AWS Load Balancer Definition
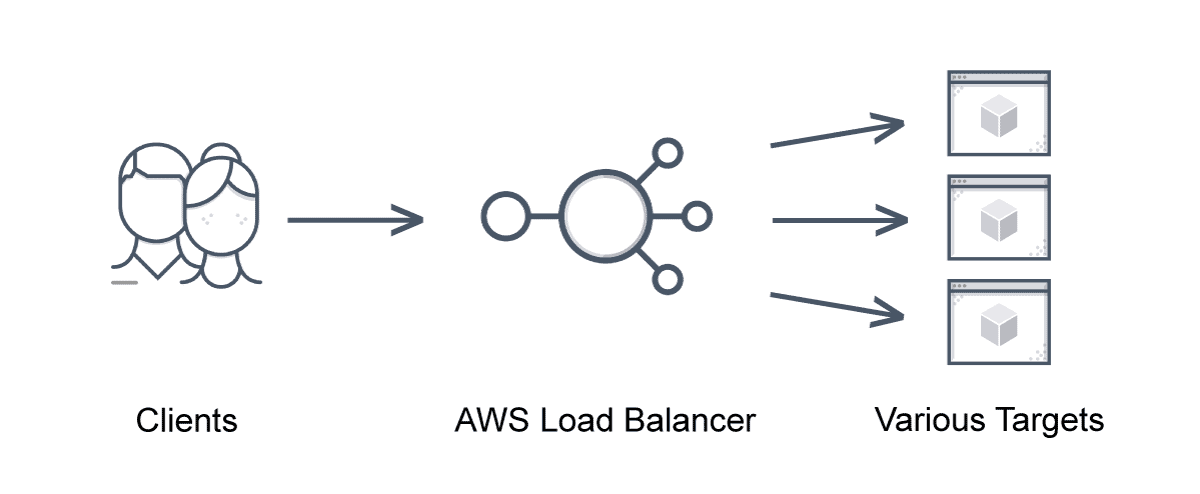
AWS load balancers accept incoming application traffic from clients and distribute it across various registered targets such as EC2 instances in multiple availability zones. The AWS application load balancer feature allows developers to route and configure incoming traffic in the AWS public cloud between end-users and applications.
A single point of contact for clients, the AWS elastic load balancer only routes to healthy instances and identifies unhealthy instances. Once the target is operational, the AWS load balancer algorithm resumes routing traffic to it.
Load balancing is essential in cloud environments with multiple web services.
AWS Load Balancer FAQs
What is AWS Load Balancer?
AWS Elastic Load Balancing (ELB) distributes incoming application traffic automatically across multiple targets such as containers, EC2 instances, and IP addresses in one or more availability zones. This distributes and balances how frontend traffic reaches backend servers and increases the fault tolerance and availability of user applications. AWS load balancing also monitors registered targets for health and routes distributes traffic accordingly.
AWS Load Balancer Types
There are four AWS load balancer types supported:
- AWS Classic Load Balancer
- AWS Network Load Balancer (NLB)
- AWS Application Load Balancer (ALB)
- AWS Gateway Load Balancer (GLB)
The previous-generation AWS classic type of load balancer is now only recommended where users have instances running on an EC2-Classic network. For all other users, AWS Classic Load Balancer features can be replaced by either AWS Network Load Balancer (NLB) or AWS Application Load Balancer (ALB).
(AWS Gateway Load Balancer does not distribute traffic across multiple targets, so its applications are less broad. In terms of AWS load balancer differences this is the most significant for most users.)
Take a closer look with an AWS load balancers comparison:
AWS Classic Load Balancer
This simple load balancer operates both at the request level and the connection level and was originally used for classic EC2 instances. Its primary disadvantage is that it does not support certain features, such as route-based or host-based routing. A well-configured load balancer can improve efficiency and performance by distributing the load among the servers regardless of what they contain.
AWS Application Load Balancer
The Application Load Balancer (ALB) is an OSI model layer 7 load balancer that routes network packets based on their contents to different backend services. In contrast to the classic AWS elastic load balancer which would need to run for each service, an AWS application load balancer delivers AWS layer 7 load balancing that can balance the network traffic of many backend services.
This new generation load balancer offers native support for WebSocket and HTTP/2 protocols. WebSocket allows developers to minimize power consumption even as they configure persistent TCP connections between client and server. HTTP/2 reduces network traffic by multiplexing requests over a single connection.
AWS Load Balancer Classic vs Application Load Balancer
AWS application load balancer performance is higher and supports more features compared with the classic load balancer, such as the following
- IP address registration as targets
- Path-based/host-based routing
- Calling Lambda functions to serve HTTP(S) requests
- AWS WAF load balancer
- SNI
- Enhanced containers via load balancing between multiple ports of a single instance
Network Load Balancer AWS
AWS recommends AWS Network Load Balancer (NLB) if the application needs to achieve static IP and extreme performance. In terms of the AWS application vs network load balancer comparison, the NLB is better optimized to manage traffic patterns that are unstable and spiky and workloads that fluctuate rapidly.
NLB delivers high throughput and scales to handle millions of requests per second. This means network load balancer is better suited for achieving extreme network performance and handling bursty workflows at the transport layer. AWS network load balancers also avoid DNS caching problems and work with existing firewall security policies of users thanks to its static and resilient IP addresses. And AWS load balancer TLS termination is only possible with NLB.
How AWS Load Balancer Works
The AWS load balancer increases application availability by serving as a single point of contact for clients. Users can seamlessly add and remove instances from the AWS load balancer without disrupting the overall request flow to the application as needs change over time. In this way, AWS elastic load balancing scales as application traffic fluctuates and can in fact scale to most workloads automatically.
Users add one or more listeners to the load balancer. A listener uses the configured port and protocol to check for connection requests from clients and forwards requests using the configured port number and protocol to registered instances. Health checks ensure the AWS load balancer sends requests only to healthy instances.
The AWS load balancer distributes traffic evenly across enabled availability zones by default. To improve fault tolerance, maintain instances in approximately equivalent numbers across availability zones. You can also enable cross-zone load balancing. This type of elastic load balancing supports even traffic distribution across all registered instances.
Enabling an availability zone creates a load balancer node inside the availability zone. Targets, even if they are registered, do not receive traffic if the availability zone is not enabled.
In addition, even the classic AWS load balancer algorithm works best with at least one registered target in each enabled availability zone, but enabling multiple availability zones for all load balancers. AWS application load balancers require enablement of at least two availability zones to ensure continuous routing of traffic.
Targets in a disabled availability zone remain registered with the AWS load balancer, but they do not receive traffic. Learn more in the AWS developer guide.
AWS Load Balancer Features and Benefits
The AWS load balancer is designed to ensure elasticity of resources and high availability. Here are some of the key AWS load balancer benefits
- High availability and distribution of website traffic to multiple destinations or targets.
- Adjusting without human intervention to major changes in website traffic.
- SSL/TLS decryption and user authentication functions offer high security.
- Hybrid load balancing can assist in migrating cloud resources.
- Continuous auditing and monitoring delivers increased visibility of your applications.
- Support for AWS certificate manager.
Here is a closer look at some of the more important AWS load balancer attributes and features.
Amazon EC2 Auto Scaling
- Maintain application availability with Amazon EC2 Auto Scaling and add or remove EC2 instances automatically and with dynamic and predictive scaling features according to defined conditions.
- Maintain the fleet availability and health using Amazon EC2 Auto Scaling fleet management features.
- Use predictive scaling and dynamic scaling in tandem for more rapid scaling.
AWS Load Balancer Reverse Proxy
AWS Application Load Balancer can be used as a reverse proxy, but it supports no dynamic targets, only static targets. In other words, it supports fixed IP addresses but not domain names.
AWS Internal vs External Load Balancer
How do the AWS internal and external load balancers differ?
An internal load balancer routes traffic to EC2 instances in private subnets which clients must be able to access. Even a Route53 record pointing to an internal load balancer cannot grant access to a client not on the virtual private cloud (VPC).
External load balancers, whose nodes have public IP addresses, are needed for clients who are not on the VPC to connect. External load balancers, sometimes called internet-facing load balancers, have DNS names that are publicly resolvable to the public IP addresses of the nodes. This allows them to route requests from all over the internet.
Internal load balancer nodes have private IP addresses only, and the internal load balancer’s DNS name is publicly resolvable to those private IP addresses. Therefore, internal load balancers can accept and handle requests only from clients who can access the virtual private cloud.
AWS Load Balancer Failover
Use auto scaling groups and AWS elastic load balancing health checks to identify and cycle out failing instances automatically, with no downtime. Each app is deployed to its own cluster of instances. An Auto Scaling Group (ASG) and an ELB control that cluster. The ASG controls how many instances exist in the cluster, and when to adjust that number.
The ASG verifies the health of an instance each time it boots one, and verification can have two outcomes. If the instance passes the health check, the ASG allows it to run and the ELB marks it “In Service” so it can send it incoming traffic.
If something is wrong with the instance or the app on it and the instance fails the health check, the ASG gives it a grace period as the ELB marks it as “Out of Service” until eventually the ASG replaces it.
Monitoring is continuous, and the ELB will mark any instance that fails health checks and stop routing traffic so the ASG can respond and replace it.
AWS Load Balancer Controller
AWS Load Balancer Controller, sometimes called AWS Load Balancer Kubernetes and formerly called “AWS ALB Ingress Controller“, manages elastic load balancers in Kubernetes clusters. It provisions application load balancers to satisfy Kubernetes Ingress resources and provisions Network Load Balancers to satisfy Kubernetes Service resources.
AWS Load Balancer Path Routing
AWS load balancer path routing, also called path-based routing or URL-based routing, is a unique feature of the AWS application load balancer. The ALB forwards requests to specific targets based on configured rules.
AWS Load Balancer Configuration
Use the web-based AWS Management Console interface to create and configure an AWS load balancer.
Before you begin, choose which two availability zones you’ll use for your EC2 instances. In each availability zone, configure at least one public subnet into the virtual private cloud (VPC); these are used to configure the load balancer. In addition, users can launch EC2 instances in other subnets of the availability zones.
Each availability zone should have one or more EC2 instances with a web server such as Ngnix or Apache installed. Security groups must enable HTTP access for these instances on port 80.
Then, use AWS configure load balancer documentation to
- Select which type of AWS load balancer to use
- Complete basic configuration
- Configure a security group
- Configure a target group
- Register targets
- Create a load balancer and test it
- Get more details on how to configure AWS load balancers
Limitations of AWS Load Balancer
AWS load balancers do a good job with basic functions, but they face a few significant challenges.
AWS Load Balancer Latency
AWS load balancer latency is among the system’s most notable limitations. With a classic load balancer several things can cause high latency, starting with faulty configuration. Beyond that, the high latency trouble spots are basically the same for the AWS application load balancer, especially relating to backend instances:
- Faulty configuration
- Network connectivity problems
- And as to backend instances
- High CPU utilization
- High memory (RAM) utilization
- Faulty web server configuration
- Issues caused by web application dependencies such as Amazon S3 buckets or external databases running on backend instances
Scalability: AWS Load Balancer vs Autoscaling
The load balancer and auto scaling AWS have their closest nexus in the updated network load balancer (NLB) offerings. These interact in Layer 4 and can terminate incoming TCP/TLS connections, ensure an onward connection for the upstream target, and determine what that target is.
The AWS network load balancer manages, adds, and removes available targets as a target group, making the upstream target pool elastic. In many ways, AWS network load balancers excel, but they still face a few notable scalability and elasticity challenges.
Target Group Limit
The AWS network load balancer limits the number of frontend server instances that can belong to a target group. According to AWS documentation this is based on a number of quotas, which users may adjust via account management operations.
However, the constraints of AWS load balancer architecture mean that these quotas are more like hard limits for the system. To deal with this you can attempt to increase target size with vertical scaling or use multiple NLBs, but neither solution is complete or offers the seamless experience users hope for.
Connection Stability
When high numbers of established connections are passing through a single network load balancer, they sometimes drop suddenly with no apparent cause. There can also be a delay before the NLB reconnection attempts succeed and the system re-admits traffic.
This problem in connection stability for single NLBs handling high numbers of connections is due to limits in architectural design, and essentially caps the number of connections a lone NLB can maintain.
Other Considerations
Solutions such as AWS application load balancer (ALB) or even NLB lack real-time application analytics, traffic management across clouds, and robust load balancing capabilities. Similarly, virtual appliances cannot support the elasticity and automation cloud-native applications demand, nor can they scale across multiple clouds. And traditional load balancers are designed to be based in appliances, not cloud environments. These legacy solutions also demand tedious management of individual instances and manual configuration, and lack native integration with features popular with developers and AWS APIs.
Does VMware NSX Advanced Load Balancer Offer an AWS Load Balancer Alternative?
Yes. The VMware NSX Advanced Load Balancer Platform offers advanced security, application analytics, application monitoring, full-featured load balancing, multi-cloud traffic management, on-demand autoscaling, and more. The VMware NSX Advanced Load Balancer deploys in virtualized, bare metal, or container environments, far exceeding what AWS load balancers and other legacy tools can do.
Amazon ALB and ELB lack advanced policy support and enterprise-class features, and provide only basic load balancing. The VMware NSX Advanced Load Balancer delivers enterprise-grade full-featured load balancing and advanced policy support:
- Advanced HTTP content switching capabilities
- Comprehensive persistence
- Customizable health monitoring
- DNS services and GSLB across multiple clouds
Learn more here.
For more on the actual implementation of load balancing, security applications and web application firewalls check out our Application Delivery How-To Videos.