Network Address Translation Definition
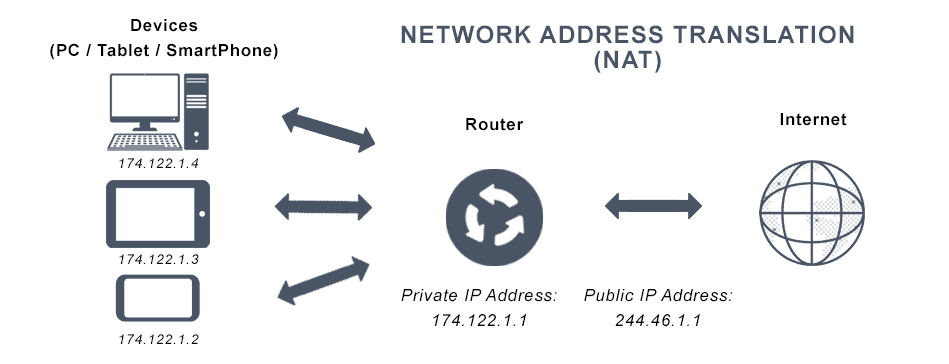
Network Address Translation (NAT) is a process that enables one, unique IP address to represent an entire group of computers. In network address translation, a network device, often a router or NAT firewall, assigns a computer or computers inside a private network a public address. In this way, network address translation allows the single device to act as an intermediary or agent between the local, private network and the public network that is the internet. NAT’s main purpose is to conserve the number of public IP addresses in use, for both security and economic goals.
Network Address Translation FAQs
What is Network Address Translation?
Network Address Translation (NAT) conserves IP addresses by enabling private IP networks using unregistered IP addresses to go online. Before NAT forwards packets between the networks it connects, it translates the private internal network addresses into legal, globally unique addresses.
NAT configurations can reveal just one IP address for an entire network to the outside world as part of this capability, effectively hiding the entire internal network and providing additional security. Network address translation is typically implemented in remote-access environments, as it offers the dual functions of address conservation and enhanced security.
What is the Purpose of NAT?
To communicate with the internet, a networking system requires a unique IP address. This 32-bit number identifies and locates the network device so a user can communicate with it.
The IPV4 addressing scheme of past decades technically made billions of these unique addresses available, but not all could be assigned to devices for communication. Instead, some were exempted and used for testing, broadcast, and certain reserved military purposes. While that left over 3 billion for communication, the proliferation of the internet has meant the addresses were near exhaustion.
The IPv6 addressing scheme was introduced as the solution to this weakness in the IPv4 addressing scheme. IPv6 recreates the addressing system so there are more options for allocating addresses, but it has taken several years to alter the networking system infrastructure and to implement. NAT was introduced by Cisco in the meantime and widely deployed.
How Network Address Translation Works
Network address translation permits a single device, such as a NAT firewall or NAT router or other network address translation device, to act as an agent between the public network and private networks—the internet and any local networks. This allows an entire group of devices to be represented by a single unique IP address when they do anything outside their network.
NAT works like a large company’s receptionist, with specific instructions on which calls and visitors to keep out, make wait, or send through, and where they should go. For example, you can tell the receptionist not to forward any visitors or calls without your request until you’re waiting for something specific; you can then leave instructions about letting that particular client communication through.
The client calls the company’s main number, because that public-facing number is the only one anyone knows. They tell the receptionist they need to speak with you, and the receptionist a) checks the instructions and knows you want the call forwarded, and b) matches your extension with a list to send the information to the right place. The caller never gets your private line.
Network address translation works similarly. The request arrives at the public IP address and port, and the NAT instructions send it where it should go without revealing the private IP addresses of the destinations.
NAT Network Address Translation Example
As a NAT network address translation example, an inside host may want to communicate with a destination network address translation web server address in the outside world. For further communication, it will send a data packet to the network’s NAT gateway router.
The NAT gateway router determines whether the packet meets the condition for translation by learning the source IP address of the packet and looking it up in the table. It can locate authenticated hosts for the internal network translation purposes on its access control list (ACL), and then complete the translation, producing an inside global IP address from the inside local IP address.
Finally, the NAT gateway router will route the packet to the destination after saving the translation in the NAT table. The packet reverts to the global IP address of the router when the internet’s web server reverts to the request. Referring back to the NAT table, the router can determine which translated IP address corresponds to which global address, translate it to the inside local address, and deliver the data packet to the host at their IP address. The data packet is discarded if no match is found.
Types of Network Address Translation
There are many forms of NAT and it can function in several ways.
Static network address translation SNAT. SNAT maps unregistered IP addresses using 1 to 1 network address translation to match up with registered IP addresses. It is particularly useful when a device needs to be accessible from outside the network.
Dynamic network address translation DNAT. This form of NAT selects a target from a group of registered IP addresses and maps an unregistered IP address to the registered version.
Reverse network address translation RNAT. RNAT allows users to connect to themselves using the internet or public network.
Overloading network address translation NAT. This is also known as NAT overload, port-level multiplexed NAT, single address NAT, or port address translation (PAT). This form of dynamic NAT uses different ports to map multiple private, local, unregistered IP addresses to a single registered IP address and distinguish which traffic belongs to which NAT IP address. In terms of port address translation vs network address translation, PAT is often most cost-effective when many users are connected to the internet through just one public IP address.
Overlapping network address translation NAT. Overlapping NAT can happen either when two organizations whose networks both use RFC 1918 IP addresses merge, or when registered IP addresses are assigned to multiple devices or otherwise in use on more than one internal network. In both cases, the networks need to communicate, and the organization(s) use overlapping NAT to achieve this without readdressing all devices.
The NAT router intercepts addresses, and maintains a table of them so that it can replace them with registered unique IP addresses. The network address translation router must both translate registered external IP addresses to those unique to the private network and translate internal IP addresses to registered unique addresses. It might achieve this either by using DNS to implement dynamic NAT or through static NAT.
In the network address translation context, the internal network, commonly referred to as the stub domain, is usually a local area network LAN that uses IP addresses internally. Most stub domain network traffic is local, remaining inside the internal network. A stub domain may include both unregistered and registered IP addresses.
Network Address Translation Configuration
A traditional NAT configuration requires at least one interface on a router (NAT outside); another interface on the router (NAT inside); and a configured set of rules for translating the IP addresses in the packet headers and possibly payloads.
In this example of network address translation configuration, IT configures the NAT router as follows. Whenever a device on the inside with an unregistered (inside, local) IP address needs to communicate with the (outside, public) network, the router translates those unregistered addresses residing on the private (inside) network to registered IP addresses.
- The organization receives a range of registered, unique IP addresses assigned by the ISP. The assigned list of addresses are called inside global addresses.
- The team splits unregistered, private addresses into one small group and one much larger group. The stub domain will use the larger group, called inside local addresses. The NAT routers will use the small group, called outside local addresses, to translate the outside global addresses or unique IP addresses of devices on the public network.
- Most stub domain computers communicate with each other using inside local addresses. There are inside global addresses for those stub domain computers that communicate extensively outside the network, meaning they do not require translation.
- However, when a typical stub domain computer with an inside local address needs to communicate outside the network, it sends the packet to a NAT router.
- The NAT router checks for the destination address in the routing table. If it has an entry for that address, the NAT router translates the packet and enters that action into the address translation table. The NAT router drops the packet if the destination address is not in the routing table.
- The router sends the packet on using an inside global address.
- A public network computer sends a packet to the private network. The packet’s destination address is an inside global address and its source address is an outside global address.
- The NAT router confirms that the destination address maps to a stub domain computer by checking the address translation table.
- The NAT router sends the packet to the destination computer after translating the packet’s inside global address to the inside local address.
NAT overloading uses multiplexing, a TCP/IP protocol stack feature. Multiplexing enables a computer to maintain multiple connections with remote computer(s) concurrently using different ports. The header of an IP packet contains:
Source Address. The originating computer’s IP address, for example, 123.123.12.1
Source Port. The assigned TCP or UDP port number for this packet, for example, Port 1060
Destination Address. The receiving computer’s IP address, for example, 52.220.51.237
Destination Port. The TCP or UDP network address translation port number the destination computer should open, for example, Port 2170
These four numbers combined represent a single TCP/IP connection. The addresses clarify the two computers at each end, and the port numbers provide a unique identifier for the connection between the two computers. Although there are a possible 65,536 values here since each port number uses 16 bits, different ports are mapped in slightly different ways, so about 4,000 available ports is realistic.
Dynamic NAT and NAT Overloading Configuration
In dynamic network address translation:
- IANA (Internet Assigned Numbers Authority), the global authority that assigns IP addresses, is the only source of unique IP addresses. Where a stub domain or internal network has been set up with IP addresses that IANA did not specifically allocate for them, the addresses are not unique and are therefore non-routable.
- The organization sets up a router enabled for NAT that contains a range of unique IP addresses from IANA.
- A stub domain computer attempts to connect to an outside computer.
- The router receives the stub domain computer’s packet.
- The NAT-enabled router saves the non-routable IP address from the sending computer to an address translation table. The router maps the first available IP address outside the zone of unique IP addresses to the sending computer to replace the non-routable IP address.
- The router now checks each packet’s destination address when it arrives from the destination computer, and verifies which stub domain computer the packet belongs to with the address translation table. If it finds no match, it drops the packet. Otherwise, it locates the alternative for the destination address saved in the address translation table and sends it.
- The computer receives the packet and the process continues as long as the external system and the computer communicate.
In NAT overloading:
- As in the previous dynamic NAT example, a stub domain or internal network has been set up with non-routable, non-unique IP addresses not specifically allocated for them, so the organization sets up a router enabled for NAT that contains a unique IP address from IANA.
- A stub domain computer attempts to connect to an outside computer.
- The NAT-enabled router receives the stub domain computer’s packet.
- The NAT router saves the non-routable IP address and port number from the sending computer to an address translation table. The router maps a port number and the router’s IP address to the sending computer to replace the non-routable IP address and port number.
- The router checks the destination ports of packets that return from the destination computer and confirms which stub domain computer the packet belongs to. It replaces the destination port and address with the saved versions from the address translation table and sends them.
- The computer receives the packet and the process continues as long as the external system and the computer communicate.
- The NAT router will continue to use the same port number throughout the connection, as it has the computer’s source port and address saved to the address translation table. If the communication ends without the entry being accessed again, the router removes the entry from the table.
In contrast to the computer described above in the traditional NAT configuration, this is how stub domain computers might appear to external networks:
Source Computer 1
IP Address: 192.168.24.11
Computer Port: 620
NAT Router IP Address: 215.37.32.203
NAT Router Port Number: 1
Source Computer 2
IP Address: 192.168.24.12
Computer Port: 80
NAT Router IP Address: 215.37.32.203
NAT Router Port Number: 2
Source Computer 3
IP Address: 192.168.24.13
Computer Port: 1560
NAT Router IP Address: 215.37.32.203
NAT Router Port Number: 3
The NAT-enabled router stores each source computer’s IP address and port number. It uses its own registered IP address and port numbers to replace the IP address and the port number that correspond to that packet’s source computer in the table. In place of the source-computer information on each packet, any external network sees the NAT router’s IP address and the assigned port number.
Some stub domain computers do use dedicated IP addresses. In these situations their IP addresses can pass by the NAT router untranslated if you create an access list of IP addresses that clarifies for the router which network computers require NAT.
A router’s Dynamic Random Access Memory (DRAM) is the main factor that determines the number of simultaneous translations that it can support. A typical address-translation table entry requires about 160 bytes, so for most applications, a router with 4 MB of DRAM is sufficient.
According to IANA and RFC 1918, there are specific ranges of IP addresses for use as internal network addresses that are non-routable. These addresses are unregistered, meaning no agency or company can use them on public computers or claim ownership over them. Instead of forwarding unregistered addresses, routers are designed to discard them. Therefore, a packet from an unregistered sending computer address could reach its registered computer destination, but the first router the reply came to would discard it.
To reduce the chance of an IP address conflict, it pays to follow the range for each of the three classes of IP addresses in your internal networking:
- Range 1: Class A – 10.0.0.0 through 10.255.255.255
- Range 2: Class B – 172.16.0.0 through 172.31.255.255
- Range 3: Class C – 192.168.0.0 through 192.168.255.255
However, this is a best practice, not a requirement.
NAT Router
Using NAT overload, a NAT router creates a network of IP addresses for a local area network LAN and connects the public network that is the internet to that LAN network. The router executes the NAT permitting communication between WAN or internet and the host devices or computers on the LAN network. Because NAT routers appear to be a solo host with a solo IP address to the internet, they are used for small scale industries and home purposes.
Advantages of Network Address Translation
Advantages of NAT
Address conservation. NAT conserves IP addresses that are legally registered and prevents their depletion.
Network address translation security. NAT offers the ability to access the internet with more security and privacy by hiding the device IP address from the public network, even when sending and receiving traffic. NAT rate-limiting allows users to limit the maximum number of concurrent NAT operations on a router and rate limit the number of NAT translations. This provides more control over the use of NAT addresses, but can also be used to limit the effects of worms, viruses, and denial-of-service (DoS) attacks. Dynamic NAT implementation creates a firewall between the internal network and the internet automatically. Some NAT routers offer traffic logging and filtering.
Flexibility. NAT provides flexibility; for example, it can be deployed in a public wireless LAN environment. Inbound mapping or static NAT allows external devices to initiate connections to computers on the stub domain in some cases.
Simplicity. Eliminates the need to renumber addresses when a network changes or merges.
Network address translation allows you to create an inside network virtual host to coordinate TCP load-balancing for internal network servers.
Speed. Compared to proxy servers, NAT is transparent to both destination and source computers, allowing for quicker direct dealing. In addition, proxy servers typically work at the transport layer or layer 4 of the OSI Reference Model or higher, making them slower than network address translation, which is a network layer or layer 3 protocol.
Scalability. NAT and dynamic host configuration protocol (DHCP) work well together, with the DHCP server doling out unregistered IP addresses for the stub domain from the list as necessary. Scaling up is easier, since you can increase the available range of IP addresses the DHCP configures to make room for additional network computers immediately instead of requesting more IP addresses from IANA as needs increase.
Multi-homing. Multiple connections to the internet, called multi-homing, helps maintain a reliable connection and reduces the chance of a shutdown in case of a failed connection. This also enables load-balancing via reducing the number of computers using any single connection. Multi-homed networks often connect to multiple ISPs, each assigning a range of IP addresses or a single IP address to the organization. Routers use network address translation to route between networks using different network address translation protocols. In a multi-homed network, the router uses part of the TCP/IP protocol suite, the border gateway protocol (BGP), to communicate; the stub domain side uses internal BGP or IBGP, and routers communicate with each other using external BGP or EBGP. Multi-homing reroutes all data through another router should one of the connections to an ISP fail.
Disadvantages of NAT
Resource consumption. Network address translation is a technology that consumes memory resources and processor space, because it must translate IPv4 addresses for all outgoing and incoming IPv4 datagrams and retain the details from translation in memory.
Delays. Path delays are caused by translation results in switching path delays.
Functionality. Some applications and technologies will not function as expected with NAT enabled.
Traceability. Network address translation complicates protocols for tunneling. IPsec is the secure protocol recommended for network address translation.
Layer issue. A router is a device for the network layer, yet as a NAT device it is required to tamper with the transport layer in the form of port numbers.
Does VMware NSX Advanced Load Balancer Offer a Network Address Translation Software Solution?
VMware NSX Advanced Load Balancer’s Platform, a software-defined application services fabric, enforces access control policies and captures and analyzes end-to-end application traffic, delivering services far beyond load balancing.
When new application servers are deployed, the servers need external connectivity for manageability. In the absence of a router in the server networks, the VMware NSX Advanced Load Balancer SE can be used for routing the traffic of server networks by using the IP routing feature of Service Engines. The Service Engine (SE) NAT functionality covers this, and serves as a NAT gateway for the entire private network of servers.
NAT will function either through IP routing on Service Engine, the SE default gateway feature, or in the post-routing phase of the packet path. To use outbound NAT functionality, it’s necessary to enable IP routing on the Service Engine and use the SE as a gateway.
VMware NSX Advanced Load Balancer supports outbound NAT for TCP/UDP, and ICMP flows.
There are three outbound NAT use case options:
- NAT Flows (show NAT flow information)
- NAT Policy Stats (show NAT policy stats)
- NAT Stat (show NAT statistics)
The platform also enables Source NAT or SNAT for application identification. The source IP address used by VMware NSX Advanced Load Balancer SEs for server back-end connections can be overridden through an explicit user-specified address—the source NAT (SNAT) IP address. The SNAT IP address can be specific as part of the virtual service configuration.
In some deployments, to provide differential treatment based on the application, it’s essential to identify traffic based on source IP address. For example, in DMZ deployments security, firewall, visibility, and other types of solutions may need to validate clients using the source IP before passing traffic on to an application.
Source NAT can be used with either high availability (HA) mode: elastic HA or legacy HA. The configuration requirements differ depending on whether the SE and back-end servers are in the same subnet (connected at Layer 2) or in different subnets (connected at Layer 3).
For more on the actual implementation of load balancing, security applications and web application firewalls check out our Application Delivery How-To Videos.