Configuring Firewall Rules in GCP
Overview
Google Cloud Platform (GCP) firewall rules let you allow or deny traffic to and from your virtual machine (VM) instances based on a configuration you specify. By creating a firewall rule, you specify a Virtual Private Cloud (VPC) network and a set of components that define what the rule does. For more information refer to GCP Firewall Rules.
Firewall rules need to be configured to allow ingress and egress traffic for the Avi Controller, service engines (SE), and the application servers.
Note: By default egress is allowed in GCP for all protocols and ports but if egress is denied by some firewall rules, then the specific destination protocol and port have to be allowed.
Skip the egress rule configuration if egress traffic is allowed.
Configuring firewall rules allow the following communication:
-
Management Traffic
a. The Controller - Service engines
b. Network services used by the Controller
c. Service engine - Service engine -
Data Traffic
a. Virtual service traffic on service engines
b. Service engine - Application servers
c. Application servers
Using the steps below create the following firewall rules.
Note: Make a note of the Target tags which will be created below since the target tags will be applied on the Avi Controller and the Service Engine virtual machines.
Management Traffic
For the list of protocols and ports required for ingress and egress management traffic, refer to the Protocol Ports Used by Avi Vantage for Management Communication.
Controller Firewall Rules
Configuring Controller Ingress Rules
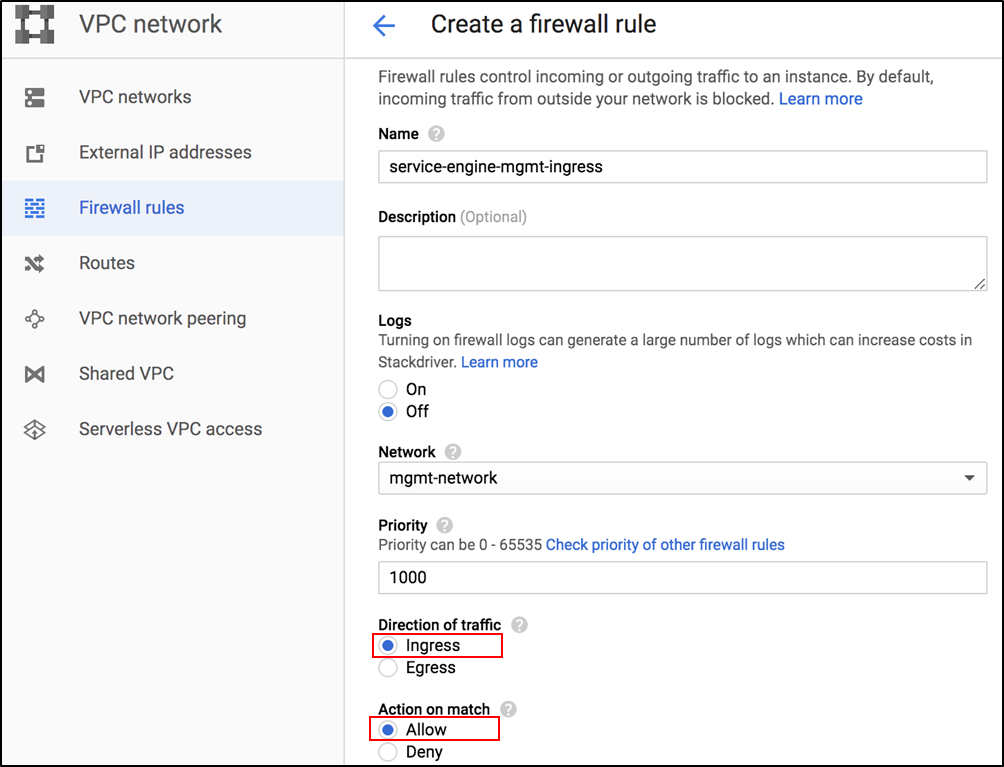
To configure a firewall rule to allow ingress traffic for the Avi Controller,
-
From the GCP console, navigate to VPC network > Firewall rules.
-
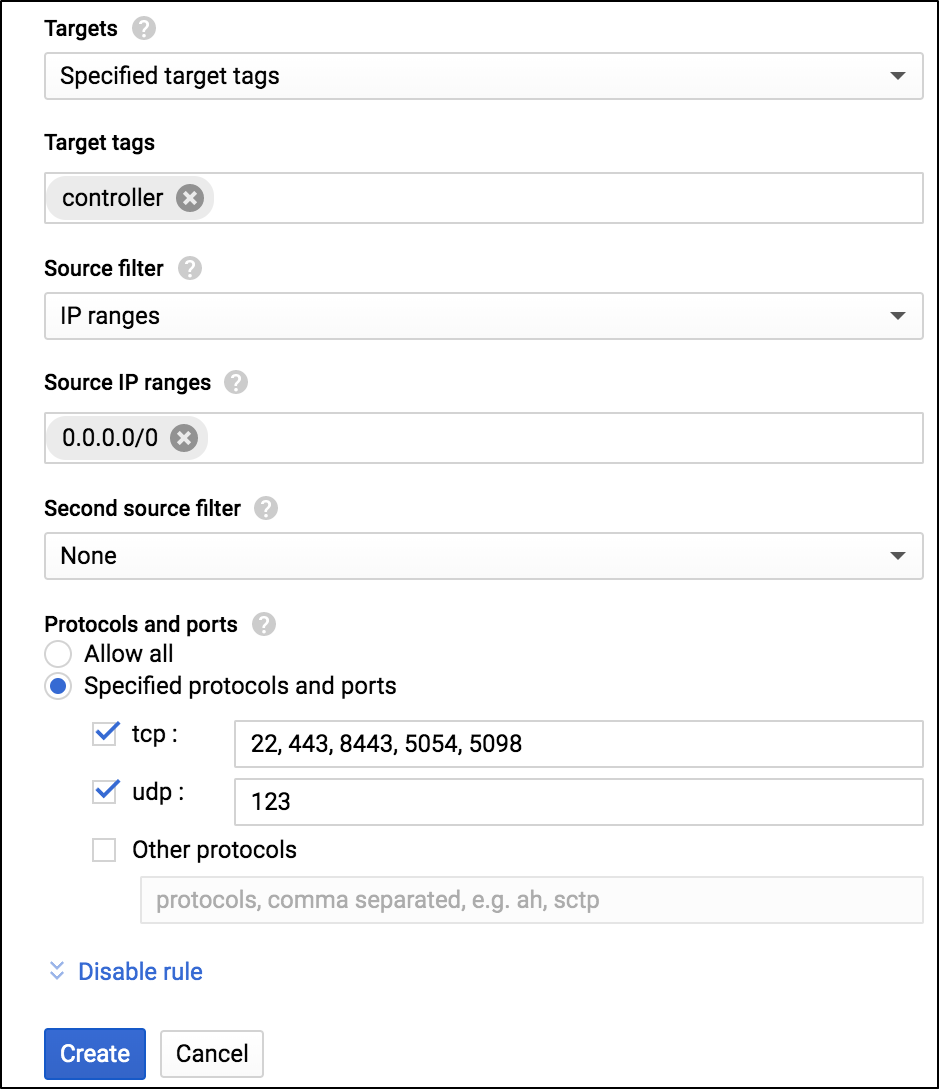
In the Create a firewall rule screen, select Ingress as the Direction of traffic and Allow as the Action on match, as shown below:
Allow Ingress Traffic for Controller
- Select Specified target tags to apply the firewall rules only to the selected instances within the virtual network.
- Enter the Target tags.
-
Select the option Specified protocol and ports and enter the tcp, udp ports to which the firewall rules are applicable.
Allow Ingress Traffic for Controller
- Click on the Create button.
Firewall rule to allow ingress traffic for the Controller is now configured.
Configuring Controller Egress Rules
Egress rules are configured to allow traffic from the Controller for network services and SE communication.
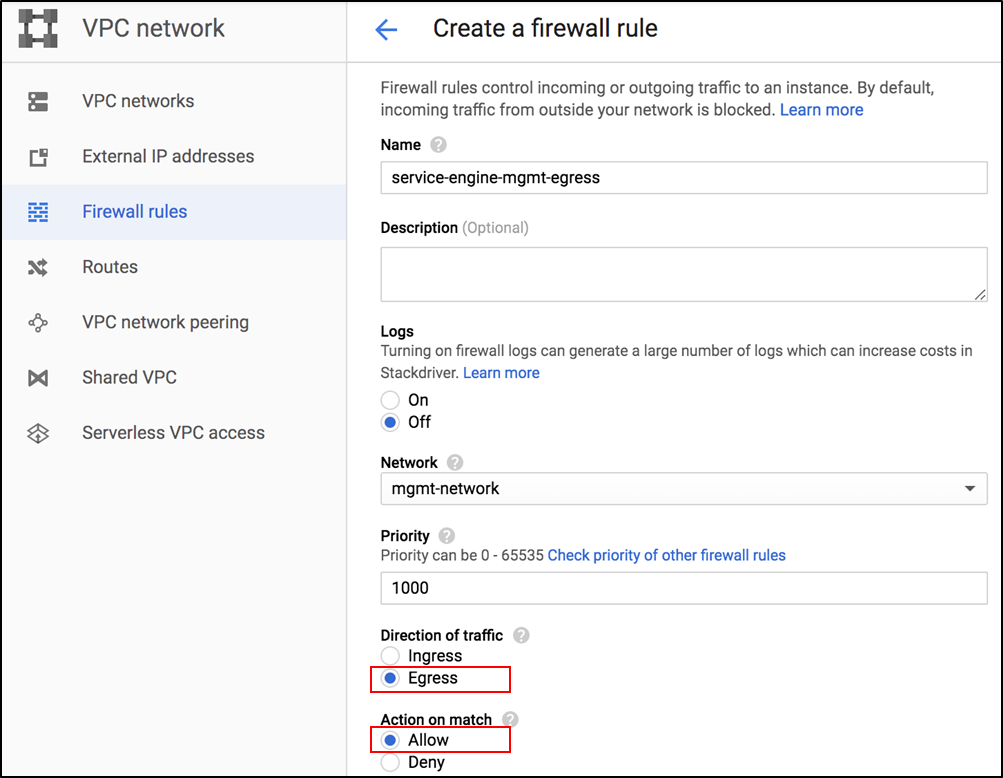
To configure firewall rules to allow outgoing traffic from a Controller,
-
In the Create a firewall rule screen, select Egress as the Direction of traffic and Allow as the Action on match, as shown below:
Allow Egress Traffic from the Controller
- Enter the Target tags.
- Select the option Specified protocol and ports.
-
Refer to the Protocol Ports article to identify the ports to which the Controller sends traffic to as a part of the network operation. Add the ports as shown in the image below:
Allow Egress Traffic from the Controller
- Click on the Create button.
Service Engine Firewalls
Service Engine to Service Engine Traffic
The following protocols and ports are required for SE-SE management traffic
| Protocol | Ports |
|---|---|
| 75 | - |
| 97 | - |
| UDP | 1550 |
Configuring Service Engine Ingress Rules
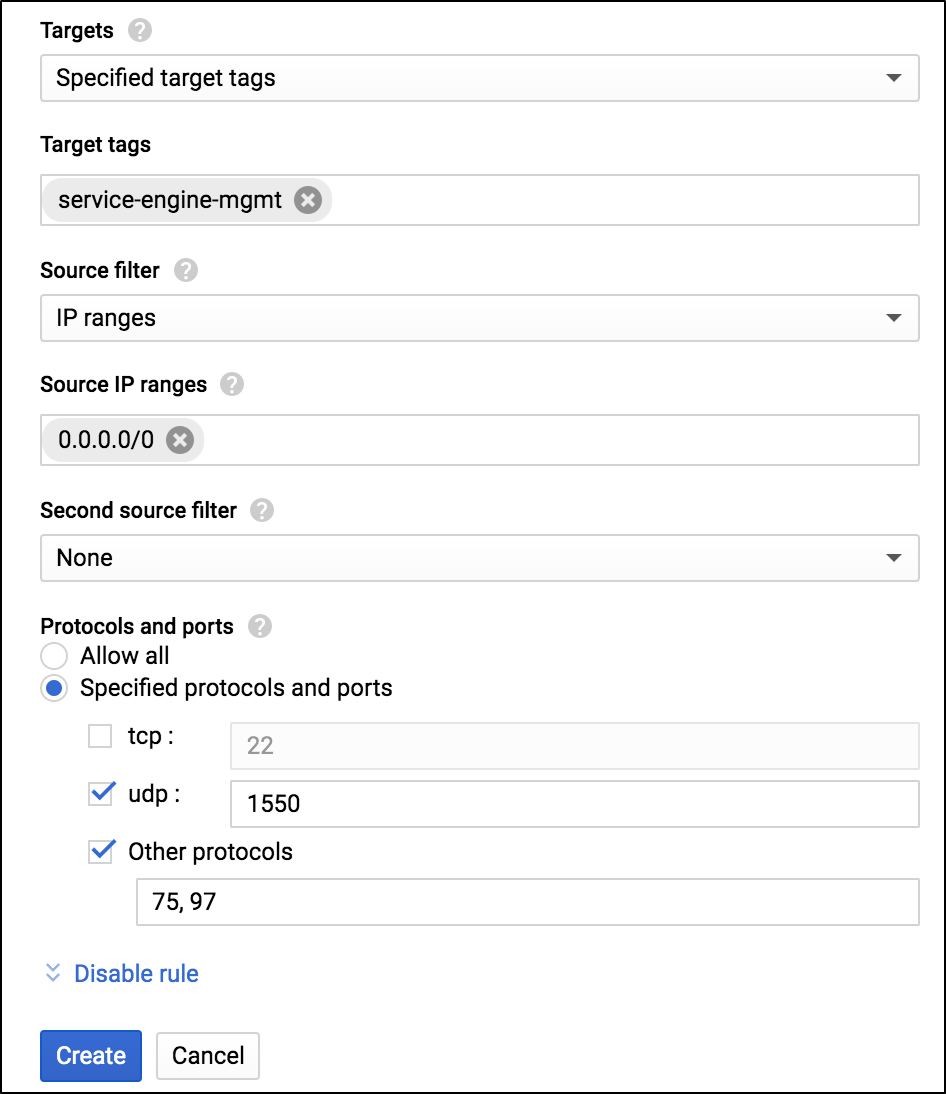
This rule is required to allow Ingress traffic from one SE to another SE.
To allow ingress traffic for SE to SE management traffic,
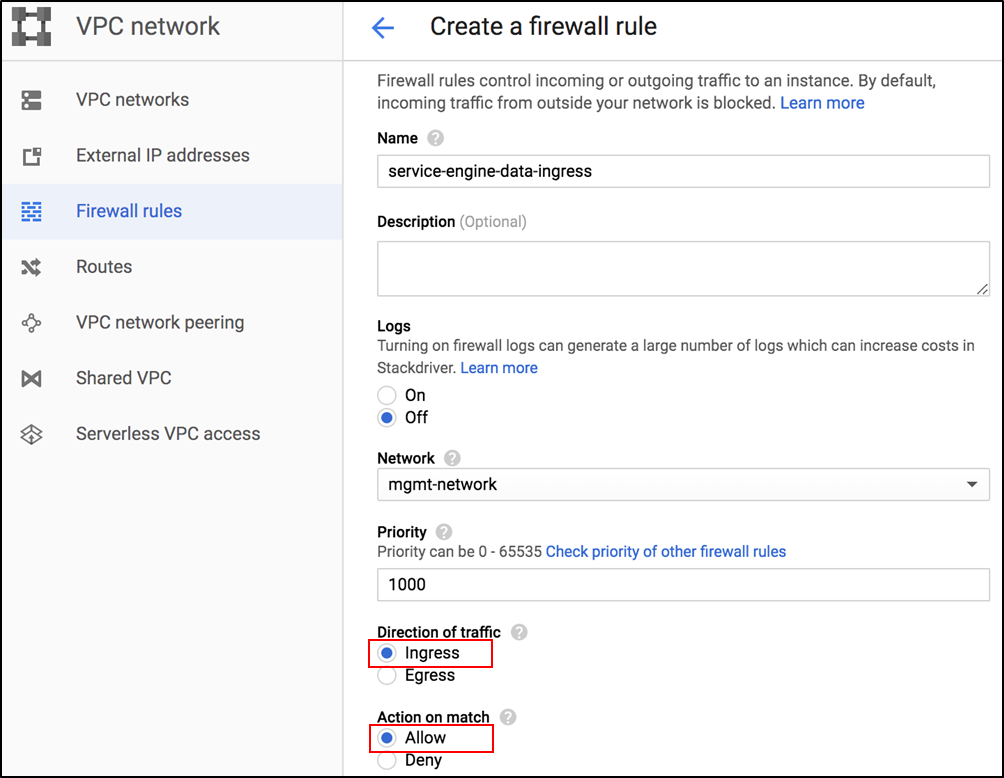
-
In the Create a firewall rule screen, select Ingress as the Direction of traffic and Allow as the Action on match, as shown below:
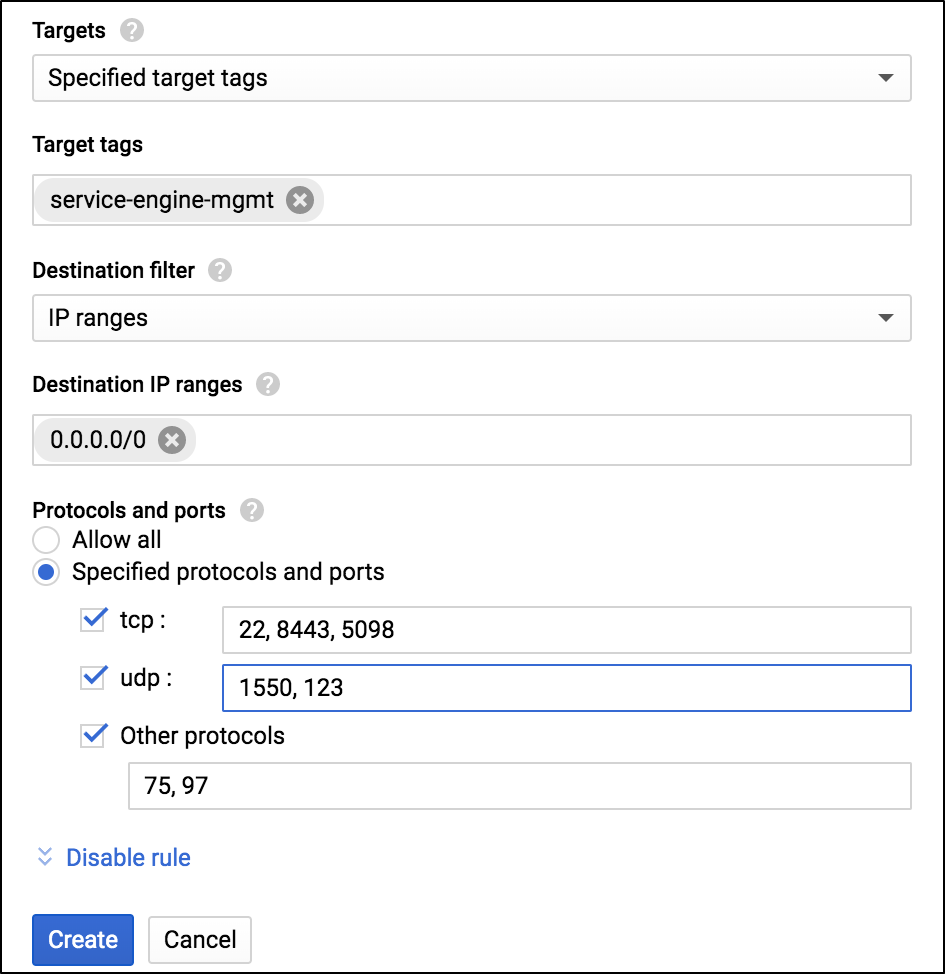
Allow Ingress Traffic from the SE
- Enter the Target tags.
-
Select the option Specified protocol and ports.
Allow Ingress Traffic from the SE
- Click on the Create button.
Configuring Service Engine Egress Rules
This rule is required to control egress traffic from SE to the Controller and SE to SE.
To allow egress traffic,
-
In the Create a firewall rule screen, select Ingress as the Direction of traffic and Allow as the Action on match, as shown below:
Allow Egress Traffic for the SE
- Enter the Target tags.
-
Select the option Specified protocol and ports.
Allow Egress Traffic from the SE
- Click on the Create button.
Firewall Rule Filtering with Service Accounts
Firewall rules in GCP can be made more specific in nature by using service accounts for source and destination filtering.
You can create new SE instances with service accounts provided.
Adding Service accounts to GCP instances
-
Service account can be added to an instance on its creation.
-
Service account can not be added to an already running instance. In such case, the instance needs to be stopped before adding the Service account, and after adding the service account, the instance needs to be started again for the change to take effect.
Notes:
-
Service account will only be added to newly created SEs, and not the existing SEs.
-
Reconcile will not happen for service account, as the SEs will need to be stopped and restarted for making any service account related change.
For more details on assigning roles to service account, refer to Roles and Permissions (GCP Full Access) guide.
Data Traffic
Configuring Service Engine Ingress Rules for Virtual Service Ports
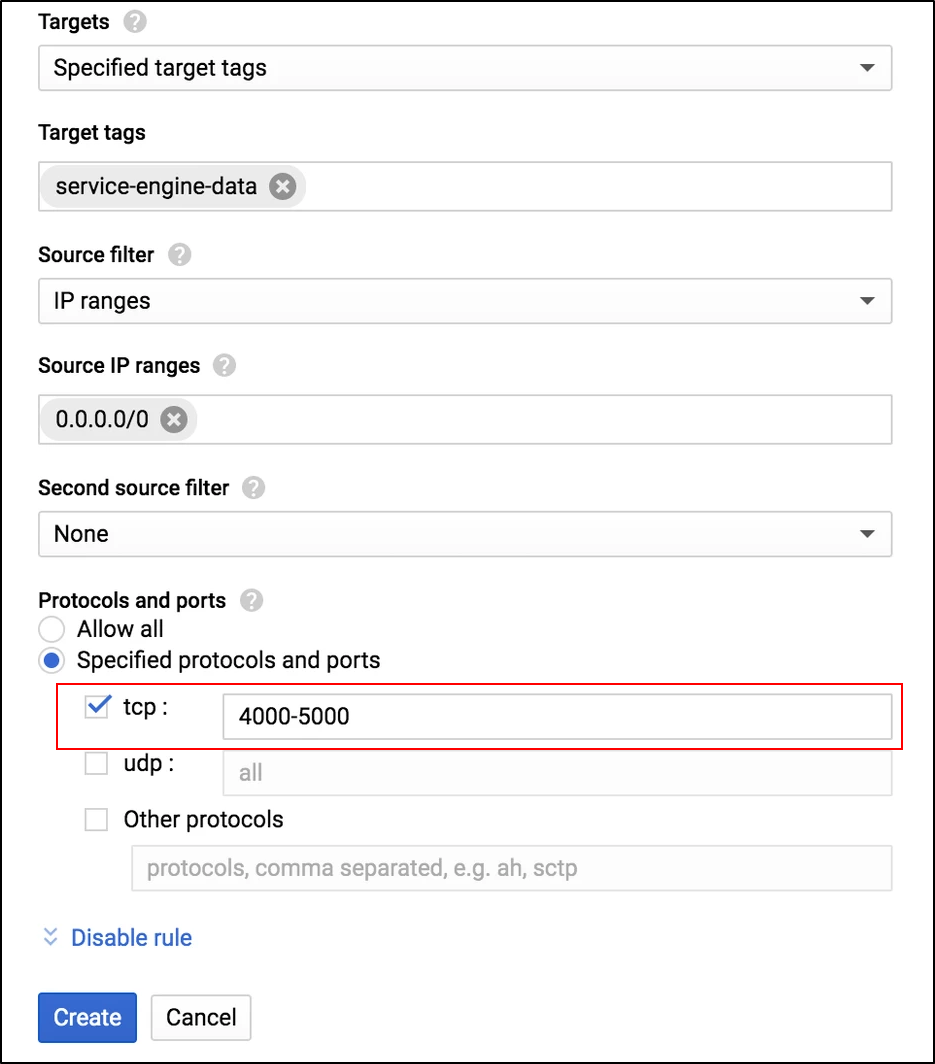
For data traffic, allow ingress for all the virtual service ports.
For example, here TCP: 4000-5000 is allowed for the virtual service traffic.
To allow ingress for data traffic,
-
In the Create a firewall rule screen, select Ingress as the Direction of traffic and Allow as the Action on match, as shown below:
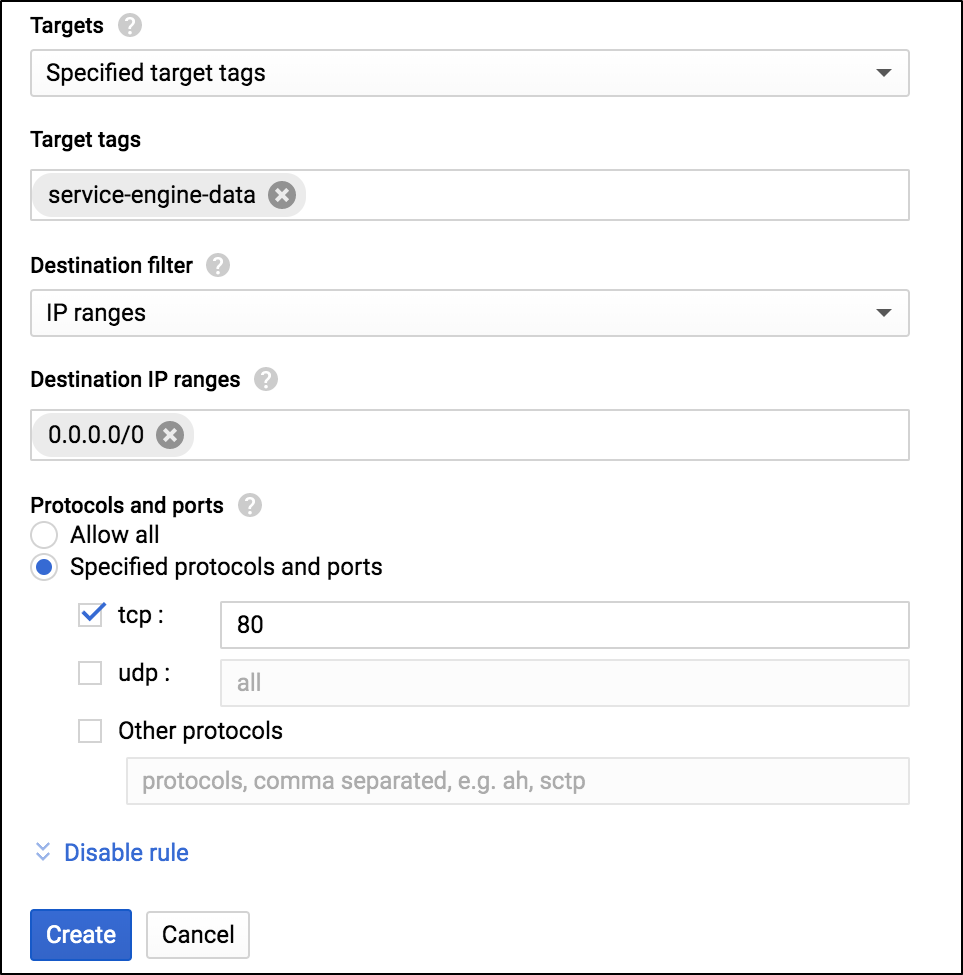
Allow Ingress for Data Traffic
- Enter the Target tags.
-
Select the option Specified protocol and ports.
Allow Ingress for Data Traffic
- Click on the Create button.
Configuring Service Engine Egress Rules
Configure this rule to allow sending traffic to the backend server ports.
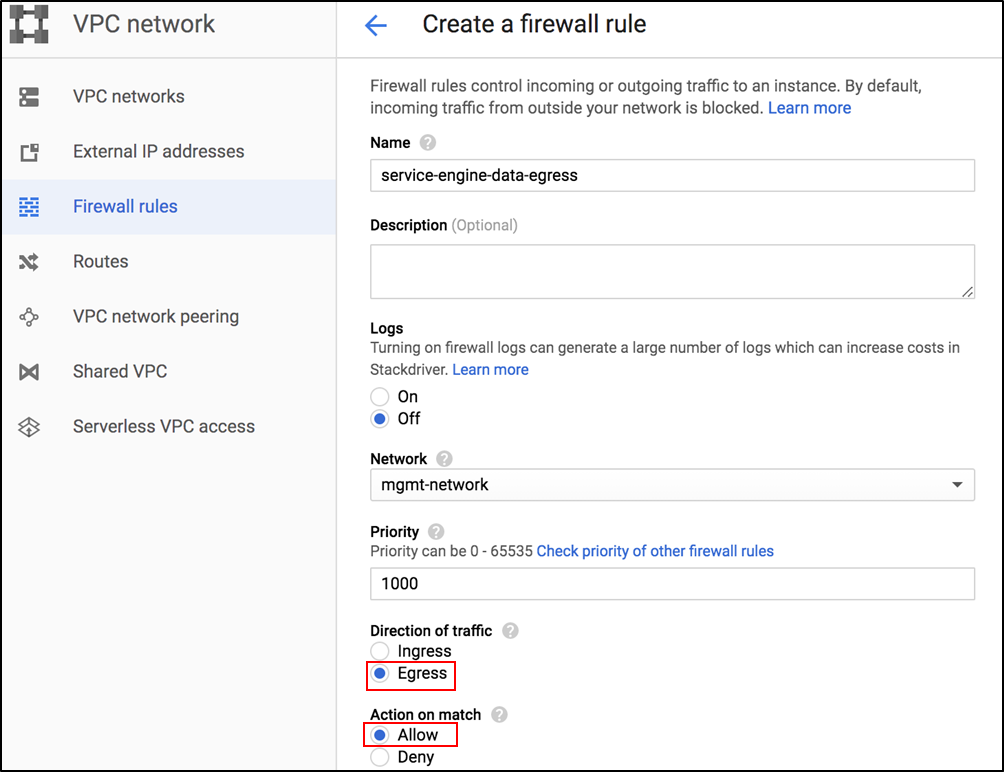
To allow egress for data traffic,
-
In the Create a firewall rule screen, select Egress as the Direction of traffic and Allow as the Action on match, as shown below:
Allow Egress for Data Traffic
- Enter the Target tags.
-
Select the option Specified protocol and ports.
Allow Egress for Data Traffic
- Click on the Create button.
Application Servers
Similarly, create the firewall rules for application servers for ingress and egress to access the application.