Single VIP with two Virtual Services (Using 307 Redirect)
Overview
Avi Vantage can be deployed in front of Unified Access Gateways (UAG) , connection servers, app volume managers etc as required.
This article shows the recommended way to configure Avi Vantage for load balancing traffic to UAG servers in VMware Horizon deployments.
The document also covers steps to load balance connection servers and app Volume managers.
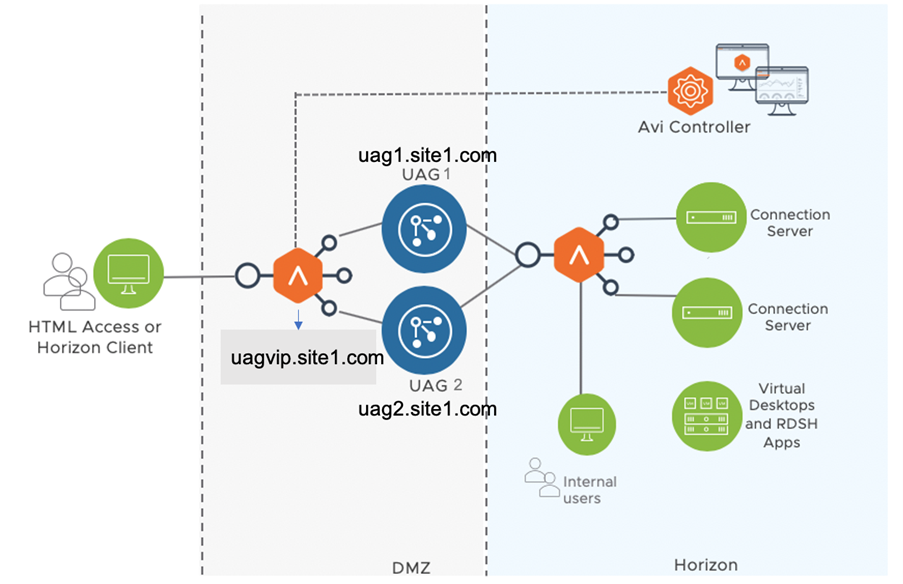
Sample Topology
Consider the request flow with the sample topology:
Note: The sample topology illustrates UAG deployment in a DMZ network. However, Avi Vantage supports deployment in both DMZ and non-DMZ networks.
| FQDN | Entity Description | IP Address used for DNS Entries | Real IP |
|---|---|---|---|
| uagvip.site1.com | FQDN of Avi LB VIP | VIP 1 | 10.10.5.200 |
| uag1.site1.com | FQDN of UAG server 1 on site 1 | VIP 1 | 10.58.17.163 |
| uag2.site1.com | FQDN of uag server 2 on site 1 | VIP 1 | 10.58.17.164 |
Note: The IP and FQDN used in the example are for illustration purposes only. Replace this with your real environment details.
Request Flow
The request flow for this deployment is as shown below:
-
User sends a request to access uagvip.site1.com over the internet.
-
The request comes to the Avi load balancer.
-
The Avi load balancer does the load balancing and sends the request to one of the backend UAG servers. In this case, let’s assume that Avi sent the request to UAG server 1 i.e. uag1.site1.com
-
UAG sends 307 redirect to client with uag1.site1.com FQDN. UAG servers should be configured with the 307 feature as explained in Unified Access Gateway Support for HTTP Host Redirect. A sample UAG configuration is shown here.
-
Client looks for location header and queries the host in the location header (uag1.site1.com ).
-
Using the DNS entries that were created (shown in the table above), the FQDN (uag1.site1.com) will be resolved to Avi VIP IP.
-
From the 307 redirect, all further flows will have the host header set.
-
Client starts authentication with new UAG FQDN (uag1.site1.com).
-
When the request comes to the Avi LB, the Avi virtual service parses the host header and forwards to UAG based on the host header (uag1.site1.com ) using the HTTP policies.
-
UAG1.site1.com performs authentication, verifies entitlements and returns the secondary protocol information which includes the external URL’s for the protocols, along with their configured custom ports.
-
When the client launches the application, the L4 virtual service uses a DataScript to send the request to correct UAG server based on the incoming destination port i.e. custom ports.
Configurations for Load Balancing
The steps to configure the load balance UAG are as below:
-
Creating an L4 Virtual Service using the L7 virtual service as shared VIP and specify all the ports required for secondary protocols
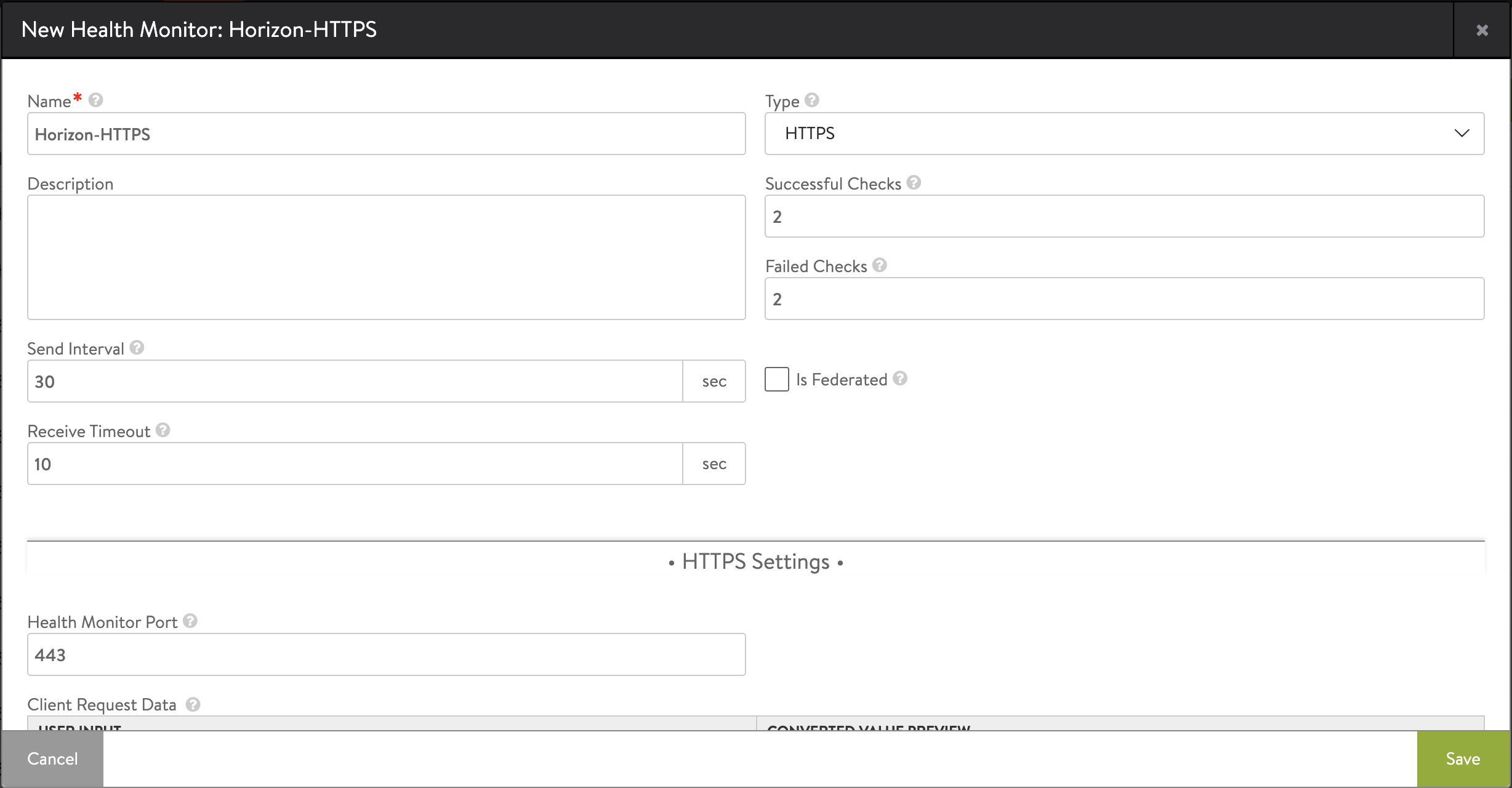
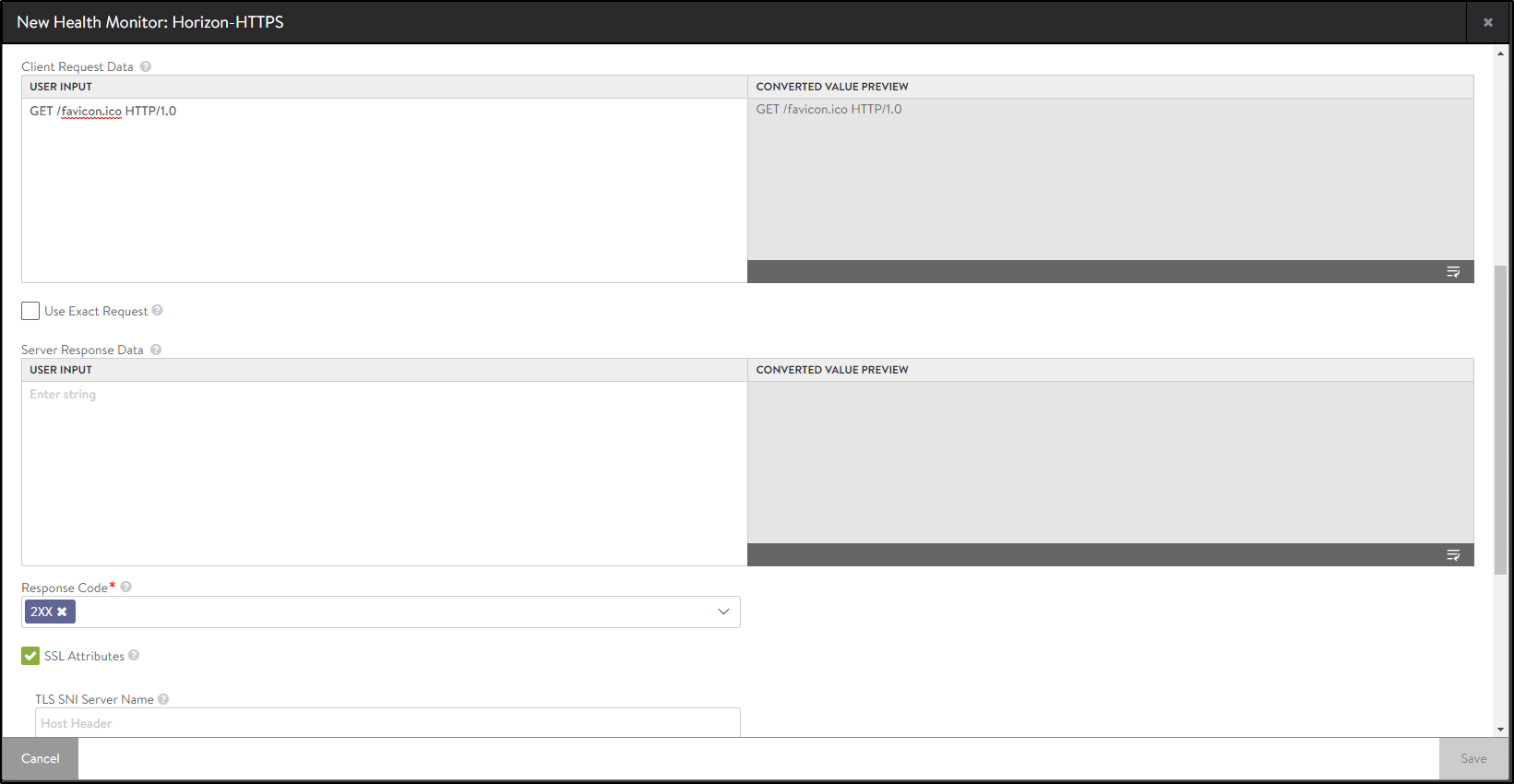
Creating Custom Health Monitor for UAG
To create a custom health monitor,
-
From the Avi UI, navigate to Templates > Profiles > Health Monitors.
-
Click on Create.
-
Select the VMware cloud that was created for Horizon.
-
Enter the following details in the New Health Monitor screen.
Field Value Send Interval 30 Receive Timeout 10 Client Requested Data GET /favicon.ico HTTP/1.0 Response Code 2xx -
Click on Save.
Creating Pools
Create an SSL Profile to be used in the UAG Pool
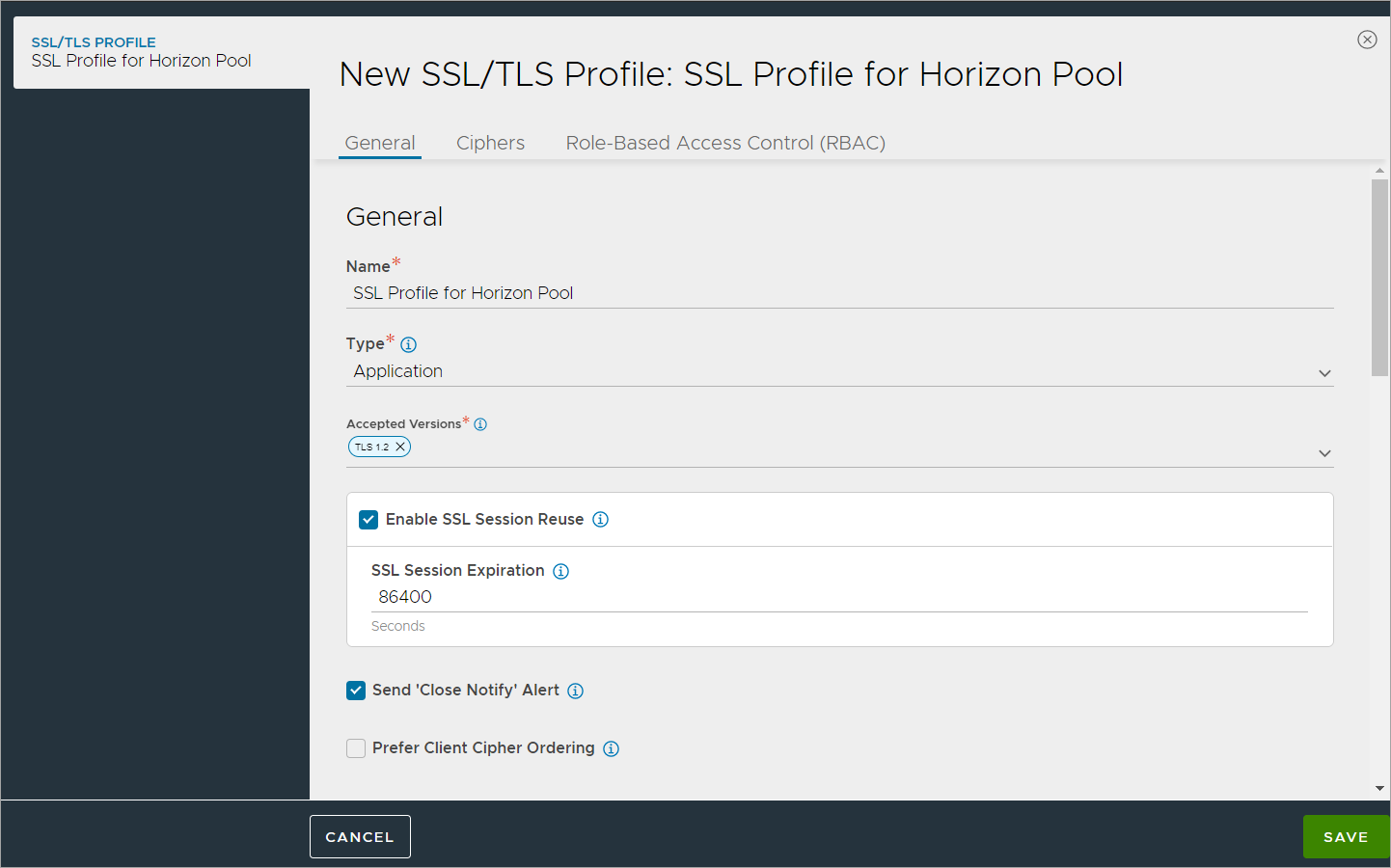
Creating SSL Profile for Pool
Create an SSL Profile for the UAG pool with the configuration given below:
- Accepted Versions: 1.2
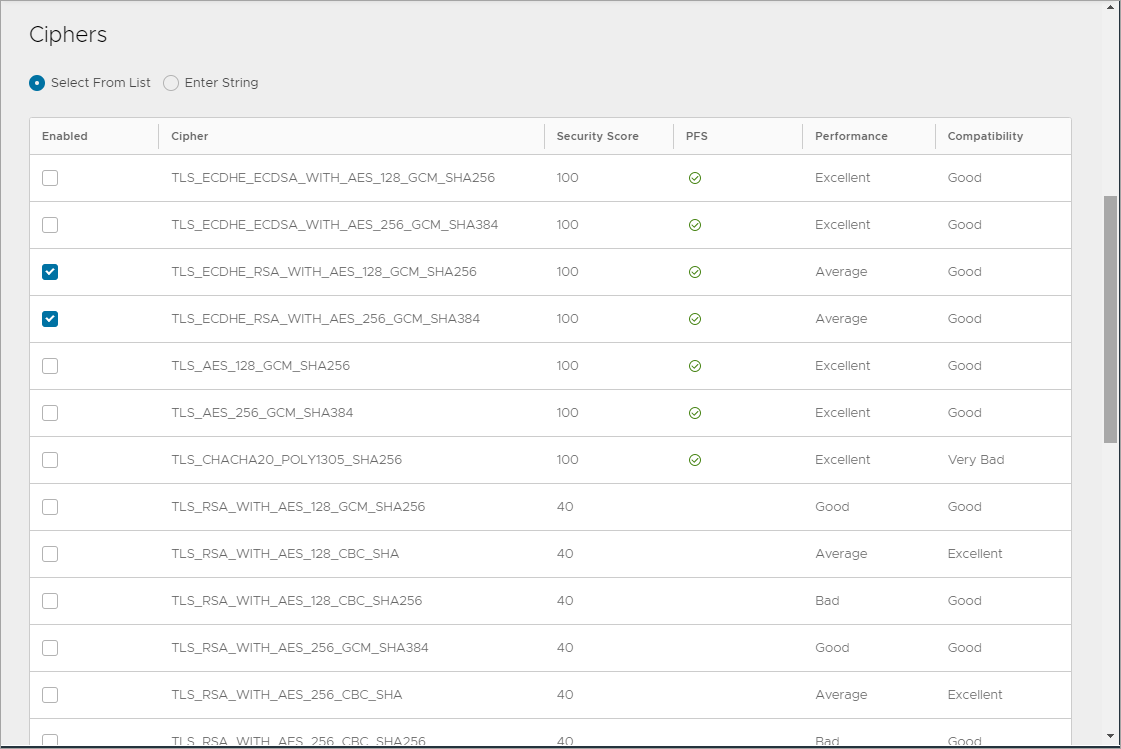
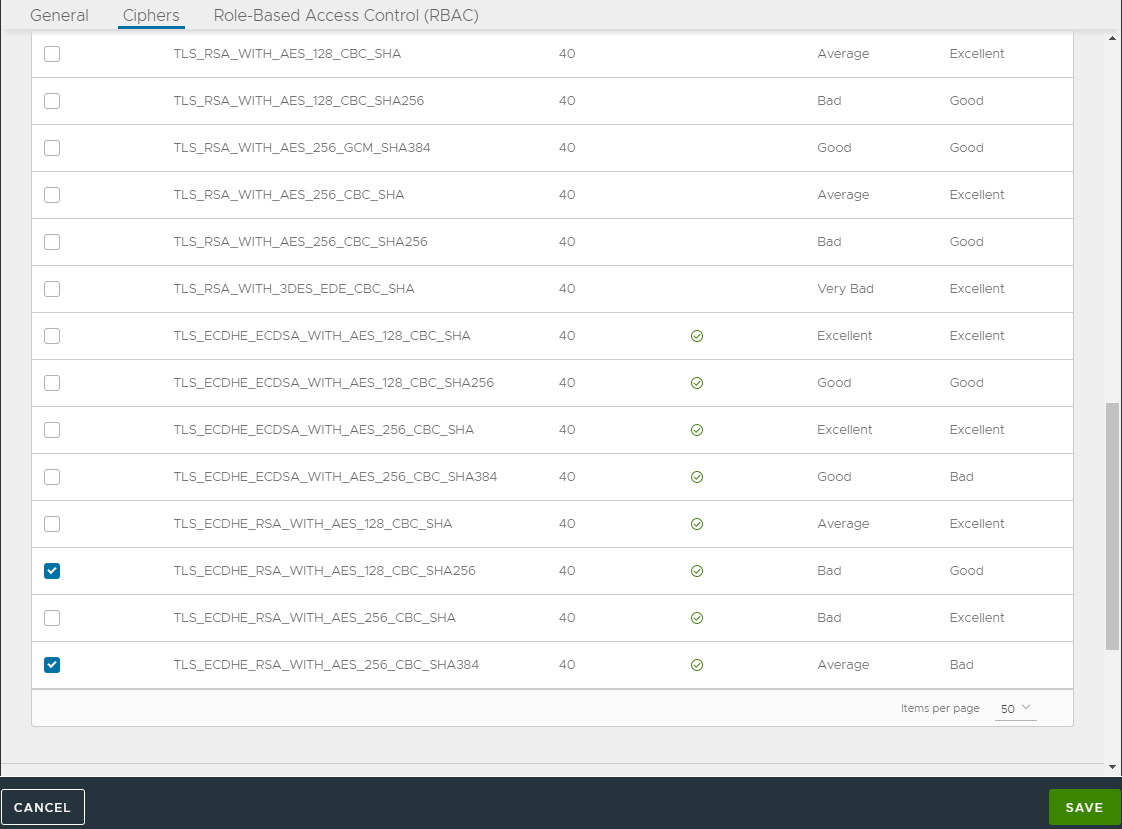
- Cipher List:
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- Navigate to Templates > SSL/TLS Profile > Create
- Select Application Profile.
- Enter the details as shown below:
- Click on Save.
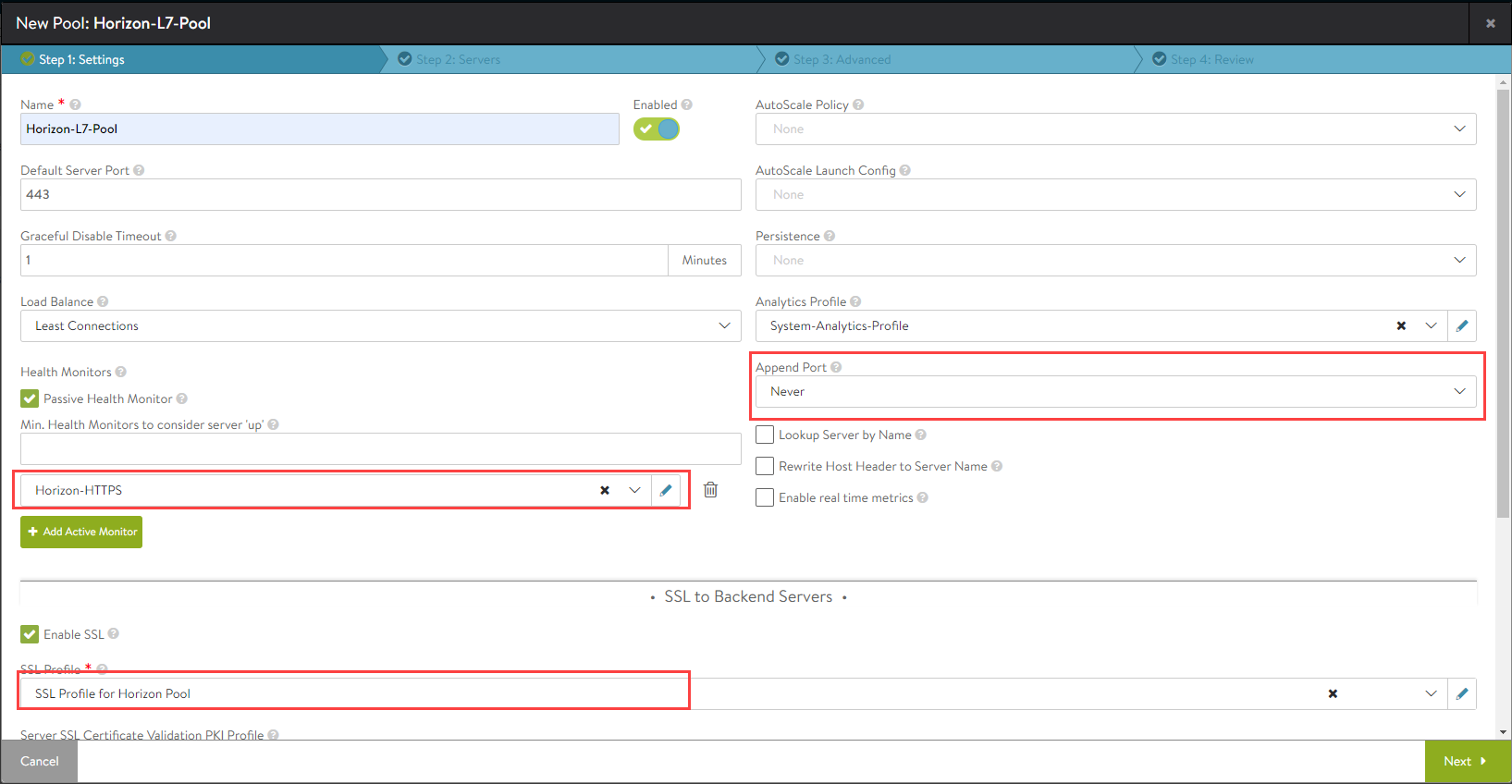
Creating the UAG L7 Pool
To create the pool,
-
In Avi Vantage, navigate to Applications > Pools.
-
Select the vCenter cloud from the Select Cloud sub-screen.
-
Click on Next.
-
Click on Create Pool.
-
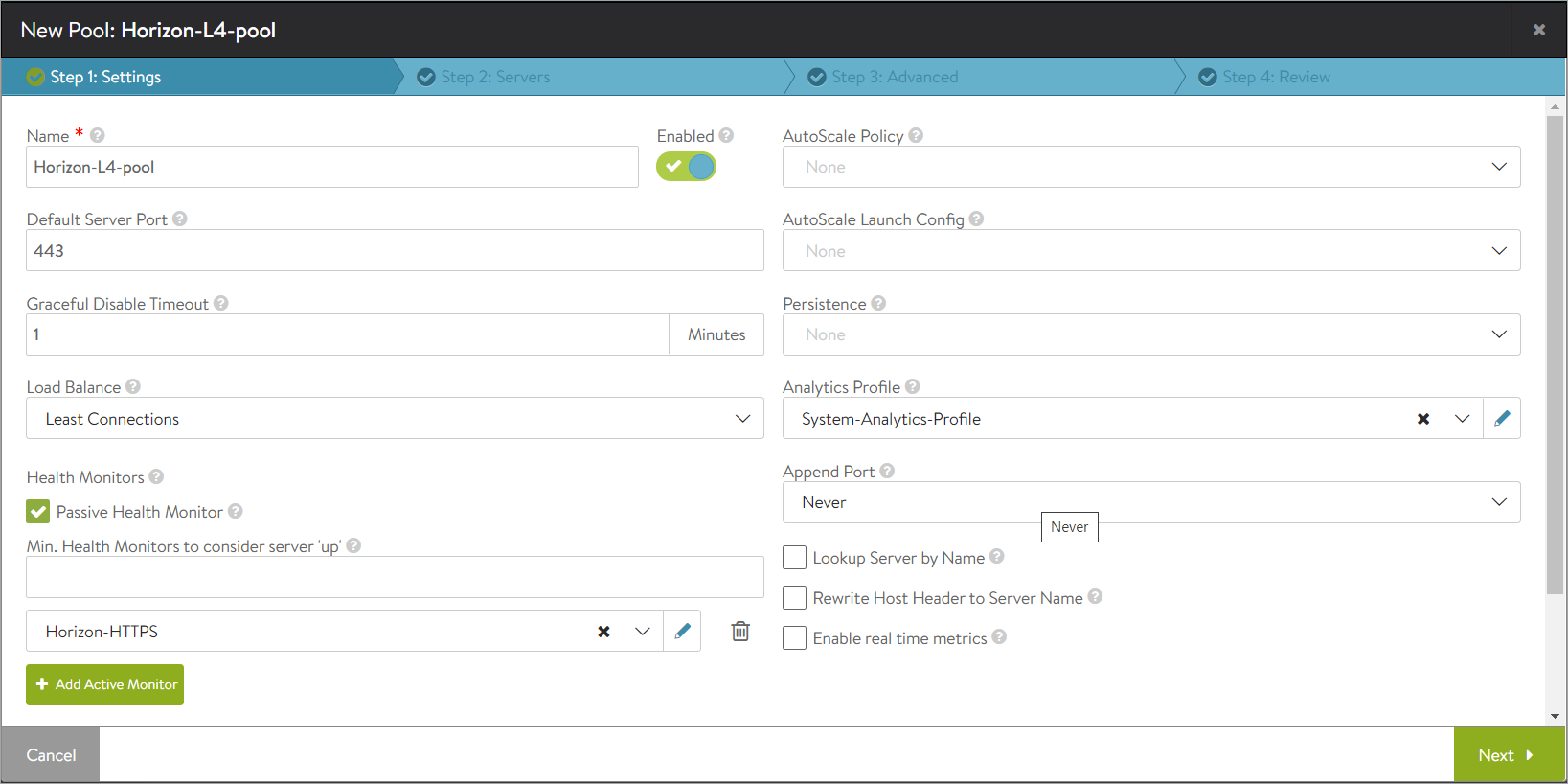
In the New Pool: screen, update the details as shown below:
-
Click on Next.
-
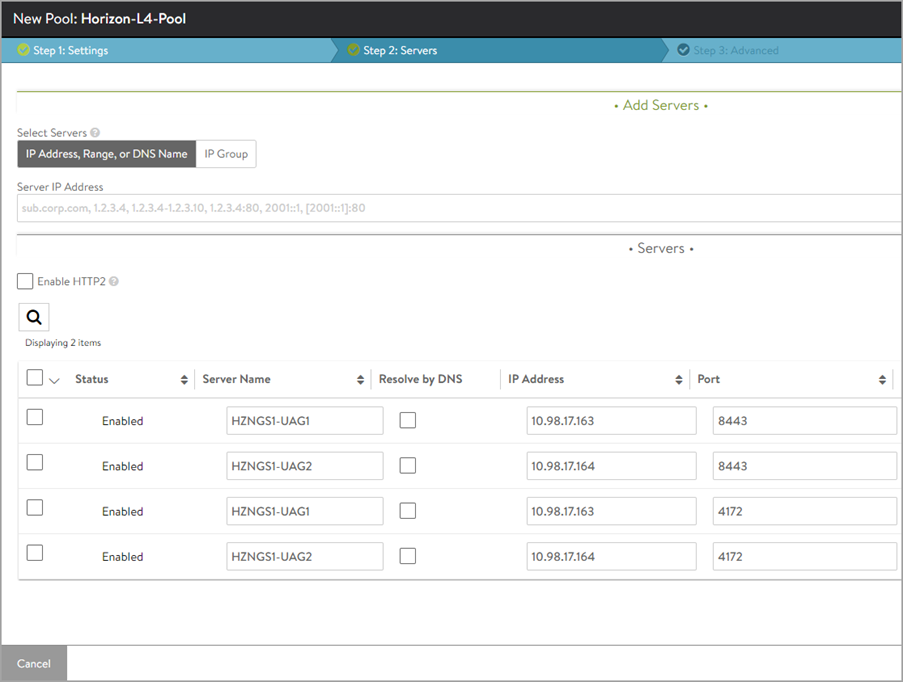
In the Step 2: Servers tab, add the Server IP Address of the UAG servers created earlier and click on Add Server. The ports need to be configured for Secondary Protocol like 8443 for Blast, 4172 for PCoIP.
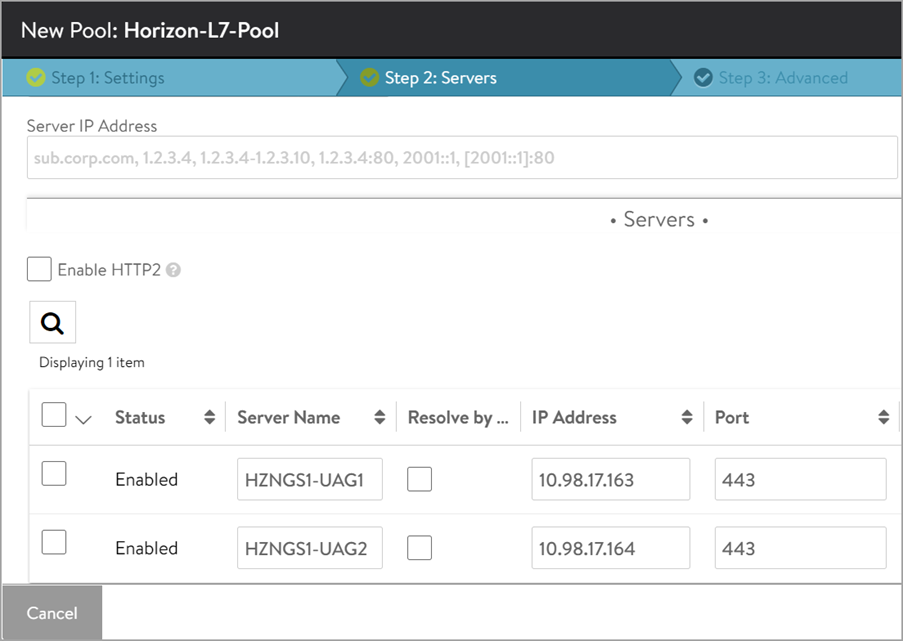
-
Click on Next.
-
Navigate to Step 3: Advanced tab > Step 4: Review.
- Click on Next and then click on Save.
Creating the UAG L4 Pool
-
Create a pool with the name Horizon-l4-pool. Ensure that the pool configuration (port , UAG server IP , load balancing algorithm , health monitor etc.) is the same as the Horizon L7 Pool.
-
Under the Step 2: Servers tab, add the Server IP Address of the UAG servers created earlier and click on Add Server.
The ports need to be configured for Secondary Protocol like 8443 for Blast, 4172 for PCoIP.
-
Click Next.
-
Click Next and click Save.
Installing the SSL certificate Required for L7 VIP
The SSL connection is being terminated at the Avi virtual service. Therefore, the SSL certificate must be assigned to the virtual service . It is recommended to install a certificate which is signed by a valid certificate authority instead of using self-signed certificates. Install the certificate in Avi Vantage, and ensure the CA certificate is imported and linked. For information, refer to Import Certificates.
Note: For this set up, a certificate named Horizon_Certificate has been installed.
Add the SAN certificate to UAG as explained in the Configuring TLS/SSL Certificates for Unified Access Gateway Appliances.
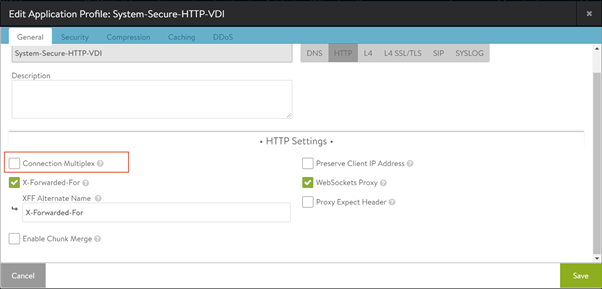
Disabling Connection Multiplexing
In case of UAG load balancing, disable connection multiplexing for the System-Secure-HTTP-VDI profile.
To disable connection multiplexing,
-
Navigate to Templates > Profiles> Application > System-Secure-HTTP-VDI.
-
Click on the edit icon.
-
Click on Save.
Creating L7 Virtual Service and HTTP Request Policies
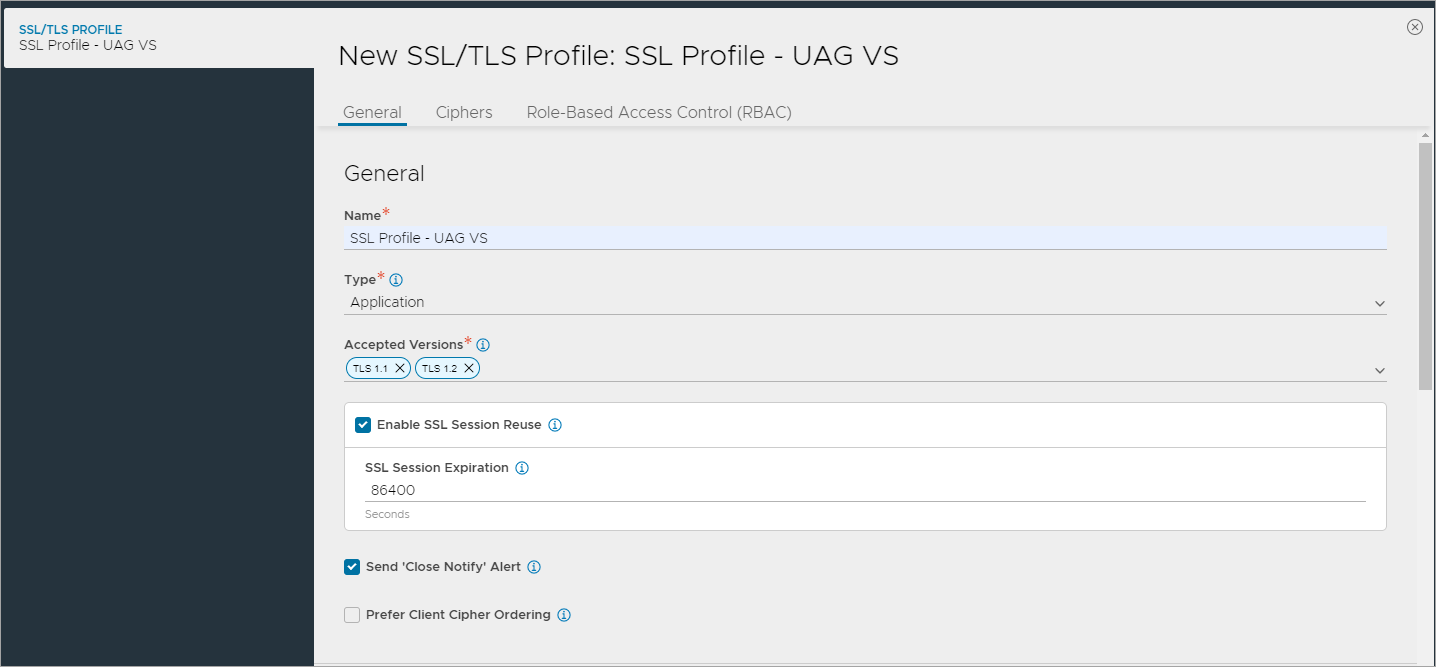
Create an SSL Profile for the virtual service with the configuration given below:
- Accepted Versions: TLS 1.1, 1.2
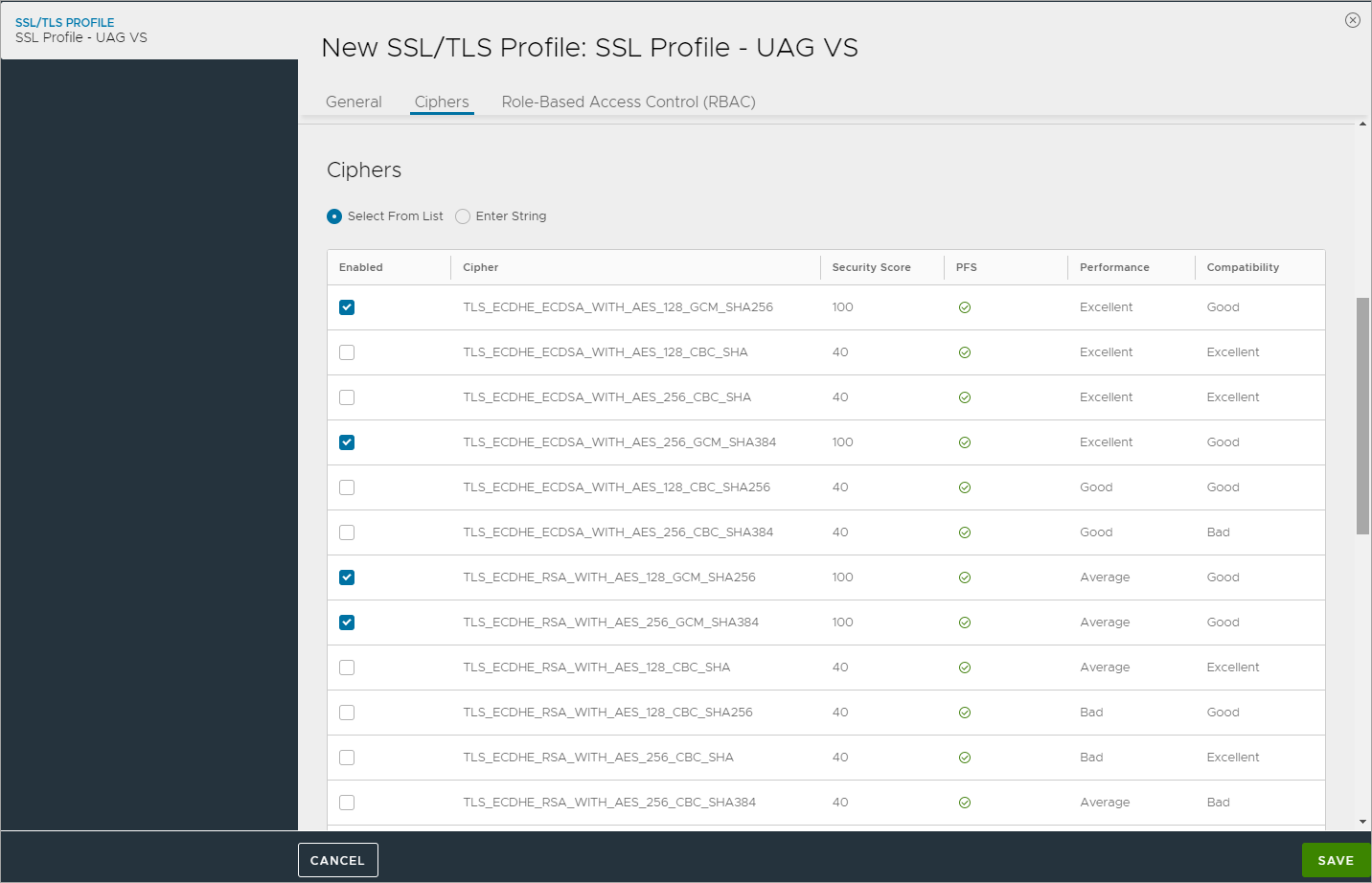
- Cipher List:
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- Navigate to Templates > SSL/TLS Profile > Create
- Select Application Profile.
- Enter the details as shown below:
- Click on Save.
To create the new L7 virtual service,
-
From the Avi UI, navigate to Applications > Virtual Services.
-
Click on Create Virtual Service > Advanced Setup.
-
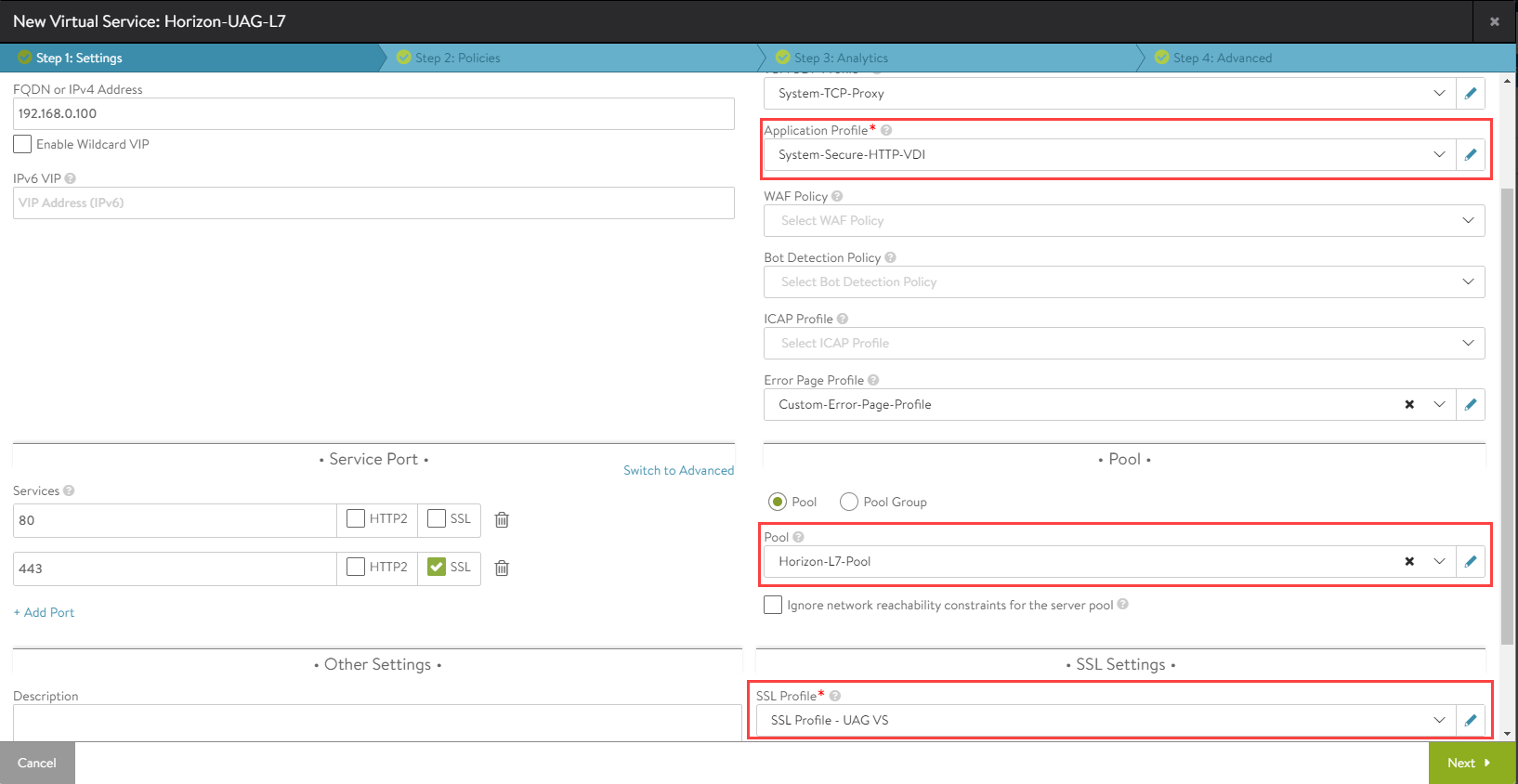
Use the System-Secure-HTTP-VDI as the Application Profile.
-
Configure the virtual service as shown below:
-
Click on Next.
-
Go to Policies > HTTP Request Policies and add policies as shown below:
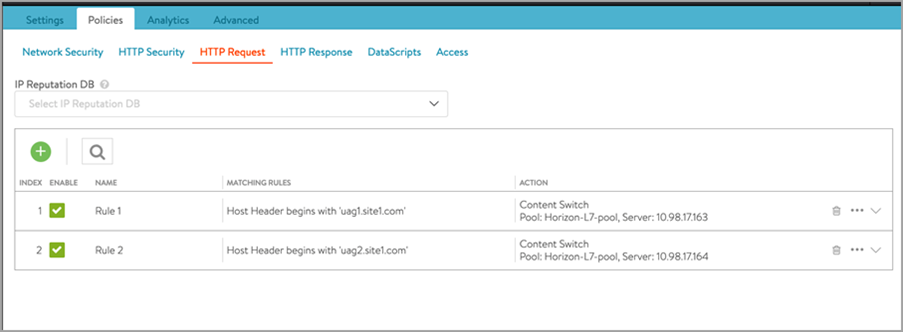
As mentioned in the request flow, the Avi L7 virtual service looks for host header in the incoming requests from client. Based on the host header, request is sent to one of the UAG servers.
In the http policies shown above, the rules are created to look for the Host header and then route the request to one of the backend UAG servers based on the Host header.
For example, if the host header is uag1.site1.com, send the request to UAG1 server. If host header is uag2.site1.com, send the request to UAG2 server -
Click Save.
-
Click on Next > Next.
-
Click Save.
Creating L4 Virtual Service
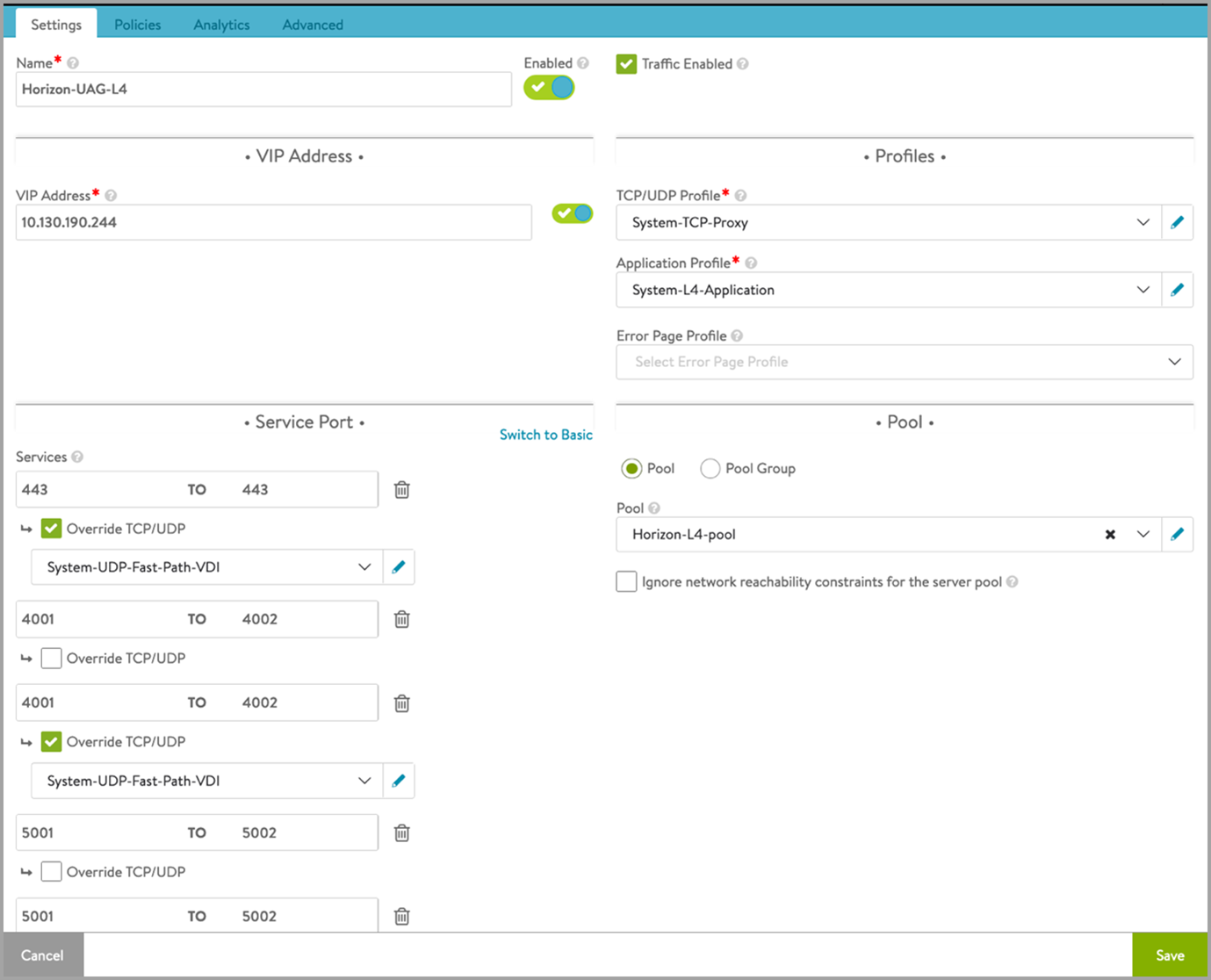
Create another virtual service which will share the same IP address as that of the L7 VIP. This will make sure that we need only one virtual IP address for both the primary and secondary protocols. L7 virtual service will loadbalance the primary protocol whereas L4 virtual service will load balance the secondary protocols. To create an L4 virtual service,
-
Click on Create Virtual Service > Advanced Setup.
-
In the New Virtual Service screen, click on Switch to Advanced under VIP Address as shown below:
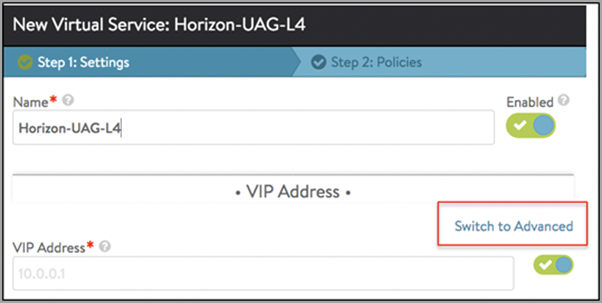
-
Select the L7 virtual service that was created as the Virtual Service for VIP Sharing as shown below:
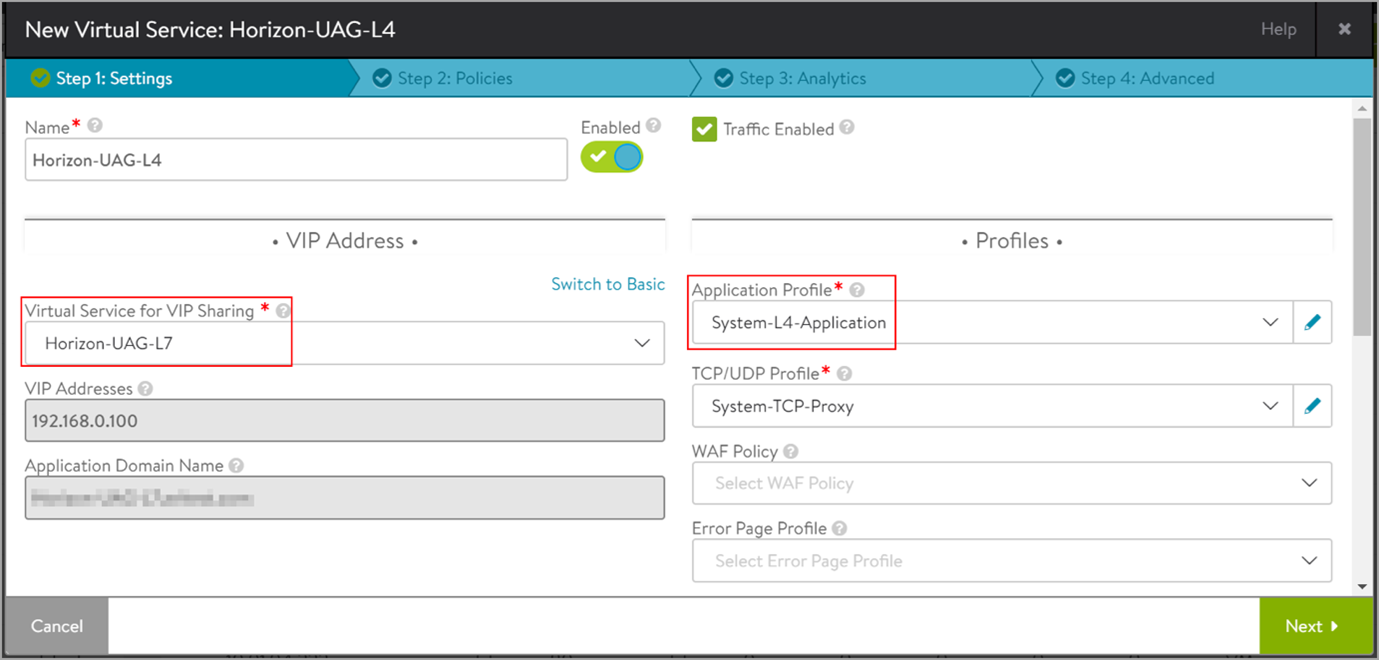
-
Under Service Port > Services, click on Switch to Advanced.
-
Add the port numbers for the secondary protocols as shown below:
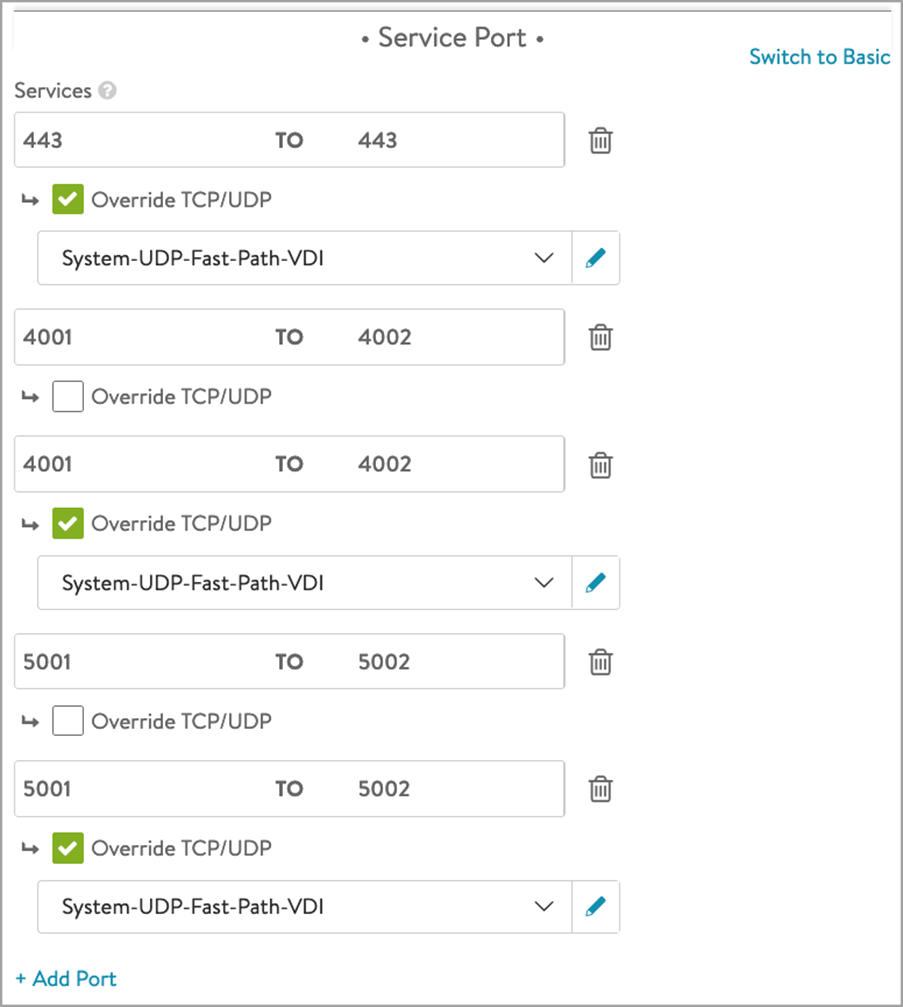
The custom ports here, that is, 4001 and 4002 are used for Blast and 5001 and 5002 are used for PCoIP. These are configured on UAG. Note that there is no restriction to use only these port numbers. You can use any non standard port numbers here but you need to make sure that configuration of these port numbers are same on UAG and on Avi (as shown above).
A sample configuration is shown here -
Click on Save.
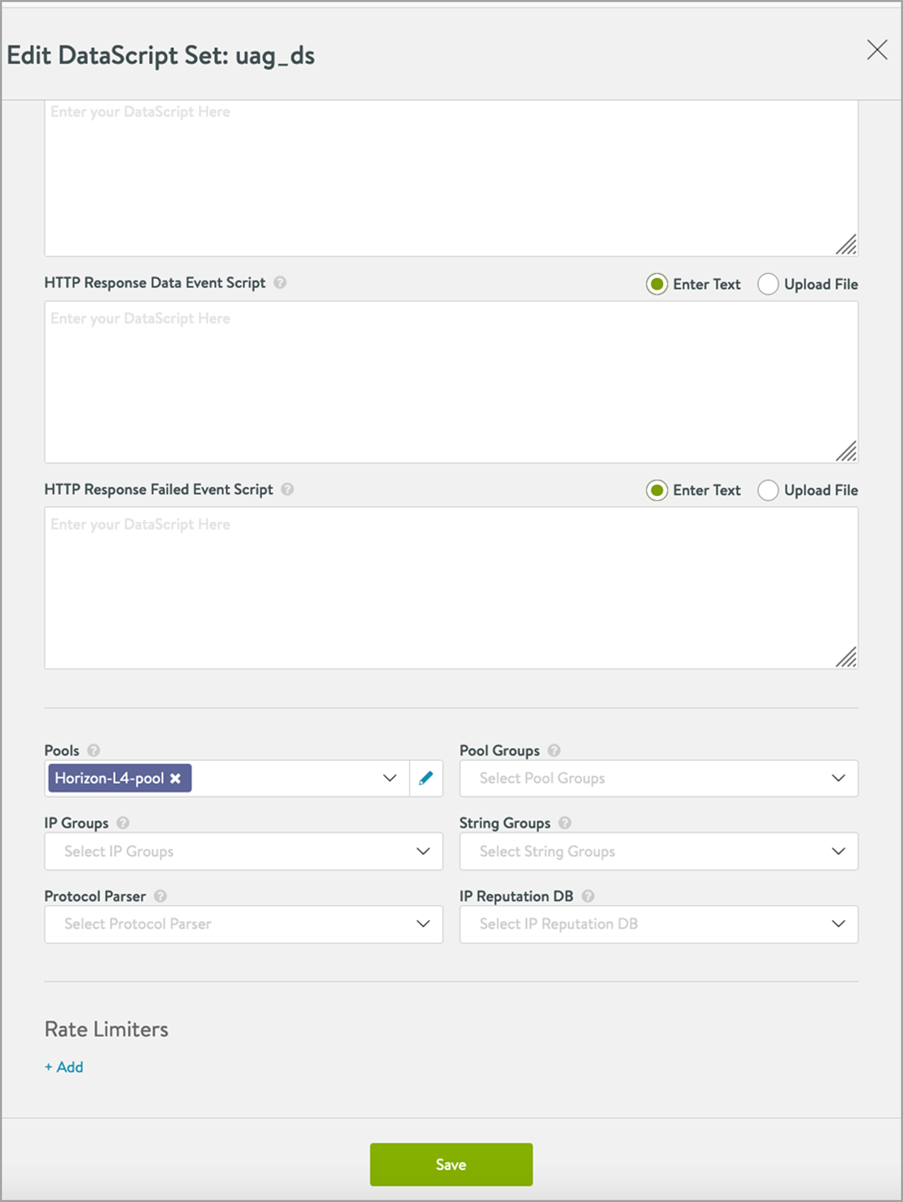
Creating the L4 DataScript
To create the L4 DataScript,
-
Edit the L4 virtual service which was just created.
-
Click on Next.
-
Click on DataScript.
-
Add the following DataScript for L4 Request Event:
avi_port = avi.vs.port()
if avi_port == "4001" then
avi.pool.select("L4-pool", "UAG_server1_IP_site1", 8443)
elseif avi_port == "4002" then
avi.pool.select("L4-pool", "UAG_server2_IP_site1", 8443)
elseif avi_port == "5001" then
avi.pool.select("L4-pool", "UAG_server1_IP_site1", 4172)
elseif avi_port == "5002" then
avi.pool.select("L4-pool", "UAG_server2_IP_site1", 4172)
end
Notes:
1. This DataScript is to ensure that requests coming on specific ports are routed to the appropriate UAG server. The ports (4001/4002/5001/5002) are used to establish persistence logic using this DataScript. It is ensured that Avi translate the port to the standard blast/PCoIP ports i.e. 8443/4172 while sending the requests to one of the UAG servers. This is important because UAG servers listen on ports 8443 and 4172 for Blast and PCoIP respectively. UAG servers do not understand the custom ports -4001/4002/5001/5002.
2. If there more UAG servers, ensure all the server IP:port pairs are added to the L4 pool before creating the DataScript.
- In the DataScript pane, bind the L4 pool:
- Click on Save.
Important Configurations to Check on UAG for This Solution
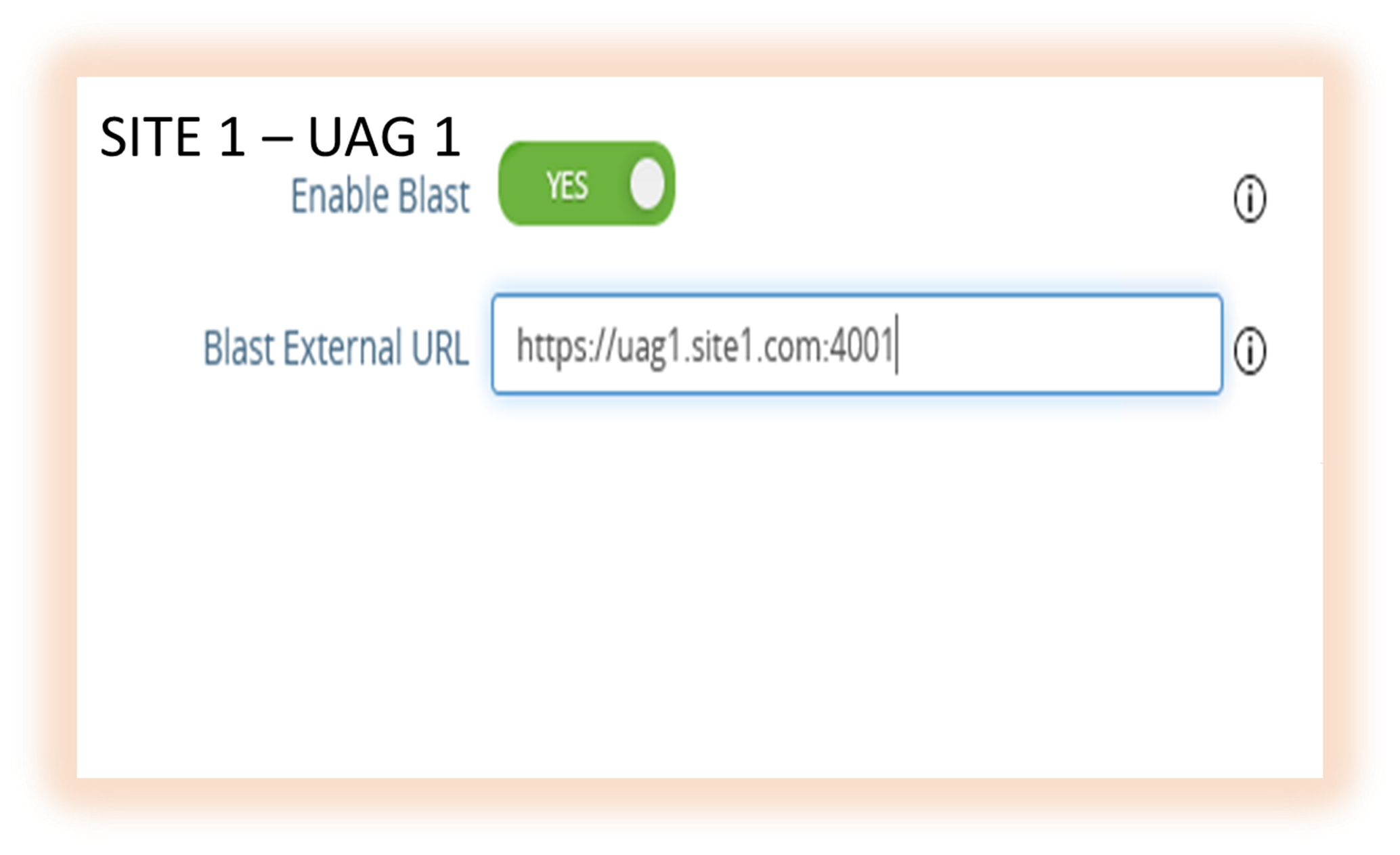
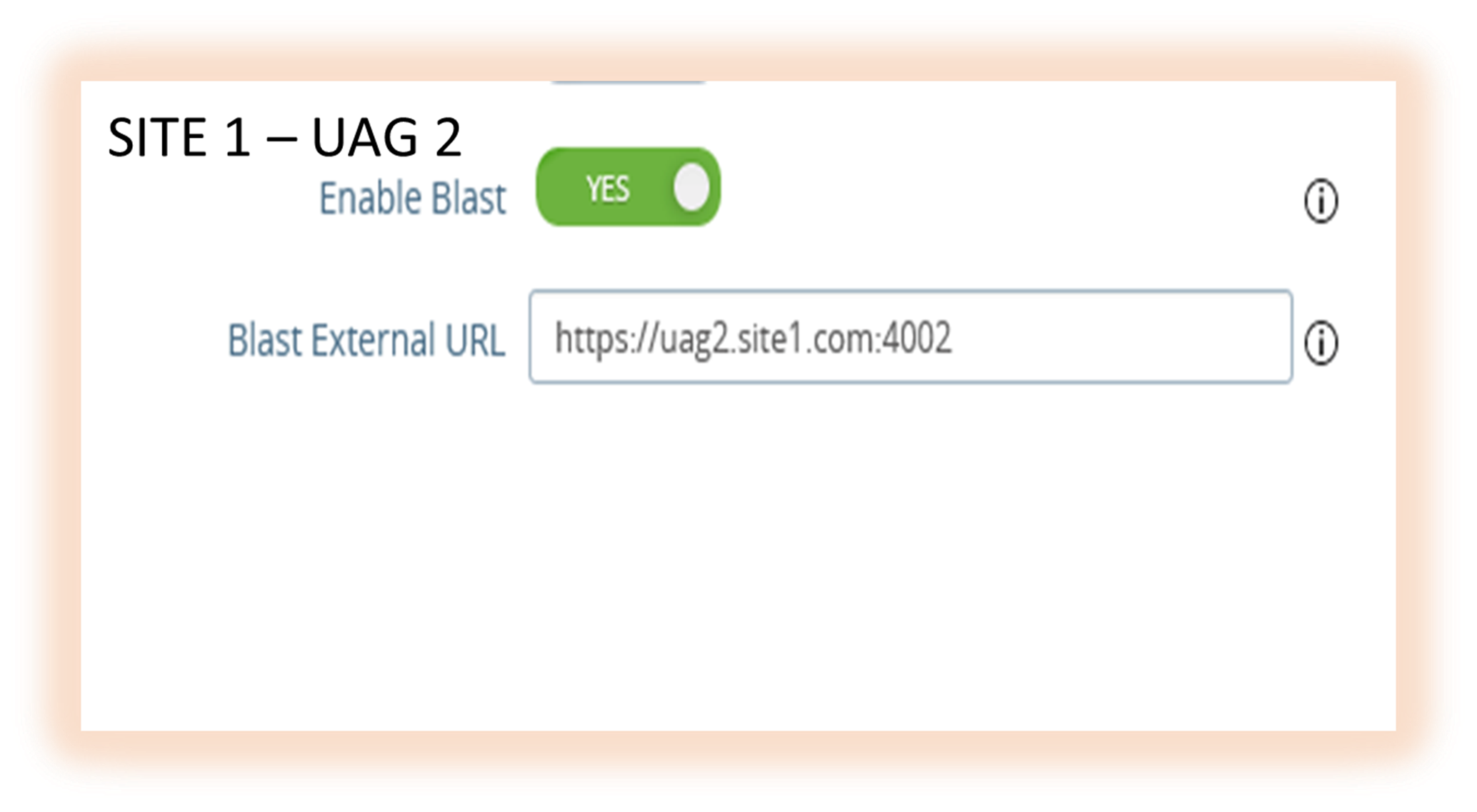
- Blast URL should point to the UAG hostname/FQDN with the correct port numbers as shown below, for example:
- Site 1 – UAG1 - https://<UAG1 FQDN>:4001/
- Site 1 – UAG2 - https://<UAG2 FQDN>:4002/
- Similarly, PCoIP should point to Avi VIP with correct port numbers.
- Site 1 – UAG1 - https://<Avi VIP IP on site 1>:5001/
- Site 1 – UAG2 - https://<Avi VIP IP on site 1>:5002/
- Host Redirect mapping should be configured on all UAGs.
Notes: Ensure the following:
- The source host is the LB FQDN. For example, uagvip.site1.com
- The redirect host is the UAG’s FQDN. For example, uag1.site1.com
- Upload the Avi VS certificate on all the UAG servers
Other Considerations
- All the host names/FQDNs have to be added in SAML IDP.
- Install the same certificate and key pair on Avi and bind it to the UAG L7 VS.
-
In some cases, when accessing the VMware Horizon Client, multiple icons for the same site can be displayed as shown below:
This issue will be resolved in the upcoming releases for Horizon Client.
Enabling WAF For UAG Traffic
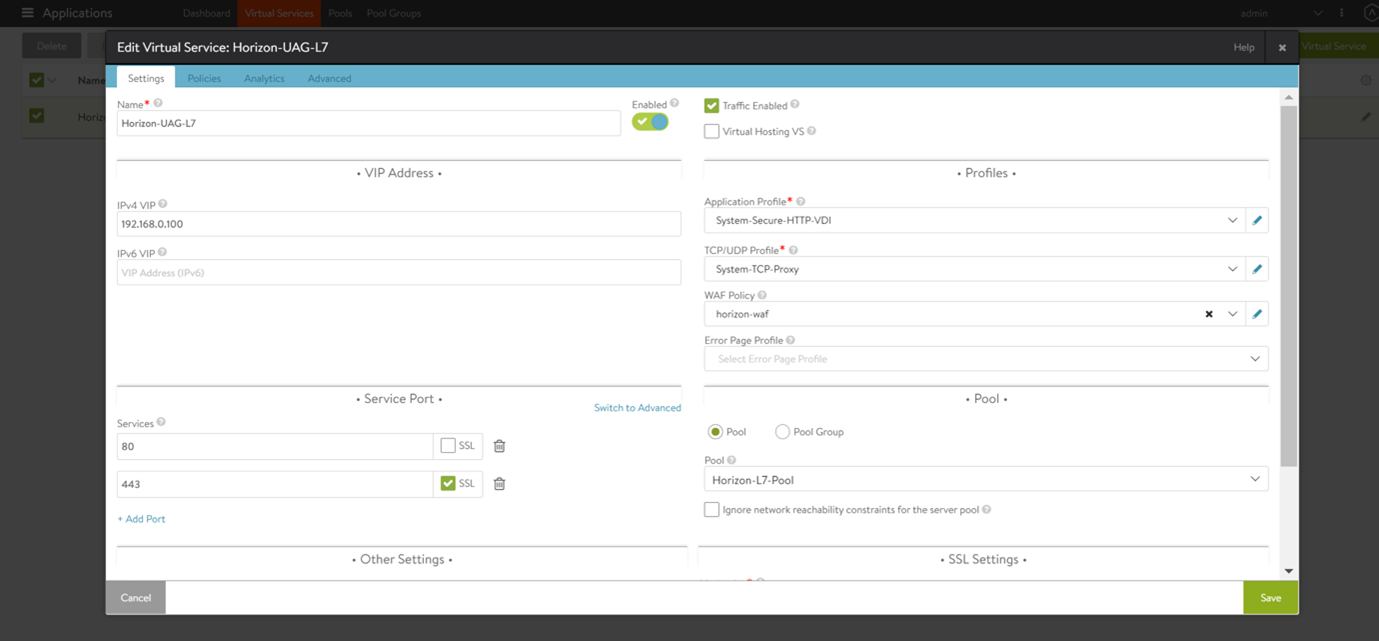
Avi Vantage supports WAF for HTTP/HTTPS traffic for Horizon deployments. WAF rules are supported for L7 virtual service for primary protocol (XML/API) traffic.
Notes:
- It is recommended to use the default CRS rules. The other rules for response inspection are not required and these signatures or rules should not be enabled in CRS rules.
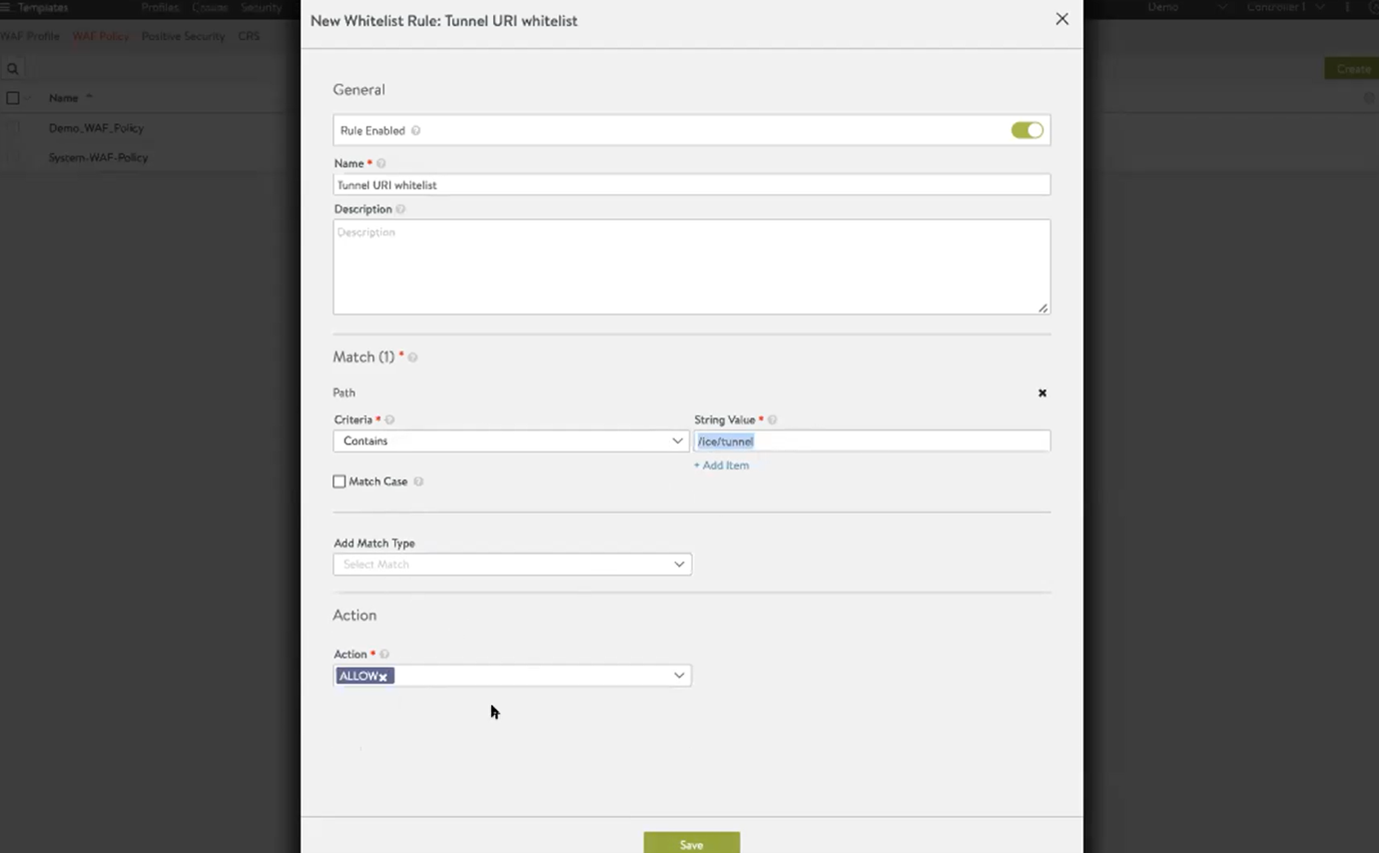
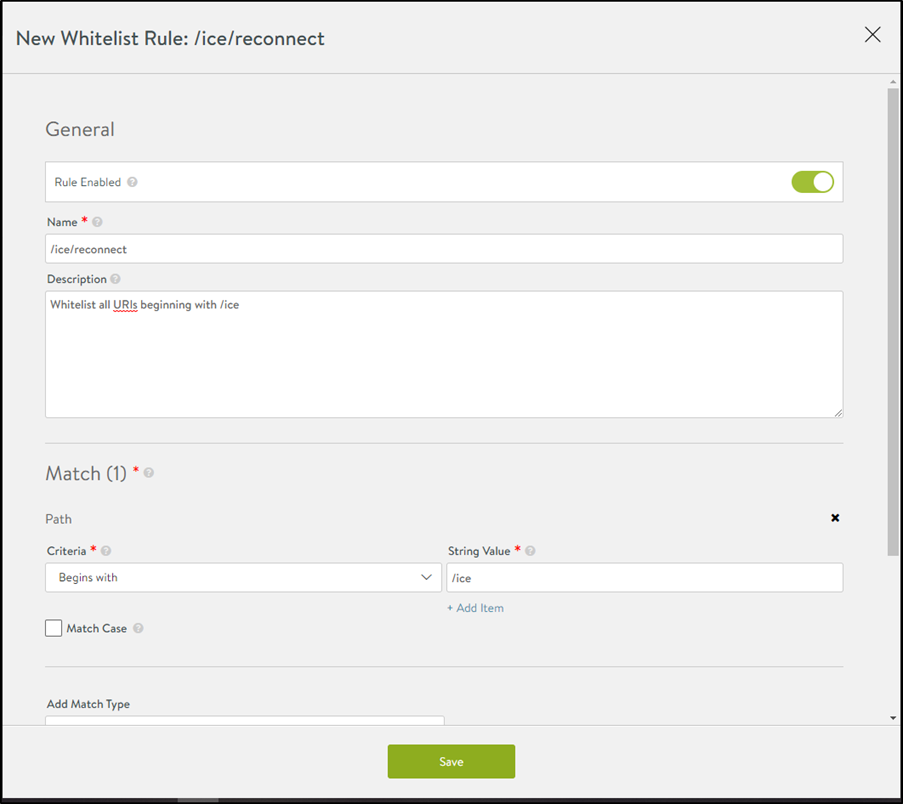
- It is mandatory to add the WAF policy and allowed URI containing /ice/tunnel/ and /ice/reconnect to make sure the WAF feature works seamlessly with the horizon application. Similarly, allow other /ice/ related URIs, if any. Allowing all URIs beginning with /ice is a best practice.
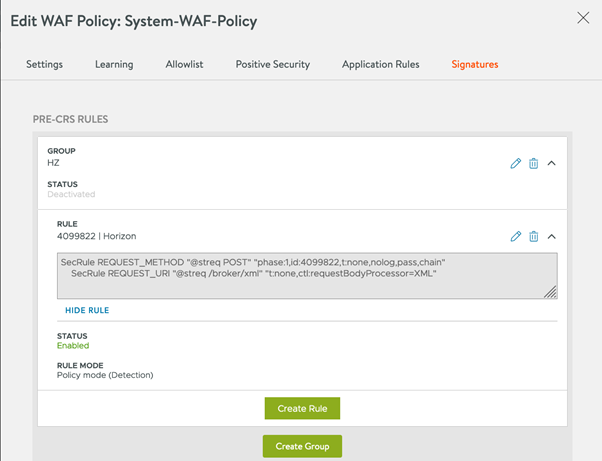
- Use the following to add a pre-CRS rule as shown below: This rule is required to make sure that Avi parses the incoming payload as XML payload only.
SecRule REQUEST_METHOD "@streq POST" "phase:1,id:4099822,t:none,nolog,pass,chain"
SecRule REQUEST_URI "@streq /broker/xml" "t:none,ctl:requestBodyProcessor=XML"
- It is recommended to disable command injection rule(932105). This rule is not required for Horizon deployments.
Create an L7 virtual service (or use the existing virtual service) and follow the steps mentioned below:
-
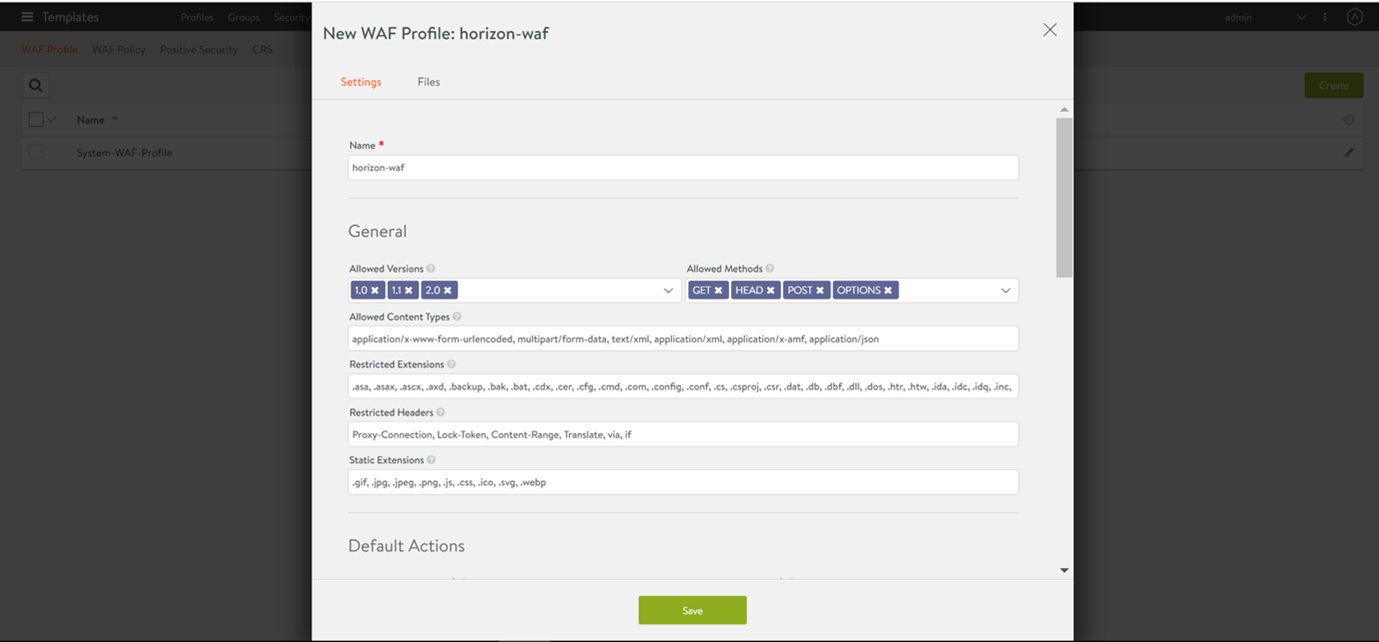
Create a WAF profile.
-
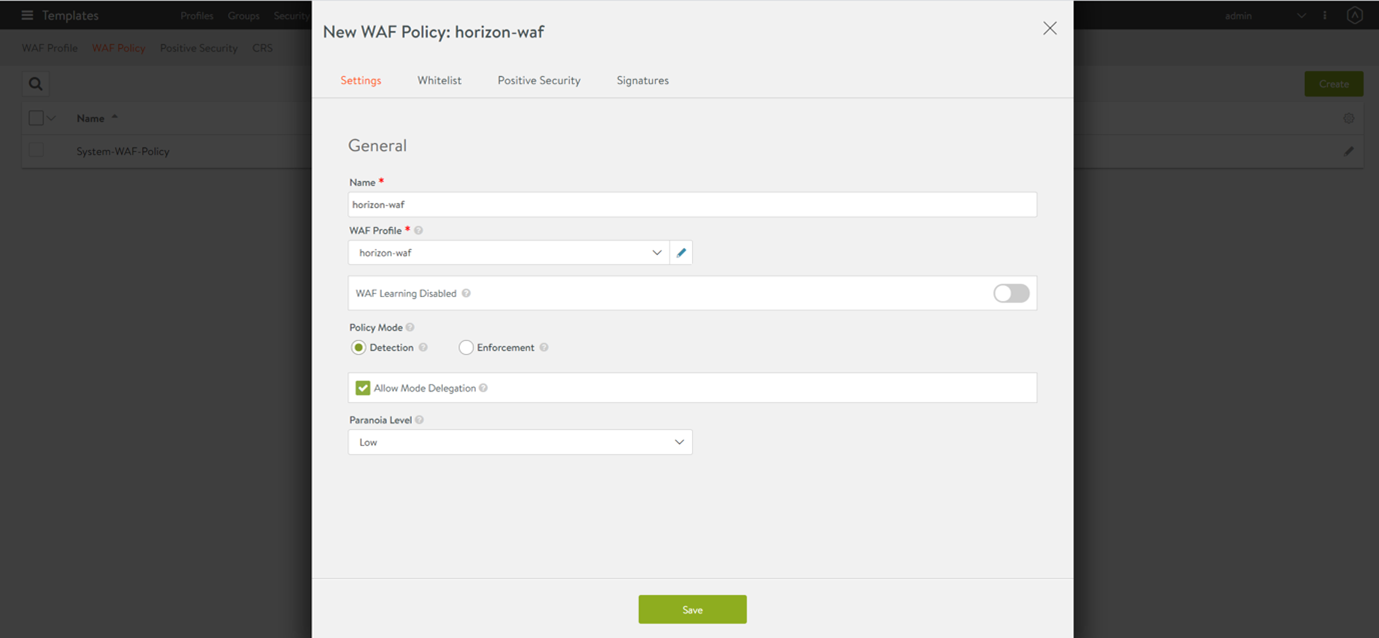
Create the WAF Policy.
- Navigate to Template > WAF > WAF Policy. Select the WAF profile created in the previous step. The default profile can be used too.
- Add an allowlist rule
-
This allowlist makes sure WAF does not block the request having URI which contains /ice/tunnel. This is a mandatory step.
Select the Allowlist tab and click on Add Rule.
Provide the following attributes:
To allow all URIs beginning with /ice, create the rule as shown below:
Similarly, you can create another allowlist rule for /ice/reconnect.
To add pre-CRS rule, click Save and click on Signatures > Add PRE-CRS Rules as shown below:
-
-
Associating with the required virtual service Once the WAF profile is ready, navigate to Application > Virtual Service. Select the required L7 virtual service and associate the WAF policy created in the previous step as shown below:
Load Balancing Connection Server
Both L4 and L7 virtual services are supported to load balance traffic to connection servers. However, it is recommended to use L7 virtual services.
To know how to use L7 virtual service to load balance traffic to connection servers, refer to Load Balancing Traffic to Connection Servers.