SAML Authentication for Single Sign-On
Starting with release 17.2.4, Avi Vantage supports single sign-on (SSO) to the Avi Controller’s UI using Security Assertion Markup Language (SAML). SAML is an XML-based markup language for exchanging authentication and authorization between an identity provider (IdP) and a service provider(SP).
Avi has verified interoperability with the Google, Okta and OneLogin IdPs. Contact your Avi sales team if you require integration with other IdPs.
Configuring SSO with SAML via the Avi UI
SAML settings can be configured in the authentication profile. Navigate to Templates > Security > Auth Profile. Enter a name for the profile and select SAML as Type.
Settings
Any node acting as a service provider must generate a metadata file for registration with the IdP. The file contains configuration and integration details for SAML single sign-on. Obtain the metadate file from your identity provider.
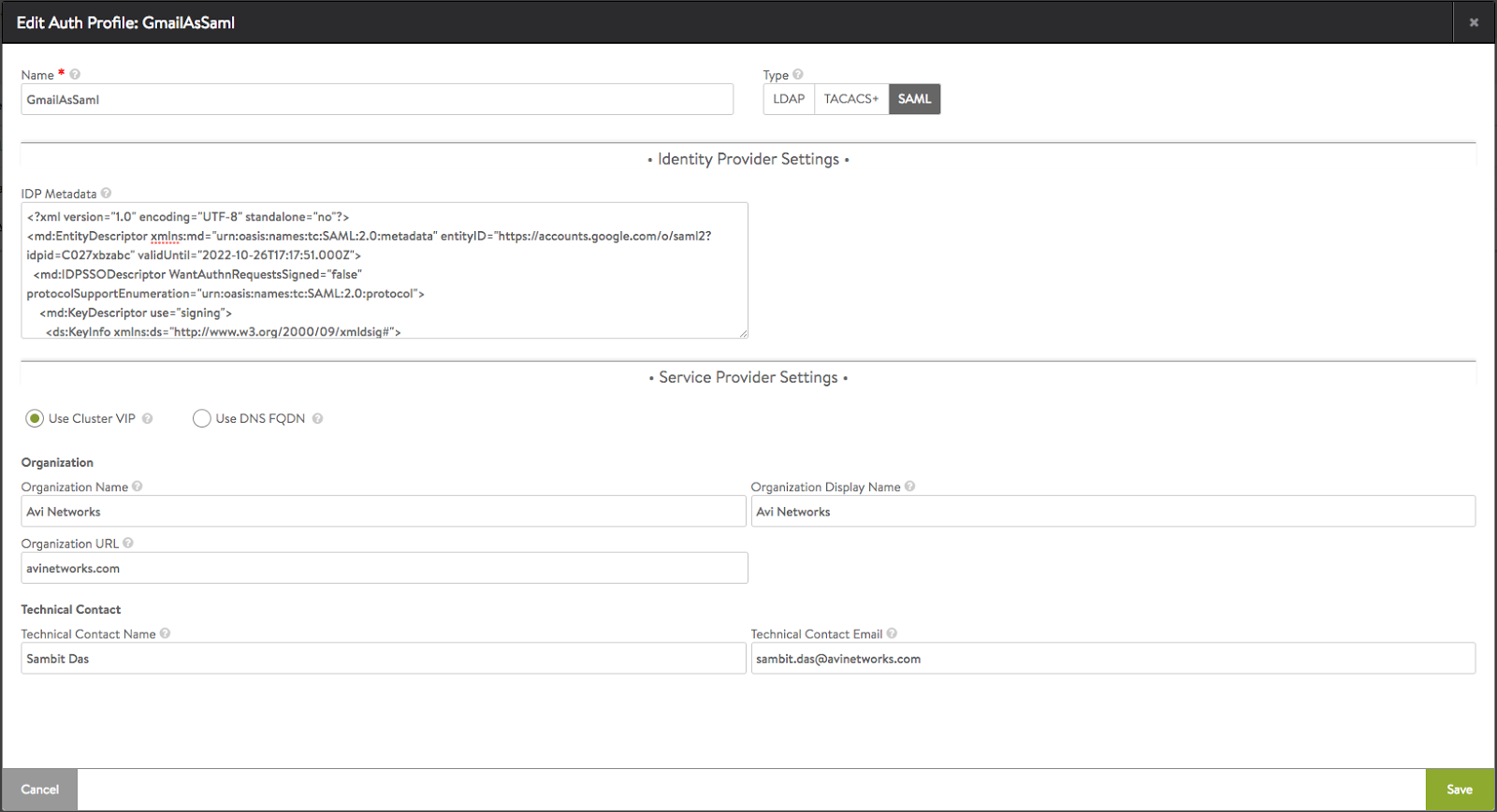
Figure 1. Authentication profile editor
Service provider metadata contains keys, services and URLs defining SAML endpoints of the Avi Controller. The Avi Controller can be registered using its cluster IP or a DNS-resolvable FQDN. If “Use Cluster IP” is selected, then the cluster IP is picked up automatically. If “Use DNS FQDN” is chosen, the user will be prompted to provide an FQDN.
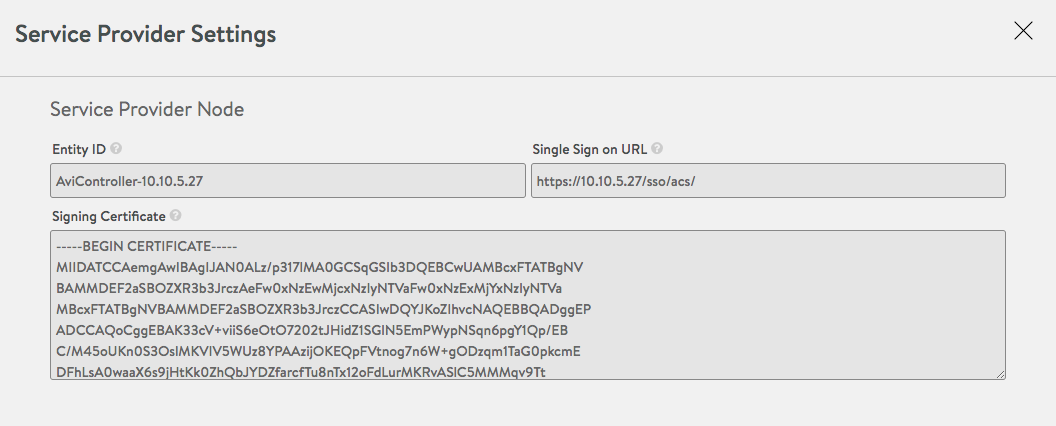
Figure 2. Service provider settings
Service provider settings can be retrieved by clicking on the ? button on the list page. This page contains the service provider entity-ID and the single sign-on URL generated by the Avi Controller. The signing certificate is a self-signed certificate with common name set to the entity-id. This certificate is used by the IdP for encrypting the assertion response.
Create Application on the IdP
A SAML application needs to be created on the IdP using this Controller-generated information. The entity-ID and the single sign-on URL required while creating the application on IdP needs to precisely match the Avi-generated configuration.
In the case of certain identity providers, IdP metadata can be retrieved after the SAML application has been created. In those cases, the recommended workflow is to create a SAML authentication profile on Avi Vantage without IdP metadata and then use the Avi-generated attributes to create the SAML application. Once the application has been created, the IdP metadata can be plugged into the authentication profile. The authentication profile cannot be attached to the system configuration without valid IdP metadata.
Note: Starting with Avi Vantage version 20.1.1, both SAML assertion and response signing are mandatory for successful SAML authentication.
Local Admin or User Logon
After SAML-based access is enabled, you may occasionally want to have the Avi Vantage web console display the logon UI without redirecting to the SAML authentication profile configured on the IdP logon page. To do so, send the Controller or cluster IP address a URL which takes on one of the following two forms:
https://ControllerIP/#!/login?local=1https://FQDN/#!/login?local=1
