Logout Support in OIDC
Overview
Starting with NSX Advanced Load Balancer version 22.1.3, Client/Relying Party (RP)-initiated Logout for OpenID is supported.
NSX Advanced Load Balancer being the OAuth Client (RP) initiates a request that directs the Identity Provider (IDP) to log out by redirecting the user agent of the user to the IDP’s Logout endpoint.
Note: RP-initiated Logout is applicable only if OIDC is enabled.
NSX Advanced Load Balancer-Initiated Logout Flow
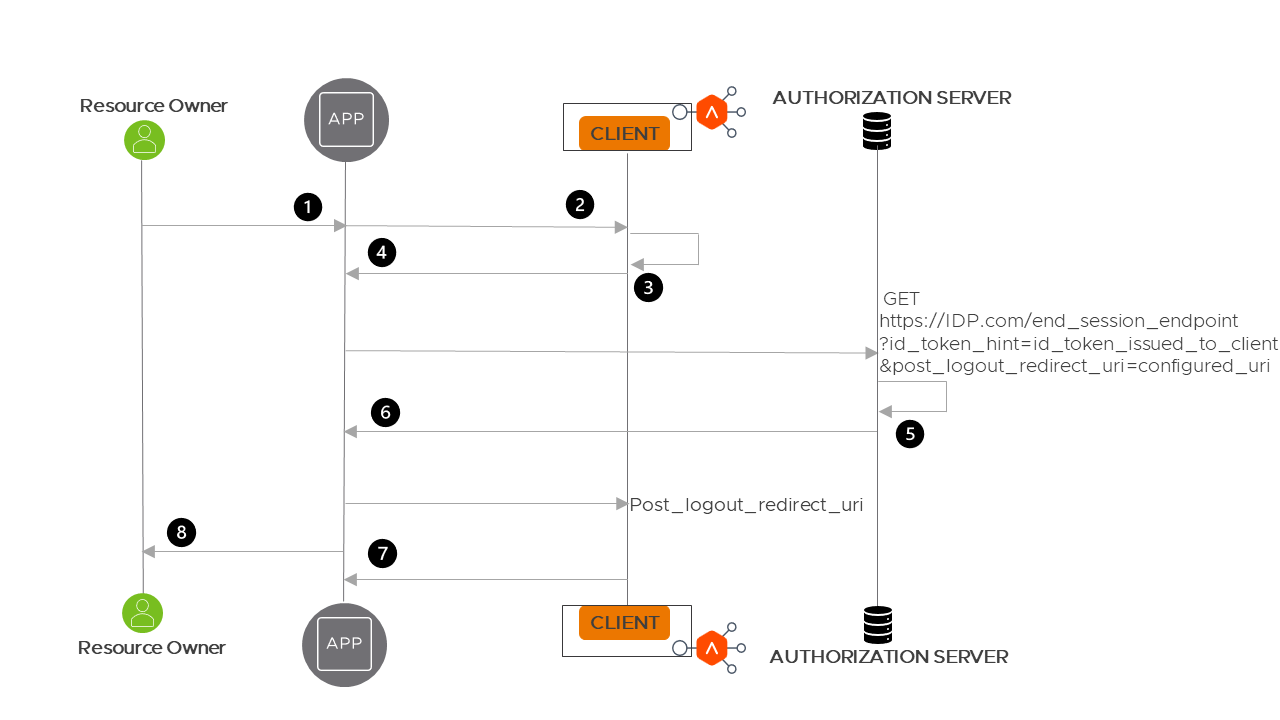
The flow of the NSX Advanced Load Balancer-initiated logout is explained below:
-
The Resource Owner/User clicks the Logout button provided by the application and navigates to the logout URI (e.g., /oauth/logout), which is configured in NSX Advanced Load Balancer.
Note: The Logout button is provided by the application and not by NSX Advanced Load Balancer. -
App/Browser sends the logout request to NSX Advanced Load Balancer.
-
NSX Advanced Load Balancer clears out the session details of the user from the session DB.
- NSX Advanced Load Balancer sends the redirect request to Authorization Server/IDP’s end session endpoint (which is configured in NSX Advanced Load Balancer) with the invalid cookie to clear out the NSX Advanced Load Balancer to App/Browser cookies.
GET https://IDP.com/end_session_endpoint?id_token_hint=id_token_issued_to_client&post_logout_redirect_uri=configured_uri -
Authorization Server/IDP clears the session details of the user and,
a. The admin must first configurepost_logout_redirect_uriat the IDP (e.g., okta) end, to which IDP redirects the user after logout is performed.
b. Otherwise, NSX Advanced Load Balancer will configure / as defaultpost_logout_redirect_uri. -
Authorization Server/IDP redirects to the NSX Advanced Load Balancer endpoint at
post_logout_redirect_uri. -
The user can log out successfully.
- After the successful logout, the user must provide the credentials to again access the resources, and NSX Advanced Load Balancer initiates the OAuth login flow.
Note: The above flow is applicable only when there is a valid session cookie sent by the client on clicking the Logout button.
URI Endpoints
The use of three URI endpoints in RP-Initiated logout are as follows:
-
Logout URI (Mandatory) - This endpoint is configured in NSX Advanced Load Balancer and the Logout button in the application navigates to this endpoint.
-
End Session Endpoint (Mandatory) - This endpoint is configured in NSX Advanced Load Balancer and provided by IDP.
-
Post Logout Redirect URI (Recommended) - The endpoint URI to which the RP requests that the end-user’s user agent be redirected after a logout has been performed. The same value must be configured in the IDP and NSX Advanced Load Balancer.
Configuring RP-Initiated Logout
Using the UI
The prerequisite configuration steps for OIDC are explained here.
- Navigate to Applications > Virtual Services.
- Click Create or edit the existing Virtual Services.
- Navigate to Policies > Access.
- Under Access Policy, select OAUTH.
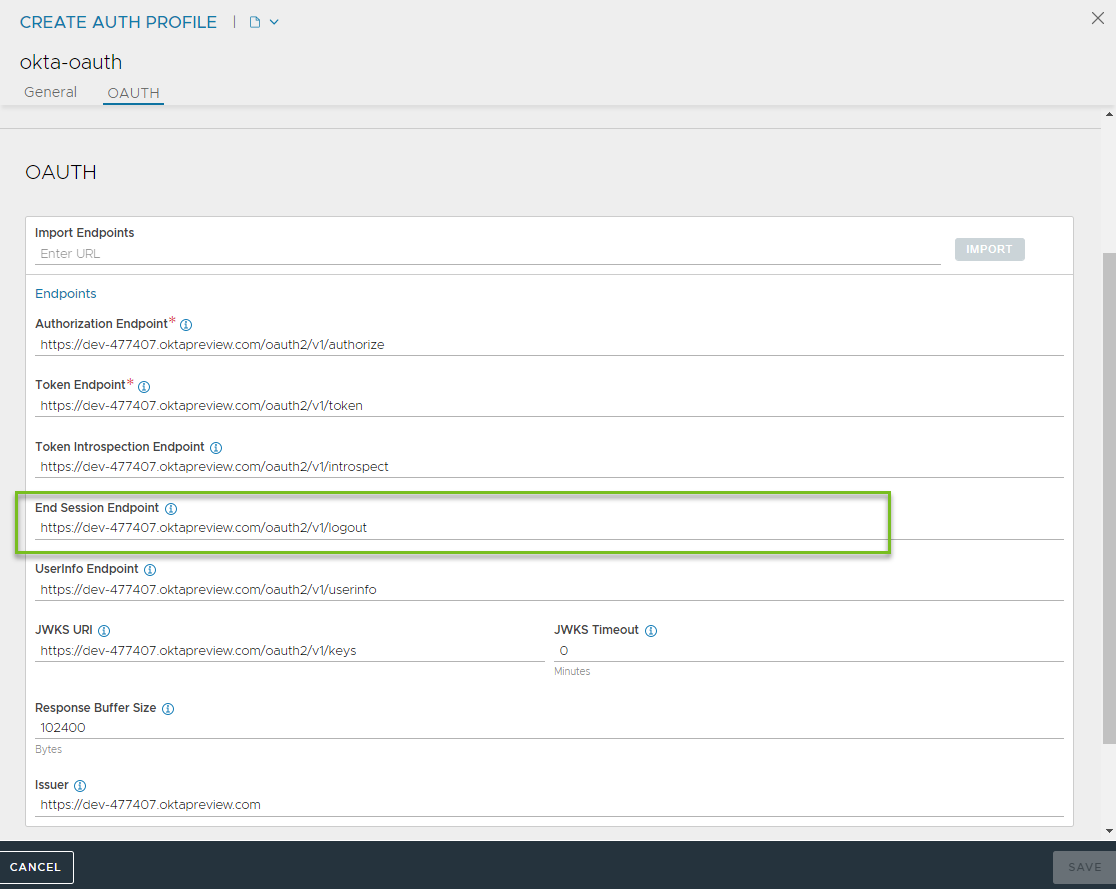
- Create or edit an Auth Profile by configuring End Session Endpoint. For complete configuration steps, see Configuring Authentication Profile.
- Under Access Policy, enter the details in the fields. For complete configuration steps, see Configuring OAuth settings on the Virtual Service.
- Enter Logout URI and Post Logout Redirect URI as shown below:

- Click Save.
Using the CLI
The prerequisite configuration steps for OIDC are explained here.
- Configure
OAuth oauth_profileof authprofile withend_session_endpointor logout URI of IDP (e.g., okta).[admin: controller]: > configure authprofile okta-oauth [admin: controller]:authprofile > oauth_profile [admin: controller]:authprofile:oauth_profile> end_session_endpoint https://dev-477407.oktapreview.com/oauth2/v1/logout [admin: controller]:authprofile:oauth_profile>save [admin: controller]:authprofile>save [admin: controller]:> - Configure OAuth enabled virtual service with
oidc_enableset to true usingconfigure virtualservice <VS_NAME>command.[admin: controller] configure virtualservice okta-test - Configure
logout_uri&post_logout_redirect_uriunder theoauth_vs_configsubmodule of virtual service.[admin: controller]:virtualservice> oauth_vs_config [admin: controller]:virtualservice:oauth_vs_config> logout_uri https://okta-test.auth.com/oauth/logout [admin: controller]:virtualservice:oauth_vs_config> post_logout_redirect_uri https://okta-test.auth.com/ [admin: controller]:virtualservice:oauth_vs_config> save [admin: controller]:virtualservice> save [admin: controller]:>
Output:
[admin:controller]: virtualservice> oauth_vs_config
[admin:controller]: virtualservice:oauth_vs_config> where
Tenant: admin
Cloud: Default-Cloud
+--------------------------+-------------------------------------------------+
| Field | Value |
+--------------------------+-------------------------------------------------+
| redirect_uri | https://okta-test.auth.com/oauth/callback |
| cookie_name | OAUTH_IUPKWGLH |
| cookie_timeout | 1 min |
| oauth_settings[1] | |
| auth_profile_ref | okta-oauth |
| app_settings | |
| oidc_config | |
| oidc_enable | True |
| profile | True |
| userinfo | True |
| client_id | 0oaubdgcuk6wLEfKq0h7 |
| client_secret | <sensitive> |
| resource_server | |
| access_type | ACCESS_TOKEN_TYPE_OPAQUE |
| opaque_token_params | |
| server_id | 0oaubdgcuk6wLEfKq0h7 |
| server_secret | <sensitive> |
| key[1] | |
| name | dc7dde0a-8a64-45b4-8ded-f65adb03c2a4 |
| aes_key | b'sdZFYlVECVu9aW7XK4IhVaC8TfakvNSvp6m861tyVNc=' |
| logout_uri | https://okta-test.auth.com/oauth/logout |
| post_logout_redirect_uri | https://okta-test.auth.com/ |
The end_session_endpoint is configured under authprofile as shown below:
[admin:controller]: > show authprofile okta-oauth
+--------------------------+---------------------------------------------------------+
| Field | Value |
+--------------------------+---------------------------------------------------------+
| uuid | authprofile-998740b9-5123-4d4d-8fb9-f9f9a3886248 |
| name | okta-oauth |
| type | AUTH_PROFILE_OAUTH |
| oauth_profile | |
| authorization_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/authorize |
| token_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/token |
| introspection_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/introspect |
| jwks_uri | https://dev-477407.oktapreview.com/oauth2/v1/keys |
| jwks_timeout | 0 min |
| issuer | https://dev-477407.oktapreview.com |
| pool_ref | pool-okta |
| oauth_resp_buffer_sz | 1000000 |
| userinfo_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/userinfo |
| end_session_endpoint | https://dev-477407.oktapreview.com/oauth2/v1/logout |
| tenant_ref | admin |
+--------------------------+---------------------------------------------------------+
Notes:
-
Logout URI is only applicable if OIDC is enabled.
-
End Session Endpoint must be configured to configure Logout URI.
-
End Session Endpoint cannot be removed if Logout URI is configured. To remove the End Session Endpoint, no value must be configured for the Logout URI.