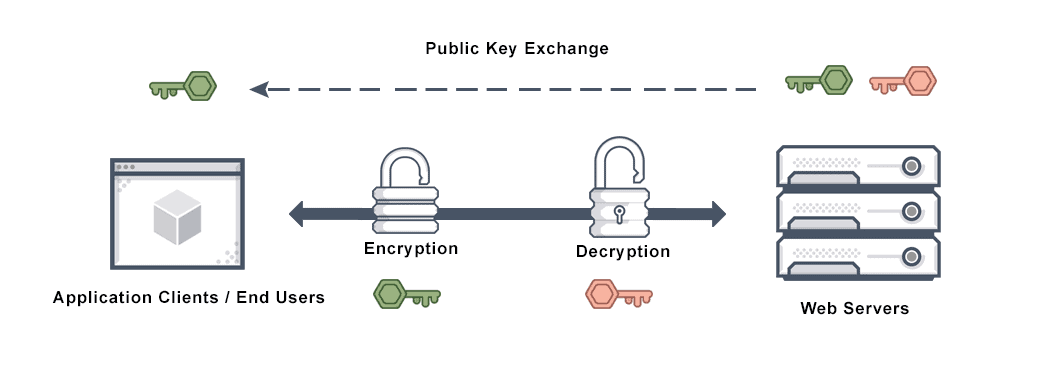
When a browser tries to access a website protected by SSL security, the web server and browser use a process called an SSL handshake to establish an SSL connection. This SSL handshake process happens instantaneously and is invisible to the user.
During the SSL handshake, the website and browser connect securely. The browser demands that the server identify itself so it can begin to ensure the connection is authenticated and encrypted. The server responds by sending the browser a copy of its SSL certificate and its public key.
The browser compares the certificate root to a list of trusted CAs to determine whether it can trust the certificate and the website is secure. If the certificate is unrevoked, unexpired, and has a valid common name for the website it is connecting to, the browser will use the server’s public key to create, encrypt, and return a symmetric session key.
The server then uses its private key to decrypt the symmetric session key. It encrypts and sends an acknowledgement using the session key, beginning the encrypted session. Now, the browser and server can use the session key to encrypt all data transmitted. This is why the handshake process is at the heart of how SSL security works.
What’s More Secure – SSL or HTTPS?
This is a common question, but actually a website has https:// or Hyper Text Transfer Protocol Secure appears in its URL when an SSL certificate secures it. By clicking on the lock symbol on the browser bar, you can see the details of the certificate, including the corporate name of the website owner and the issuing authority.
According to Google’s Webmaster best practices, SSL security and HTTPS addresses should be used everywhere on the web. As of 2014, Google has been rewarding SSL secured websites with better web rankings.
What is the Difference Between TLS and SSL Security?
Transport Layer Security (TLS) is actually just an improved, successor version of SSL. The TLS protocol works very similarly to the way SSL works, including using protecting data during transfer using encryption. In fact, TLS and SSL are often used interchangeably in the industry, although SSL is still widely used.
The most recent version is TLS 1.3, which is defined in RFC 8446 from the Internet Engineering Task Force (IETF) standards. In terms of which SSL/TLS version is secure, both SSL and its TLS successor can encrypt sensitive data such as credit card numbers, passwords, usernames, and other private information.
What Causes SSL Security Errors?
After initiating the SSL handshake and establishing the TCP connection, the server sends the user its certificate along with a number of specifications. Those details include which version of SSL/TLS to use, as well as which encryption methods.
When the user attempts to access a page with security issues, an SSL connection error occurs. This is because there are security concerns should they continue, so for their own protection, their access is interrupted.
SSL security errors can take a number of forms, sometimes depending on the browser. In some cases, the https:// of the page may be highlighted, while in others users might see a warning about a connection that is not private.
When setting up SSL security, if an admin misconfigures the system rendering it less secure, there is a danger of poor performance, reduced speed, failed transactions, and data loss. Obviously, SSL security is only as secure as the way the ciphers can compatibly allow client users to connect to specific applications.
Configuring ciphers is simpler in systems that allow admins to enable and deactivate specific ciphers and reorder them by dragging and dropping. Insights into proper security configuration and complex application delivery are also essential to better performance.
The right software-based load balancing platform can help prevent errors in SSL security configuration by revealing granular insights into SSL traffic flow. These insights help expose risks such as the POODLE vulnerability and DDoS attacks, and provide more visibility into what visitors are using, enabling further risk mitigation in real-time.
What is SSL Secure Shopping Online (Ecommerce)?
An SSL certificate will appear in a website’s address bar in that it will read https:// rather than http:// . Some sites in some browsers also show a padlock icon in the address bar to communicate that the connection is encrypted for SSL secure shopping.
Finally, those sites displaying a company name in the address bar in green have an Extended Validation SSL certificate for the most secure shopping experience. However, the mere presence of the padlock icon doesn’t always mean total security, due to data scooping by the NSA, other countries, and private companies, not to mention the Heartbleed bug leaking session data and courts ordering websites to reveal their SSL keys. Moreover, there are multiple vectors to attacking SSL and TLS.
Today the greatest weakness is the SSL private key itself, which is used to encrypt every session. If an attacker acquires that key even much later, decrypting any past transactions that were encrypted using the private key is possible.
There is a simple solution that both SSL and TLS support: Perfect Forward Secrecy. PFS generates a one-time “ephemeral” key to encrypt a single session and then discards it, instead of using the SSL certificate (and key) for encrypting a client’s connection directly.
PFS demands specific combinations of SSL settings, particularly the ephemeral Diffie-Hellman cipher suite, which it deploys for the key exchange. Most current web servers and OpenSSL support PFS and the Diffie-Hellman ciphers. Servers and infrastructure that don’t can still benefit from PFS thanks to newer, software-based load balancers.
Load Balancing and SSL
A load balancer often decrypts SSL traffic to improve performance. This works because decrypting at the load balancer saves the web servers from the extra CPU cycles and power it takes to decrypt data.
This process of decrypting traffic before passing it on is called SSL termination. Obviously, this means that the traffic between the web server and load balancer is no longer encrypted, increasing the risk of an attack, but keeping the load balancer in the same location reduces that risk.
A load balancer can also act as an SSL pass-through, allowing the web server to decrypt requests after passing them on. While this does tax the server’s power more, it provides extra security.
Can Avi’s Platform Support an SSL Security Policy?
Avi supports terminating client SSL and TLS connections as the virtual service. This requires Avi to send a certificate to clients that authenticates the site and establishes secure communications. Avi’s platform can also generate self-signed certificates for testing or safe environments. You can even import an existing certificate and its corresponding private key into Avi directly, such as from another server or load balancer.
For more on the actual implementation of load balancing, security applications and web application firewalls check out our Application Delivery How-To Videos.