Configuring SAML Authorization Policies
Overview
Authorization is the process to control the access provided to the users. With authorization policies, you can indicate if the authenticated user is permitted to have access to a resource or not.
For instance, on a protected resource, such as, saml.acme.com, you can restrict the access to users to use same.acme.com/admin page.
Starting with Avi Vantage version 20.1.1, SAML authorization policies are supported.
The following section discusses configuring authorization policy with corresponding rules and action.
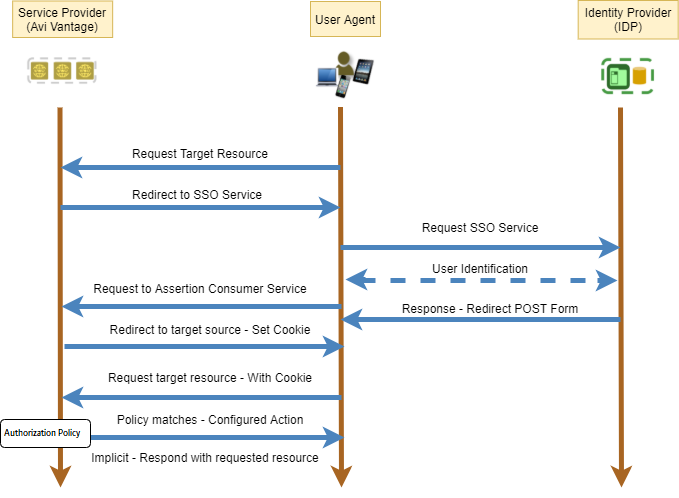
SAML Authorization Policies
The diagrammatic representation of SAML authorization flow is as follows:
SAML Authorization Rules
The SAML authorization supports the following match types:
| Match Type | Description |
|---|---|
| Attribute | The attributes that are part of SAML response from IDP |
| Path | URI Path |
| Host Header | Host header that is present in incoming request |
| Method | HTTP request method, for instance, GET, POST etc. |
Note: Host header and path can be configured to be case sensitive aware.
The SAML authorization supports the following action types:
| Action Type | Description |
|---|---|
| allow_access | Allow access on authorization policy rule match |
| close_connection | Close connection on authorization policy rule match |
| http_local_response | Send HTTP local response on authorization policy rule match |
Example:
Assume the following scenario:
- The aviadmin path should be allowed only for a user with an email(attribute), say, admin@acme.com.
- Only GET requests are allowed for this path.
- Requests carrying host-header admin.acme.com are only allowed to access this path.
If all the above conditions are met, then only the access should be allowed. Else, the 403 response code should be returned to the user.
For the above scenario, the authorization policy configuration will be as follows:
+------------------------------+------------------------------------------------+
| Field | Value |
+------------------------------+------------------------------------------------+
| uuid | ssopolicy-86fb0825-8d1f-45f4-a56b-f8bf8adf9a46 |
| name | sso1 |
| authentication_policy | |
| default_auth_profile_ref | saml-idp-authz |
| authorization_policy | |
| authz_rules[1] | |
| name | Demo_rule |
| index | 1 |
| enable | True |
| match | |
| attr_matches[1] | |
| attribute_name | email |
| attribute_value_list | |
| match_criteria | EQUALS |
| match_str[1] | admin@acme.com |
| path | |
| match_criteria | EQUALS |
| match_case | INSENSITIVE |
| match_str[1] | /aviadmin |
| host_hdr | |
| match_criteria | HDR_EQUALS |
| match_case | INSENSITIVE |
| value[1] | admin.acme.com |
| method | |
| match_criteria | IS_IN |
| methods[1] | HTTP_METHOD_GET |
| action | |
| type | ALLOW_ACCESS |
| status_code | HTTP_RESPONSE_STATUS_CODE_403 |
| authz_rules[2] | |
| name | Deny_rule |
| index | 2 |
| enable | True |
| match | |
| path | |
| match_criteria | EQUALS |
| match_case | INSENSITIVE |
| match_str[1] | /aviadmin |
| action | |
| type | HTTP_LOCAL_RESPONSE |
| status_code | HTTP_RESPONSE_STATUS_CODE_403 |
| type | SSO_TYPE_SAML |
| tenant_ref | admin |
+------------------------------+------------------------------------------------+
Here the rule name Demo_rule will be hit only if all the criteria are met and will be provided an access.
If any of the criteria is not met in Demo_rule, then Deny_rule will be hit, and access will be denied.
You need to explicitly define the action in a rule (Deny_rule in this case), else it will be implicitly permitted.
Notes:
-
If there are multiple conditions within a single rule then it is AND match. If there are multiple rules then it is a OR match i.e., if multiple rules are configured and if one of the rules matches, then the action will be executed. The order of rule check depends on index of rule.
-
The status_code has a default value of
HTTP_RESPONSE_STATUS_CODE_403and it will be honored only when the action is local response. For other actions like close connection or allow access, the status code will be ignored.
Configuring Authorization Policy with Corresponding Rules and Actions
This section explains the different kind of matches in example formats. You can choose one criterion or more based on the use case or requirement.
The following are the steps to configure SAML authorization policies:
-
You can attach the authorization profile to the authentication policy which contains the IDP metadata. For instance, configured authorization profile is
saml-idp-authz.
For more details on the authentication profile, refer to SAML Configuration on Avi Vantage user guide.[admin:controller]: > configure ssopolicy ssopolicy1 [admin:controller]: ssopolicy> authentication_policy default_auth_profile_ref saml-idp-authz [admin:controller]: ssopolicy:authentication_policy> save - You can navigate to authorization policy mode.
[admin: controller]: ssopolicy> authorization_policy -
You can configure the multiple authorization rules ordered by the index under authorization policy. The following is an example of configuration of authorization rule of name rule1.
[admin:controller]: ssopolicy:authorization_policy> authz_rules name rule1 New object being created [admin:controller]: ssopolicy:authorization_policy:authz_rules> - You can choose the match criteria for authorization policy as described in match table above. In the following example,
attr_matchesattribute is used as match criteria.
attr_matches[admin:controller]: ssopolicy:authorization_policy:authz_rules> match [admin:controller]: ssopolicy:authorization_policy:authz_rules:match> attr_matches New object being created [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> attribute_name Attribute name whose values will be looked up in the access lists. attribute_value_list (submode)The attributes or values in the SAML assertion responses are matched through attribute matches against the configured attributes and its values.
The SAML assertion attributes can have zero or more values associated with each of them. You can configure multiple attributes and values as part of each rule. The rule is matched only if all the attributes are matched.
The matches can be either positive or negative.
-
Positive Match — BEGINS_WITH, CONTAINS, ENDS_WITH, EQUALS, REGEX_MATCH
-
Negative Match — DOES_NOT_BEGIN_WITH, DOES_NOT_CONTAIN, DOES_NOT_END_WITH, DOES_NOT_EQUAL, REGEX_DOES_NOT_MATCH
Positive attribute match rules are matched if the attribute is present in the assertion response and one of the values of the corresponding attribute matches with the configured value list.
Negative attribute match rules are matched if the attribute is not present or all the values of the corresponding attribute negatively matches with the configured value list.
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> attribute_name email [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> attribute_value_list [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches:attribute_value_list> match_str abc@xyz.com [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches:attribute_value_list> [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches:attribute_value_list> match_criteria begins_with [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches:attribute_value_list> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> save admin:controller]: ssopolicy:authorization_policy:authz_rules:match> -
- You can search for multiple attributes in the same rule. You can configure multiple attribute matches under a single rule as follows:
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> attr_matches New object being created [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> attribute_name firstname [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> attribute_value_list match_criteria equals match_str abc [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches:attribute_value_list> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:attr_matches> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match> - Based on the above details, the configuration will be as follows:
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> where Tenant: admin Cloud: Default-Cloud +------------------------+-------------+ | Field | Value | +------------------------+-------------+ | attr_matches[1] | | | attribute_name | email | | attribute_value_list | | | match_criteria | BEGINS_WITH | | match_str[1] | abc@xyz.com | | attr_matches[2] | | | attribute_name | firstname | | attribute_value_list | | | match_criteria | EQUALS | | match_str[1] | abc | +------------------------+-------------+Host Header
-
You can add more conditions to be matched in the same rule, for instance, you can add another condition to match host header.
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> host_hdr [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> match_criteria hdr_ hdr_begins_with header value begins with the configure value(s) hdr_contains header value contains configured value(s) hdr_does_not_begin_with header value does not begins with the configure value(s) hdr_does_not_contain header value does not contains configured value(s) hdr_does_not_end_with header value does not ends with the configured value(s) hdr_does_not_equal header value does not equals the configured value(s) hdr_does_not_exist header does not exist in the HTTP request hdr_ends_with header value ends with the configured value(s) hdr_equals header value equals the configured value(s) hdr_exists header exists in the HTTP request [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> match_criteria hdr_begins_with [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> value abc.xyz.com [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:host_hdr> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match>Http Methods
-
Add another condition, if required, based on HTTP methods as follows:
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> method [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:method> match_criteria is_in [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:method> methods http_method_ http_method_connect HTTP connect method http_method_copy HTTP COPY method http_method_delete HTTP delete method http_method_get HTTP get method http_method_head HTTP head method http_method_lock HTTP LOCK method http_method_mkcol HTTP MKCOL method http_method_move HTTP MOVE method http_method_options HTTP options method http_method_patch HTTP PATCH method http_method_post HTTP post method http_method_propfind HTTP PROPFIND method http_method_proppatch HTTP PROPPATCH method http_method_put HTTP put method http_method_trace HTTP trace method http_method_unlock HTTP UNLOCK method [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:method> methods http_method_get [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:method> savePath
-
Match the path match based on the string group or list of the string values of the path. This is case sensitive and supports the following list of matching operations:
[admin:controller]: ssopolicy:authorization_policy:authz_rules:match> path [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> match_criteria begins_with [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> string_group_refs System-Cacheable-Resource-Types [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> match_str /acme [admin:controller]: ssopolicy:authorization_policy:authz_rules:match:path> save [admin:controller]: ssopolicy:authorization_policy:authz_rules:match> save [admin:controller]: ssopolicy:authorization_policy:authz_rules>
Configuring Action
You can configure any action as mentioned in the table above. In the following example, you can use http status code, such as http_local
_response to send 403-response to the user.
[admin:controller]: ssopolicy:authorization_policy:authz_rules> action
[admin:controller]: ssopolicy:authorization_policy:authz_rules:action>
status_code HTTP status code to use for local response when a policy rule is matched.
type Defines the action taken when an authorization policy rule is matched.By default, access is allowed to the requested resource.
watch Watch a given show command
where Display the in-progress object
[admin:controller]: ssopolicy:authorization_policy:authz_rules:action> type http_local_response
[admin:controller]: ssopolicy:authorization_policy:authz_rules:action> status_code http_response_status_code_403
[admin:controller]: ssopolicy:authorization_policy:authz_rules:action> save
[admin:controller]: ssopolicy:authorization_policy:authz_rules> index 1
[admin:controller]: ssopolicy:authorization_policy:authz_rules> save
[admin:controller]: ssopolicy:authorization_policy> save
[admin:controller]: ssopolicy> save The following is the SSO policy configuration based on the above-mentioned configuration steps:
+------------------------------+------------------------------------------------+
| Field | Value |
+------------------------------+------------------------------------------------+
| uuid | ssopolicy-16fc1b04-f635-439b-97a4-a3890dead864 |
| name | ssopolicy1 |
| authentication_policy | |
| default_auth_profile_ref | saml-idp-authz |
| authorization_policy | |
| authz_rules[1] | |
| name | rule1 |
| index | 1 |
| enable | True |
| match | |
| attr_matches[1] | |
| attribute_name | email |
| attribute_value_list | |
| match_criteria | BEGINS_WITH |
| match_str[1] | abc@xyz.com |
| attr_matches[2] | |
| attribute_name | firstname |
| attribute_value_list | |
| match_criteria | EQUALS |
| match_str[1] | abc |
| path | |
| match_criteria | BEGINS_WITH |
| match_case | INSENSITIVE |
| match_str[1] | /acme |
| string_group_refs[1] | System-Cacheable-Resource-Types |
| host_hdr | |
| match_criteria | HDR_BEGINS_WITH |
| match_case | INSENSITIVE |
| value[1] | abc.xyz.com |
| method | |
| match_criteria | IS_IN |
| methods[1] | HTTP_METHOD_GET |
| action | |
| type | HTTP_LOCAL_RESPONSE |
| status_code | HTTP_RESPONSE_STATUS_CODE_403 |
| type | SSO_TYPE_SAML |
| tenant_ref | admin |
+------------------------------+------------------------------------------------+